Last month, I gave an introduction to the Darknet. In this blog, I’d like to talk specifically about what an attacker can purchase, and at what price. You see, the entry point for cyber attackers keeps dropping as more vendors rush to sell their services on both the Darknet and the Clearnet. Attackers can easily purchase a number of services such as undisclosed exploits and malware to botnets, bulletproof hosting and a number of other attack services. An attacker with limited skill can also purchase full service items that offer setup assistance for botnets and ransomware campaigns. An attacker wishing to purchase attack tools is only limited by their budget, allowing those who can afford it instant access to some of the more sophisticated tools available today.
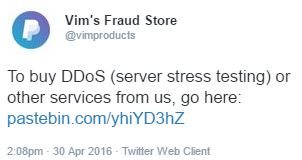
Hardly a day goes by that I don’t see a vendor advertising their services on Twitter or some other form of social media. These advertisements are normally accompanied by a link to either a forum where they are selling their services, or a link to a paste site with additional information about the services they offer and where it can be purchased.
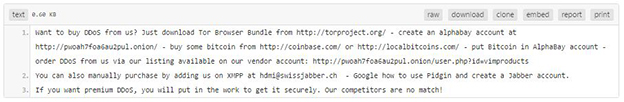
Botnets
Botnet services are commonly found on both the Clearnet and the Darknet. Would-be attackers can purchase anything from tutorials on how to control and deploy their own to the malware itself. If the purchaser does not care to learn about how to deploy their own botnet, they can purchase a setup service or even rent someone’s botnet temporarily. The average rental cost for a large botnet can cost between .025 - .05 BTC per hour and the malware itself can sell for hundreds, sometimes thousands of dollars. Some of the main functions found in these bots include DDoS attack via UDP, TCP, GET and POST floods along with the ability to emulate and bypass some JavaScript and cookie challenges.
[You might also like: 5 Ways Hackers Market Their Products and Services]
DDoS Attacks
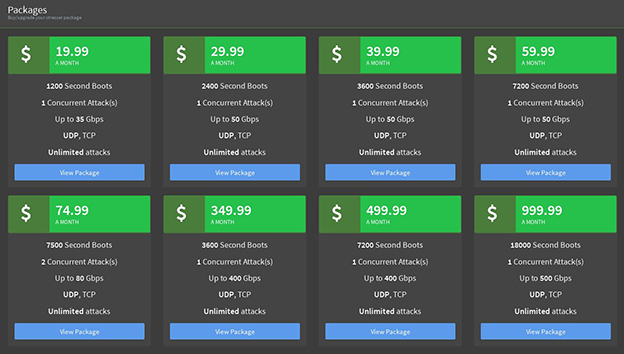
DDoS attacks can be purchased both on the Clearnet or the Darknet though a large majority of the DDoS service can be found on the Clearnet being sold as booter or stresser services. Notorious DDoS groups like Lizard Squad run their own public DDoS services. Lizard Squad’s current service is called Shenron. Shenron offers eight packages ranging from as little as $19.99 to $999.99 a month. Attack times for these packages range from 1,200 to 18,000 seconds of boot time and the power behind the packages on Shenron allegedly range from 35Gbps to 500Gbps. Their services currently offer three different attack methods including DNS, SNMP, and SSYN.
Exploits
Often Darknet marketplaces offer a number of exploit code for sale, like a local privilege escalation on Windows 8.1 or a single message DoS exploit on Telegram. You can also find exploits like a Remote Code Execution (RCE) that allows you to upload your bot to a large amount of vulnerable routers. These exploits can come with a high price tag though. The RCE exploit on the router is currently for selling for $2,500 and the Telegram 0day is selling for close to $5,000. If an attacker is willing to pay these prices, they can easily skip the line and quickly start creating havoc by building their own large botnet and launching attacks against their intended victims.
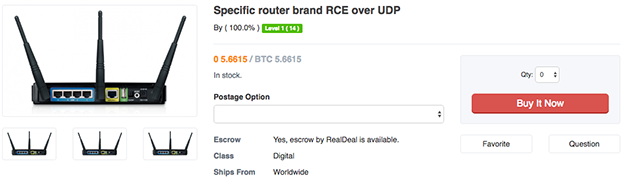
Ransomware
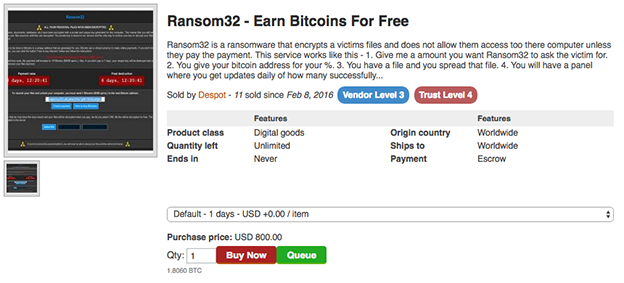
Ransomware is another popular item found in the attack marketplace. Ransomware is often sold in a variety of forms but ultimately requires the attacker to share some profits with the vendor or operator behind the campaign. For example, Ransom32 is selling on AlphaBay for $800. Once the attacker purchases the package from the vendor, they specify how much they want to ransom their victim for and give the vendor a Bitcoin address to send payments to. The vendor will then send the purchaser a malicious file that the attacker can send to their victims and give them access to a control panel where they can get daily updates about their current campaign and who has paid.
The attack marketplace is slowly allowing anyone and everyone to become an attacker if the price is right. For $19.99 a month an attacker can run attacks for 30 days, 1,200 seconds at a time utilizing multiple vectors of attack, or they can spend $1,000 and run their own botnet or ransomware campaign. This is ultimately shifting the scale of the attack landscape. It doesn’t take much more than an idea, and some money, to carry out a large scale attack today. We are now seeing a breed of attackers who know nothing about hacking other than what site they need to go to and how much they need to spend to carry out the campaign they envision. Those that have more money and less time to invest can immediately start their campaign without the need to learn about anything. The more money you have to spend on attack services, the more you can accomplish without prior experience.
Learn more about cyber-attack detection and trends in the 2016 Global Application and Network Security Report.
Download Now