It’s probably not news that the amount and frequency of cyber-attacks are rising precipitously. And one type of attack, the Web DDoS Tsunami, represents a notoriously large component of this growth. At Radware, we see and live this every day. Here’s the great news — our customers are protected against them by our Cloud WAF and DDoS Protection solutions.
It’s inaccurate to suggest that any DDoS attack is easy to combat, but definitely easier to argue that the new generation of HTTPS Floods are extremely difficult to detect and mitigate. Since HTTPS Floods have been around for a few years, they are sometimes considered “old news”. Consider this, though — the volume and intensity of HTTPS Floods are up dramatically, and the level of sophistication introduced by attackers is growing fast and viciously. We strongly believe that the "old" HTTP/S Floods are turning into Web DDoS Tsunamis. And, of course, a tsunami is something everyone should be prepared for ahead of time and have the proper protection in place.
It’s now a much bigger threat than most IT professionals realize.
What Can Be Categorized as a Web DDoS Tsunami Attack?
To understand Web DDoS Tsunami attacks — and HTTP Flood attacks in general — it helps to first understand the 4 ways in which these attacks can be categorized: attack volume, attack duration, characterization of the botnet used by the attackers and how attack transactions are crafted to look like legitimate requests.
In this blog — the first of two on the subject — we’ll take a look at Attack Volume and Attack Duration.
Attack Volume
In just the past few months there have been several million RPS (requests per second) HTTPS Flood attacks observed and publicized by various 3rd party organizations. At Radware, we have also experienced such million-RPS attacks targeting our customers. A number of these huge, observed attacks even reached upwards of tens of million RPS. Correspondingly, several record-breaking attacks were recently disclosed by public cloud vendors. No doubt we are in the era when HTTPS Flood attacks are turning into Web DDoS Tsunamis. Of course, these mega-RPS attack levels represent extreme HTTPS Floods, but keep in mind that the number of very high-volume RPS attacks is high and keeps growing. Just last year, several studies demonstrated that 95% of HTTPS Floods clocked in at under 150k RPS (the 99% percentile can reach more than 500k RPS). Over just the last few months, there has been a steep rise in the average RPS rate. Numerous attacks reached hundreds of thousands, even millions, RPS. We can say with reasonable confidence that almost all web applications, web services or any other online assets on Earth can be targeted by this wave of massive volume Web DDoS Tsunamis! The need for Web DDoS Tsunami protection is truly a “must have" need of our industry.
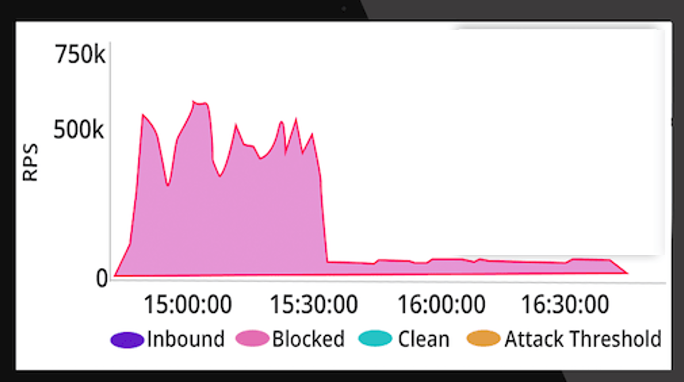
Figure 1: Real-life Web Tsunami example that Radware successfully mitigated for our customer, who was targeted. The attack was in excess of 500k RPS and lasted over an hour.
This rise in Web DDoS Tsunamis greatly impacts not just online asset owners, but also WAF and DDoS Protection solution vendors. They have the added responsibility of protecting both their customers’ online assets and their own infrastructure from these sophisticated, high-RPS DDoS attacks. Each WAF and DDoS protection provider must ensure that if several tenants share the same infrastructure and there’s an attack on one tenant, there’s probably an attack on another. On top of that, application layer (L7) infrastructures, because they are more complicated and expensive to build and manage, are way more complex and expensive when it comes to mitigating Web DDoS Tsunamis than those of their more traditional network layer (L3) counterparts.
Building Web Tsunami attack detection and mitigation services requires special care, expertise and large investments in the proper infrastructure. The objective is to eliminate the protection infrastructure from being overwhelmed and saturated by the attack’s massive volume of traffic before getting to actual customer protection. Only high-capacity L7 entities (web proxies, and others), along with highly architected and ruggedized protection infrastructures, can successfully face such ridiculous attack volumes. Only highly skilled and experienced vendors in both DDoS and L7 AppSec protection can satisfy the L7 infrastructure and attack mitigation requirements generated by this new era of Web DDoS Tsunamis.
Attack Duration
A Web DDoS Tsunami can last anywhere from a few seconds to hours, even several days. It’s a broad timeframe. While some of the infamous ultra-high RPS (millions) attacks generally last less than a minute, other recent Web DDoS Tsunami attacks have lasted for several minutes or many hours. At Radware, we have also experienced tsunami attacks on our protected customers that lasted more than a day.
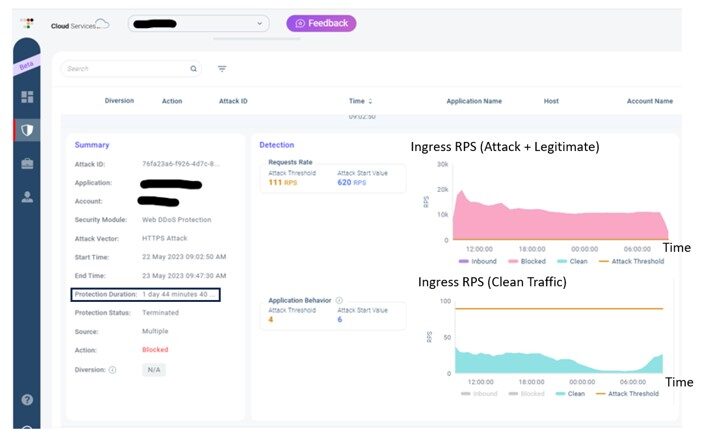
Figure 2 (image blurred to protect customer’s identity): Real-life Web Tsunami attack example against one of Radware’s customers. The attack lasted for over a day and didn’t stop. Throughout this 25-hour attack, more than one billion attack requests were successfully mitigated by Radware’s Web DDoS service. This image is taken from the Radware WEB DDoS service portal.
Duration aside, there is also a very steep rise in tsunami volume. In many cases, the attack bursts in a flash to "full power" in less than 10 seconds, then stayed there. One can only imagine an unprotected website during high traffic times suddenly jumping to 500k or a million RPS in less than 10 seconds. The results are obvious; the site will go down and be unresponsive to legitimate users, who stay frustrated for hours or simply move to another provider to obtain the services they need.
There are also attacks that last for a few seconds. Many wonder about the motivation behind these abbreviated attacks. It’s up for debate, but a common assumption is that short, aggressive attacks are used to demonstrate what the attacker is capable of accomplishing. Attackers are using Telegram (or other media channels) to showcase their ability to launch devastating attacks by displaying that the victim’s application is down and unresponsive within seconds after they’ve launched a tsunami attack. In some other cases, short attacks can be a "ransom threat message". It’s their way of showing the potential victim that "this is what we can do if you will not pay the ransom we asked for.” It’s a scare tactic indeed.
Again, protecting against such brutal tsunami attacks is not an easy and straightforward task. It requires a high degree of DDoS and AppSec protection expertise. Every Web DDoS Tsunami protection infrastructure must be able to cope with and absorb an ultra-steep increase in the incoming load, be ready to hold this volume for a diverse period of time and do it all in an efficient and cost-effective way. And this needs to be done while keeping customers’ online assets safely up and running.
Next Up — Part 2 of 4 Ways To Categorize Web DDoS Tsunami Attacks
Next week, we’ll publish the second and final blog in this series, which will cover the last 2 ways to categorize Web DDoS Tsunami Attacks — the characterization of the botnet used by attackers and how the sophisticated, legitimate-looking attack transactions are created.
Protecting against these attacks is just one of an array of reasons so many organizations rely on Radware. If you would like to speak with a talented and tenured Radware security professional, you can reach them HERE. They would love to hear from you. Protection from the latest disruptive Web DDoS Tsunami attacks and other cyberattacks is just a click away.
To learn why Radware was named a leader in DDoS mitigation by SPARK Matrix, you can read the complete analyst report HERE.