4 Ways To Categorize Web DDoS Tsunami Attacks — Part 2
In Part 1 of 4 Ways to Categorize Web DDoS Tsunami Attacks, I covered the first two ways they can be categorized — Attack Volume and Attack Duration. The following will cover the next two ways to categorize Web DDoS Tsunami Attacks — the characteristics of the botnet used and the attack transactions.
Characteristics of the Botnet Used
There is an array of dimensions that can be used to characterize botnets launching Web DDoS Tsunamis floods. The following are dimensions relevant primarily for attack detection and mitigation. Other dimensions (like botnet owners’ political or religious affiliation, financial motivation, extortion, and more) that are less relevant regarding attack detection are discussed in other Radware posts and blogs.
First, we should consider the size of the botnet. It’s characterized by the number of unique IPs from which the attack’s web transactions originate. The number of attacker IPs used can typically range from thousands to hundreds of thousands. IPs can be distributed geographically across the globe or assigned to numerous autonomous system numbers (ASNs), which are typically owned by service providers and identify networks that exist on the internet. As a result, during Web DDoS Tsunamis each of the attacker’s IPs can generate similar, higher or lower RPS levels, as do legitimate clients on average (This is when compared to legitimate clients’ average RPS during peacetime). Consequently, treating top talker IPs (i.e., client IPs with the highest RPS received in a timeframe) as the attackers as a mitigation technique — including providing other, traditional mitigation approaches like rate-limiting source IPs with high RPS levels — can potentially yield an unwanted level of false positive. This can potentially harm the availability of the protected service and the resultant frustration — which was the attacker’s original objective — will have been fulfilled. In some real-life cases we have seen in Radware, attackers generate Web DDoS Tsunami attacks from large-scale botnets, as each individual bot generates very low RPS volumes in order to evade simple approaches used to mitigate such attacks.
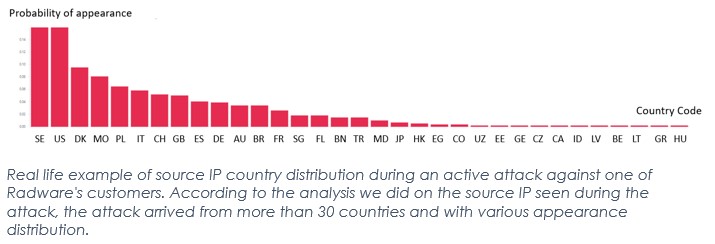
Along with botnet size, Web DDoS Tsunamis can originate from source IPs that are potentially assigned, or owned, by various types of sources. Probably the most common attacks are those in which the attacker’s IPs belong to public proxies, such as an open proxy, an anonymous proxy or an open VPN. This is commonly used by attackers to obfuscate their true identities. In addition, the attacker’s IP can belong to legitimate residential subscribers (i.e., home routers belonging to an innocent, unknowing subscriber), cloud provider IPs, web hosting provider IPs and (less common) infected IoT devices. The attackers primarily use these various types of IPs to obfuscate themselves from being identified and simply blocked (and potentially arrested by country-based law enforcement authorities). As a result, an attack won’t be detected and mitigated if threat intelligence information is used merely to mitigate it based on IP address affiliation. It may help, however, for mitigating attacks coming from an incriminated anonymous proxy. However, it won’t help in cases when the attack arrives from legitimate, residential IPs, which are the legitimate clients of most online services. Building a mitigation strategy based solely on IP address intelligence can potentially yield an unwanted level of false negatives. IP reputation can help fight — but not fight on its own — against these next generation tsunami attacks.
Tsunami attacks coming concurrently from several orchestrated botnets is also a reality. In order to build a tsunami-level HTTP attack, different hacker groups sometimes cooperate and attack a single victim at the same time. As a result, multiple types of attacker IP addresses and high volumes of RPS can appear within a single attack. Indeed, this makes it convoluted and challenging to handle.
Attack Transactions
Maybe the most interesting Web DDoS Tsunami Attack category is how the attacker crafts the HTTP transactions generated by their botnet during the onset of the WEB attacks tsunami.
When trying to explore the structure of the web DDoS HTTP request, we once again find a wide spectrum of approaches. Let’s start with a very simple case when a Web DDoS Tsunami is composed from a simple HTTP request. The attack is built from a single transaction that is transmitted, or replicated, in high volume. For example, it can be a simple HTTP GET to the “/” along with a very basic set of HTTP headers, such as Host and Accept. On the one hand, these transactions look legitimate, so it’s not likely that the attack can be mitigated by a traditional WAAF, or by other existing means. On the other hand, mitigation entities might be able to simply block, or filter, this specific single transaction before it is delivered to the protected organization’s online assets. In that case, the attack will be mitigated. However, nowadays Web DDoS Tsunamis are way more sophisticated. The attackers avoid this simple detection and mitigation by building more complex and genuine transactions. Also, they heavily rely on randomization. A wide range of an attack’s transaction structure appears in web tsunami attacks. Attackers craft more realistic and legitimate transactions that contain a set of “legitimate looking” query arguments, more HTTP headers, User Agent and referer headers, web cookies, and more. The attack requests have various HTTP methods (POST, PUT, HEAD, etc.) and direct to a number of paths within the protected application. Many attributes of the transactions generated by the attacker are continuously randomized, sometimes on a single transaction basis. Using this high level of randomization makes simple mitigation impractical. The tsunami DDoS attacks appear as legitimate traffic requests and are constantly randomized. As a result, when aiming to perfect mitigation there is no simple, pre-defined signature or rule-based mechanism to provide attack mitigation because the requests appear legitimate and do not indicate malicious intent.
One of the things that makes these attacks so difficult and confounding to mitigate is that once the encrypted traffic is decrypted, it still looks legitimate. Web DDoS Tsunami attackers leverage large amounts of sophisticated evasion techniques to bypass traditional application protections. To add to the sophistication of these attacks, the attackers change their attack pattern during the attack or use several attack request structures together. And it gets even more complex when attacks are launched by several orchestrated botnets in which several of the attacker’s strategies appear simultaneously. As a result of all these attacker strategies, Web DDoS Tsunami Attacks can contain millions of distinct transactions, all of which appear legitimate. If not treating these attacks as a type of zero-day attack and exclusively using a pre-defined set of filters (based perhaps on past attacks) to mitigate attacks, it can potentially result in high levels of unwanted false negatives in mitigation. Just think of a 3 million RPS attack with 1% false negatives; many online assets will not be able to survive the level of traffic leaking after this non-perfect mitigation.
Here’s Your Best Option to Protect Against Web DDoS Tsunami Attacks
It’s important to understand the 4 ways Web DDoS Tsunami Attacks can be categorized, but more important to know how to protect your organization from them. Don’t put it off. Remember, they are on the rise. To protect against them, organizations need a solution that can quickly adapt in real time to an attack campaign. Remember, standard on-prem or cloud-based DDoS and WAAF solutions can’t do that. These threats are dynamic; they change and evolve. Their frequency can’t be predicted, attack vectors are randomized, source IPs and other parameters change, and their ability to sustain these changes can be maintained over long periods of time. Only behavioral-based algorithms with self-learning and auto-tuning can detect and mitigate these attacks.
That’s why it’s so important to learn how Radware successfully protects our customers from Web DDoS Tsunami Attacks. Our industry-leading application protection products and solutions are developed with one goal in mind — keep customers secure by detecting and stopping attacks before they overwhelm their infrastructure. If you would like to speak with a talented and tenured Radware security professional, you can reach them HERE. They would love to hear from you. Protection from the latest disruptive Web DDoS Tsunami attacks and other cyberattacks is just a click away.
To learn why Radware was named a leader in DDoS mitigation by SPARK Matrix, you can read the complete analyst report HERE.



