Since June 2018, the Radware Threat Research team has monitored an ongoing APT against the Palestinian authority.
Download a Copy Now
Abstract
Since June 2018, the Radware Threat Research team has monitored an ongoing APT against the Palestinian authority, featuring an updated version of the Micropsia malware with an advanced surveillance toolkit. This advanced persistent threat began in March 2017 and was reported by Cisco Talos and Check Point Software Technologies, infecting hundreds of machines thus far.
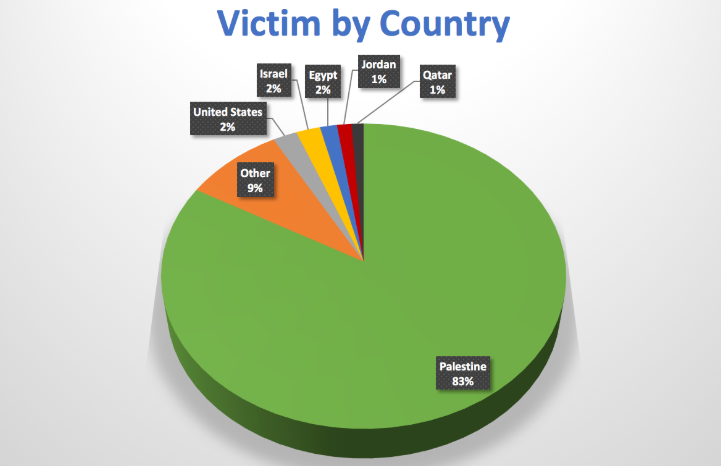
The latest Micropsia malware version analyzed in Radware’s research lab is the most sophisticated tool used by this APT group. It includes advanced surveillance features such as microphone recording, keylogging and document stealing from USB flash drives. It also resembles the old versions’ C2 communication behavior by including references to famous TV shows and characters. While the campaign and victims were selectively targeted, some instances contaminated machines in other countries as well (see below).
Infection Process
Attackers gathered intelligence and used social engineering to select their victims. They have sent spear phishing emails to email addresses of selected personas. The email contains an attached file that looked like a report from a known news agency with a malicious executable downloaded and activated in the background.
Malware Capabilities
Micropsia comes with an impressive arsenal of advanced surveillance features, allowing it to closely track the victim’s activity and control the victim’s operating system. Currently, the following capabilities exist in the analyzed binary:
- Microphone recording
- Document stealing from connected USB flash drives
- Screen capturing
- Keylogging
- Document stealing from hard drive
- Scanning all drives - full directory listing without filters
- Get files by specific path
- Download and execute an arbitrary executable
- Update malware executable
Microphone Recording
The microphone recording capability is considered an advanced surveillance feature, which is a rare occurrence among widespread malware. That said, it might become common when initiating an APT attack. While the malware’s screen capturing and keylogging capabilities are set to ‘on’ by default, the recording feature requires an activation command from the C&C at intervals defined by the operator. Once activated, Micropsia begins recording using Win32 MCI (Media Control Interface), which provides a generic interface to nearly every kind of multimedia device.
Initiating a new recording or stopping a running one is accomplished by calling Winmm.mciSendString API. That controls the multimedia device. Micropsia operators control the recording duration via Delphi timers that allow it to perform a periodic recording. A new recording is initiated by executing the above API using the following string commands.

In the same way, stopping the recording and saving it to a file is achieved by executing the following:

USB Flash Drives for Document Stealing
Controlled by Micropsia operators, the malware is able to register to an event of USB volume insertion to detect new connected USB flash drives. This functionality is detailed in an old blog post. Once an event is triggered, Micropsia executes an RAR tool to recursively archive files based on a predefined list of file extensions (*.xls, *.xlsx, *.csv, *.odt, *.doc, *.docx, *.ppt, *.pptx, *.pdf, *.mdb, *.accdb, *.accde, *.txt).
Screen Capturing and Keylogging
Upon execution, the Micropsia malware takes screenshots every 90 seconds by calling to Gdi32.BitBlt API. This functionality is implemented by a Delphi timer which runs infinitely. Screenshots are saved as unencrypted files in JPEG format with a specific file name that contains the current timestamp (yyyy-mm-dd hh-nn-ss) with the hardcoded extension .his.
The screen capturing function contains incriminating strings which lead us to assume that this code was copied from a snippet published in delphimaster.ru forum. The keylogging module also starts automatically by recording every keystroke using the user32.GetKeyState API. It also deals with clipboard data when malware detects a key press combination of Ctrl+C. This module writes its output to a log file that also contains the current timestamp (yyyy-mm-dd hh-nn-ss) with the extension .slog.
Scan Drive and Fetch Files
Micropsia is able to perform a recursive directory listing on-demand for all volume drives available on the victim’s machine. It checks whether a volume drive exists by simply iterating all possible letters (from A to Z) and testing whether this directory exists. Malware operators are also able to fetch specific files from victim file system by their path.
Storage Management
Most of the malware capabilities mentioned above have outputs written to the file system which are later uploaded to the C2 server. Each module writes its own output in a different format, but surprisingly in a non-compressed and non-encrypted fashion. Micropsia’s developers decided to solve these issues by implementing an archiver component that executes the WinRAR tool. The malware first looks for an already installed WinRAR tool on the victim’s machine, searching in specific locations.
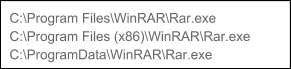
In the event a WinRAR tool is not found, Micropsia drops the RAR tool found in its Windows Portable Executable (PE) resource section to the file system.