October 7 anniversaries have become focal points for pro-Palestinian hacktivist messaging and calls for coordinated attack campaigns such as DDoS, data leaks and defacements.
Download now
Key Attack Insights:
- Israel’s retaliation following the October 7, 2023, Hamas attack sparked an unprecedented wave of DDoS activity led by pro-Palestinian hacktivists, marking a significant escalation in the hacktivist landscape.
- SYLHET GANG recently posted a call to action referencing “7 October” and urged for a coordinated action timed to that date.
- The SYLHET GANG channel functions primarily as a propaganda amplifier and mainly forwards partner claims and alliance announcements rather than publishing independent technical proof of attack activity.
October 7 anniversaries have become focal points for pro-Palestinian hacktivist messaging and calls for coordinated attack campaigns such as DDoS, data leaks and defacements. Ideologically driven actors use the symbolic date to mount publicity-focused campaigns aimed at increasing their visibility in the media and the wider hacktivist community. Given that hacktivist activity often combines low-cost disruptive techniques with high-volume social amplification, defenders should anticipate temporal spikes in website defacement, data leak and DDoS attack claims around the anniversary window.
SYLHET GANG Profile
SYLHET GANG operates primarily via Telegram channels where the group publishes original posts and forwards posts from allied groups to amplify them. The original messages in the Telegram channel are mostly announcements of new alliances, forwarded attack claims from partners and calls to action for coordinated operations. This pattern suggests that the channel plays both a coordination and recruitment role as well as a propaganda and amplification role in the wider hacktivist ecosystem. The channel posts in English, Russian and Arabic languages and repeatedly republishes links to external file hosts and attack proof pages, increasing cross-regional reach and the likelihood that a single claim cascades across many communities.
The Threat
SYLHET GANG explicitly called for coordinated action related to October 7 through a short message in its channel reading “7 October Soon / Timeout has started / We will be the first to attack IN SHA ALLAH…,” making a clear intent to time activity to the anniversary.
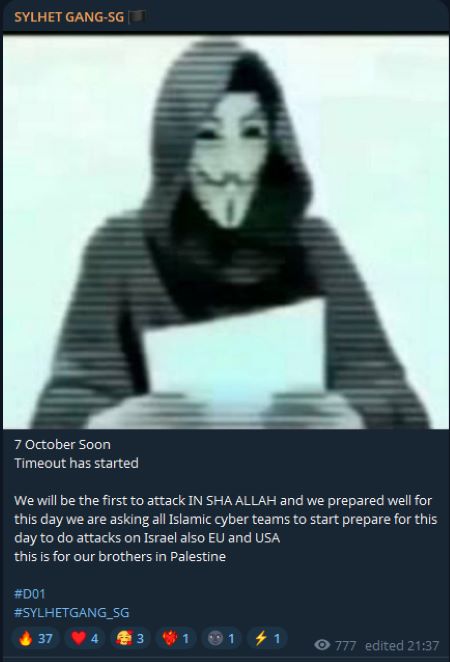
Figure 1: SYLHET GANG-SG's call to action on October 7, dated Oct 1, 2025 (source: Telegram)
Although the channel contains mainly forwards of other channels, the group’s public call to action and pattern of amplifying alleged proof materially raises the near-term risk of potentially disruptive coordinated DDoS attack waves, opportunistic web defacements and propagation of alleged data leaks by allied groups.
Collaborators
SYLHET’s channel operates inside a network of allied channels whose forwards and alliance messaging broadens their reach and increases their potential of initiating campaigns amongst allies. KaliHunt’s messages, for example, are repeatedly forwarded and SYLHET helped them to become more visible inside the community.
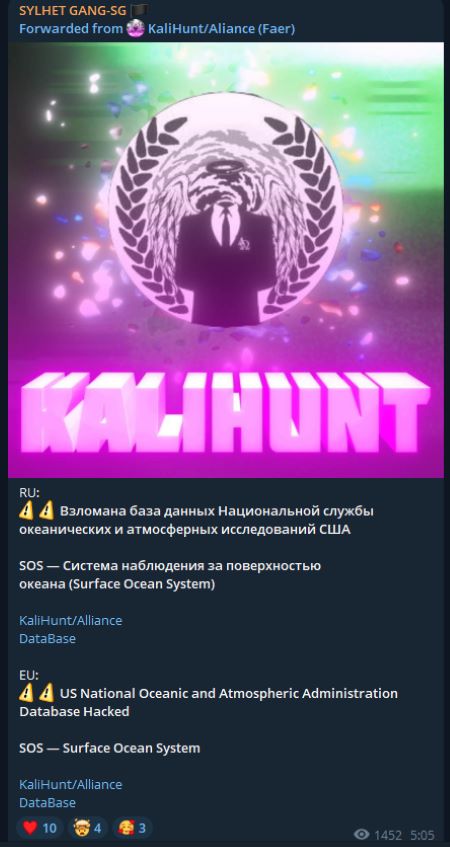
Figure 2: Message from KaliHunt forwarded by SYLHET GANG SG, dated Oct 24, 2024 (source: Telegram)
SYLHET also announced AnonSec PS in an official alliance statement, indicating the intentional mutual amplification rather than a few casual mentions.

Figure 3: Official alliance statement by SYLHET GANG and AnonSec, dated April 5, 2025 (source: Telegram)
DieNet and NoName057(16) are other regularly forwarded groups, increasing the reach of pro-Russian aligned messages across pro-Palestinian channels. NoName057(16) was also mentioned in the “7 October” framing of last year, underscoring the cross-ideological and global nature of the threat.
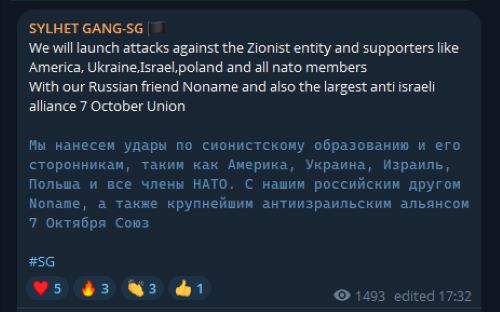
Figure 4: Message from SYLHET GANG referencing NoName, dated July 8, 2024 (source: Telegram)
Taken together, these alliance announcements and forwarding behaviors create a credible amplification pathway. The scale of a potential disruptive event will depend less on SYLHET’s technical capability, but more the speed of cross-channel propagation and how many allied groups pick up the call to leverage their mutual capabilities. This dynamic can result in multiple DDoS attack waves, coordinated defacements and an overwhelming cascade of social claims that could strain organizations’ SOC, IR and communications resources.
Reasons for Concern
- Anniversary timing: Explicit calls tied to October 7 raise the likelihood of coordinated time-bound activity.
- Networked amplification: Alliance announcements and frequent forwards allow a single claim to be spread quickly across multiple communities and languages, multiplying its reach and potential pressure on targets.
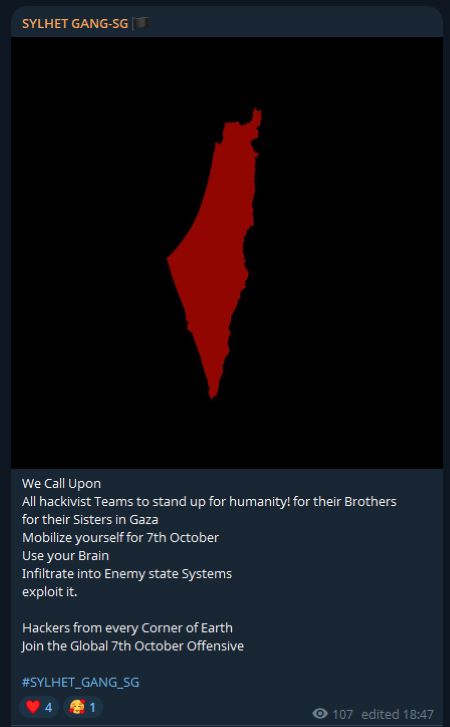
Figure 5: A message from the SYLHET GANG Telegram channel, dated October 5, 2025 (source: Telegram)
- Low barrier attacks: DDoS and web-layer nuisance attacks are cheap, scalable and hard to fully prevent without proper mitigation solutions in place. These attacks can cause service disruption, customer impact and negative media attention.