At the beginning of October 2017, citizens of Catalonia – an autonomous community in Spain - held an independence referendum. This call for independence created a conflict between the Catalan leadership and Spanish government and increased law enforcement presence in Catalonia. As a result, the hacktivist group Anonymous has launched a series of cyber-attacks against Spanish institutions in protest.
Download a Copy Now
Abstract
At the beginning of October 2017, citizens of Catalonia – an autonomous community in Spain - held an independence referendum. This call for independence created a conflict between the Catalan leadership and Spanish government and increased law enforcement presence in Catalonia. As a result, the hacktivist group Anonymous has launched a series of cyber-attacks against Spanish institutions in protest. The Anonymous operation has already seen two waves of attacks with a third lingering as Spanish authorities impose direct rule on Catalonia using Article 155 of the Spanish Constitution. More is expected as the government convoke new elections to the Parliament of Catalonia on December 21 of this year.
 Figure 1: An Anonymous propaganda image for OpFreeCatalonia
Figure 1: An Anonymous propaganda image for OpFreeCatalonia
Background
Ahead of the referendum in Catalonia, Anonymous began building support for Catalonia’s independence in September when they announced Operation Free Catalonia. Ever since, Anonymous has been targeting websites and networks of Spanish institutions, including the Constitutional Court of Spain and other government agencies. A number of other organizations – mainly ISPs, corporations, private businesses and schools - all suffered collateral impact.
Targets
Data Dumps
- sanjavier.es
- uhu.es
- lavozdealmeria.es
- juntadeandalucia.es
- sgic.udc.es
- rac.es
- juntadeandalucia.es
- ayuntamientodeguadarrama.es
- bibdigital.rjb.csic.es
- ua.es
- proteccioncivil.es
- etsii.upv.es
- newsespana.es
- votoaccesible.com
- pagina.jccm.es
- madrid.org
- biblioteca.uca.es
- sscc.es
- aperturas.org
DDoS
- dsn.gob.es
- cni.es
- fomento.gob.es
- mjusticia.gob.es
- telitec.com
- flexinet.es
- internet4spain.com
- linerentalspain.com
- unlimited3gspain.com
- mjusticia.gob.es
- bancamarch.es
- policia.es
- mineco.gob.es
- pp.es
- tribunalconstitucional.es
- casaral.es
Attack Vectors
Web Application Attacks
SQL Injection - This technique takes advantage of poor application coding. When the application inputs are not properly sanitized, it becomes vulnerable. Attackers can modify an application SQL query to gain access to unauthorized data with administrator access, run remote commands on the server, drop or create objects in the database, and more.
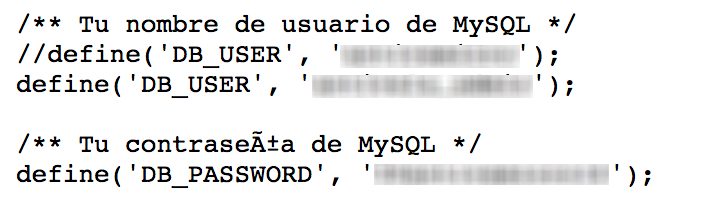 Figure 2: Username and Passwords found in text file
Figure 2: Username and Passwords found in text file
Figures 3 & 4: OpCatalonia staging server – text files contained credentials for targeted sites
Defacement – A website defacement is like digital graffiti. An attacker will change the visual appearance of the website by breaking into a web server and replacing the current website with one of their own. This attack is most commonly associated with SQL Injections. This form of an attack allows administrative access so that the hacker can make the changes required. Another way this is preformed is via FTP if the user’s credentials have been obtained.
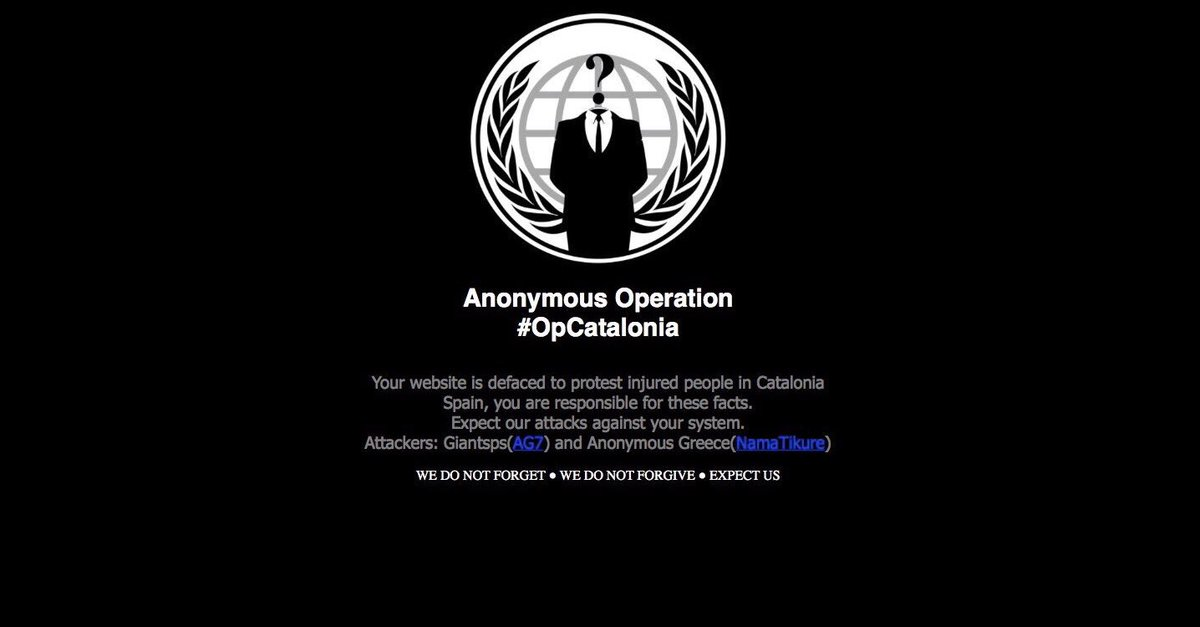 Figure 5: OpCatalonia Defacement
Figure 5: OpCatalonia Defacement
Network-Level DDoS Attacks
TCP flood - One of the oldest, yet still very popular denial-of-service attacks. It involves sending numerous SYN packets to the victim. In many cases, attackers will spoof the SRC IP so the reply (SYN+ACK packet) will not return, thus overwhelming the session/connection tables of the targeted server or one of the network entities on the way (typically the firewall). Servers need to open a state for each SYN packet that arrives and they store this state in tables that have limited size. As big as this table may be, it is easy to send a sufficient amount of SYN packets to fill the table, and once this happens the server starts to drop a new request, including legitimate ones. Similar effects can happen on a firewall which also has to process and invest in each SYN packet. Unlike other TCP or application-level attacks, the attacker does not have to use a real IP. This is perhaps the biggest strength of the attack.
 Figure 6: OpCatalonia Defacement
Figure 6: OpCatalonia Defacement
UDP Flood – In a UDP flood, the attacker sends large UDP packets to a single destination or to random ports. Since the UDP protocol is “connectionless” and does not have any type of handshake mechanism, the main intention of a UDP flood is to saturate the Internet pipe. In most cases, the attackers spoof the SRC (source) IP.
HTTP/S Flood - An attack method used by hackers to attack web servers and applications. These floods consist of seemingly legitimate session-based sets of HTTP GET or POST requests sent to a targeted web server. HTTP floods do not use spoofing, reflective techniques or malformed packets. These requests are specifically designed to consume a significant amount of the server’s resources, and therefore can result in a denial-of-service. Such requests are often sent en masse by means of a botnet, increasing the attack’s overall power. HTTP- and HTTPS-flood attacks are one of the most advanced threats facing web servers today since it is hard for network security devices to distinguish between legitimate and malicious HTTP traffic.
Social Media
Organizations that are concerned may consider following the following attackers on Twitter:
- @AnonPlus_info
- @ANONSPAIN2
- @NamaTikure
- @AnonOpsAL
- @Arm_Legi
Operational Video: https://youtu.be/f4cAkfTYDrA
OpCatalonia live hack video: https://twitter.com/Giantsps/status/923914603821707264
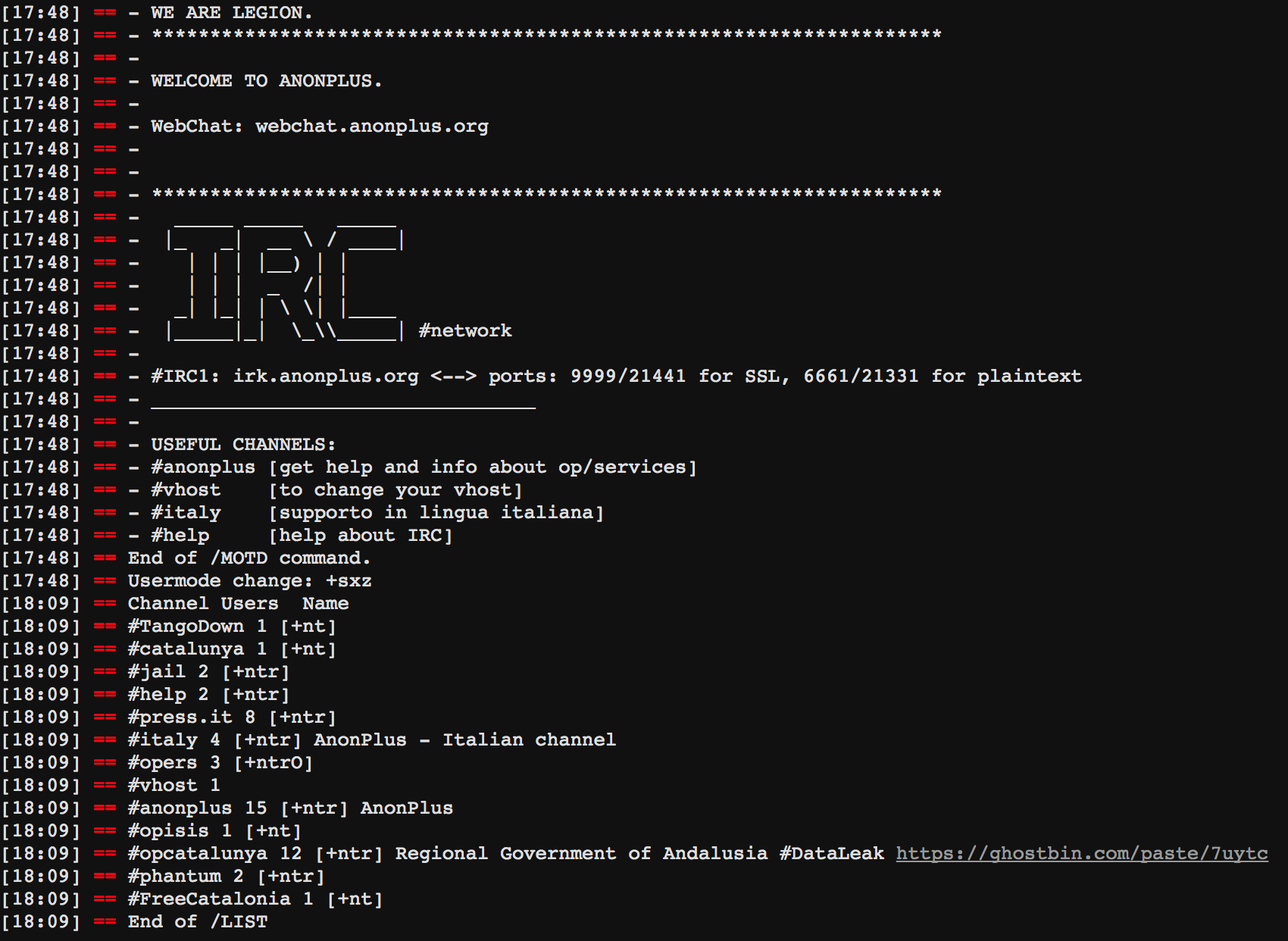 Figure 7: IRC WebChat http://webchat.anonplus.org
Figure 7: IRC WebChat http://webchat.anonplus.org
What's Expected Next
The crisis between the Spanish and the Catalan governments is not going to end soon. This operation is expected to escalate in correlation with the conflict. In the near term, there are unverified reports that the third phase will begin on November 12 following the annual Million Mask March on November 5 by Anonymous, as well as a wave of attacks as the December 21 Catalan Parliament elections approach.
Effective DDoS Protection Essentials
- Hybrid DDoS Protection - On-premise and cloud DDoS protection for real-time DDoS attack prevention that also addresses high volume attacks and protects from pipe saturation
- Behavioral-Based Detection - Quickly and accurately identify and block anomalies while allowing legitimate traffic through
- Real-Time Signature Creation - Promptly protect from unknown threats and zero-day attacks
- A Cyber-Security Emergency Response Plan - A dedicated emergency team of experts who have experience with Internet of Things security and handling IoT outbreaks
For further DDoS protection measures, Radware urges companies to inspect and patch their network in order to defend against risks and threats.
Effective Web Application Security Essentials
- Full OWASP Top-10 coverage against defacements, injections, etc.
- Low false positive rate – using negative and positive security models for maximum accuracy
- Auto policy generation capabilities for the widest coverage with the lowest operational effort
- Bot protection and device fingerprinting capabilities to overcome dynamic IP attacks and achieving improved bot detection and blocking
- Securing APIs by filtering paths, understanding XML and JSON schemas for enforcement, and activity tracking mechanisms to trace bots and guard internal resources
- Flexible deployment options - on-premise, out-of-path, virtual or cloud-based
Under Attack and in Need of Expert Emergency Assistance? Radware Can Help.
Radware offers a DDoS service to help respond to security emergencies, neutralize the risk and better safeguard operations before irreparable damages occur. If you’re under DDoS attack or malware outbreak and in need of emergency assistance,
Contact us with the code "Red Button".