Are you concerned about being targeted?
I am. As an IT person, it’s hard not be afraid when cyber attackers are always one step ahead of you. And, they have been quite busy this year, DDoSing, spreading malware, Ransoming and Doxing. I’m sure the stories have filled your newsfeeds.
The Bigger Picture
To understand what’s happening in the threat landscape, we need to put aside the headlines for a moment and focus on the bigger picture. There are five interesting trends that have implications for the way we perceive security, both as organizations and as individuals.
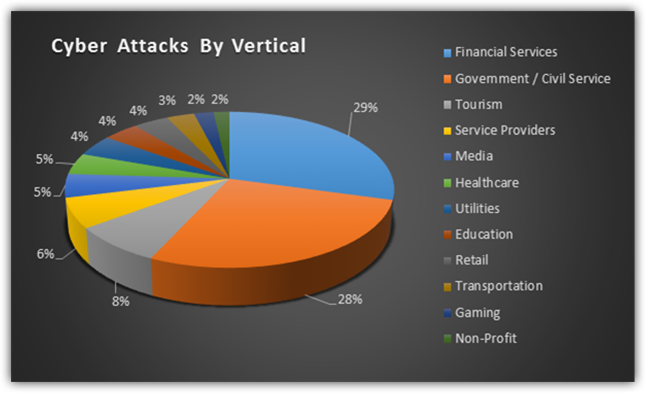
1. Cyber Ransom
Let’s say a couple of teenagers are up to no good and loitering outside your house. When you arrive home, they ask for money and threaten that they will spray your house with paintballs if you don’t. You laugh off the threat, thinking it’s just a few paintballs. However, the two teenagers return the next day with 50 of their friends, all of them armed with paintball guns.
This extortion method is now very popular in the virtual space, in the shape of DDoS threats. “If you don’t pay us – we will take down your network. Or your website. Or both.” These threat letters have been proven to be very profitable (for the perpetrators).
In fact, they worked so well that we saw more and more groups joining the game – some very capable ones, and many other copycats (here are some tips to tell the real from the fake). DD4BC, Armada collective, Kadyrovtsy and ezBTC Squad are some who have the ability to launch DDoS attacks at various volumes. Their threats are to be taken seriously, and in most cases a short “Demo” attack will follow the ransom note. These threats are also applicable to small and medium-sized businesses who do not have as high security walls as larger enterprises.
C-Suite Execs Say Won’t Pay Ransom Attacks, Until They Get Hacked, Radware Survey Finds
In parallel, ransomware also took its turn on companies. Initially it was used to harvest small amounts from helpless individuals...until the moment the attackers realized organizations can and will pay more.
Numerous new ransom malware types were introduced in early 2016 – the most common were Locky, Petya, Samas, Cerber and Bart. This plague hit everywhere, propagating in various forms such as spam, phishing and even Dropbox. These files are typically disguised as software updates, photos or documents (like invoices or CVs) but contain a malicious script used to encrypt all the files on the machine. Further analysis and tips for protection can be found here.
[You might also like: Ransom, Ransom Everywhere]
2. DDoS Commoditization
It is well known that DDoS attack tools are available on the Darknet. But in 2016, they are also available on the Clearnet for as low as $5. Here’s why this is important for businesses:
Imagine I had a horrible customer service experience at the café nearby, and was so upset that I took down their website for the whole evening, causing a loss of $1,500 - their average gross sales from evening deliveries. I don’t need to be a hacker to do it; I can just pay those five bucks and it’s done. I don’t need the know-how of a superpower hacker or the ultimate computer geek. All I have to do is choose my favorite DDoS tools.
The same applies for large businesses. For $350 I can hire a botnet or a stressed service to launch a 400Gbps DDoS attack. Some tools today are capable of doing much more than a simple flood, and can generate layer 3-7 multi-vector attacks that combine several DDoS techniques (floods, low and slow, SSL, etc.).
3. Cyber Protests
One may say that hacktivism is not new. However, as technology evolves – including social and communication channels, together with the availability of attack tools – hacktivists can pull out a successful operation quite quickly. We have seen hackers respond promptly to local controversies, such as the police shooting African-American suspects, the debate around the North-Carolina “bathroom law”, the city of Denver ban against homeless residents and more.
During these attacks, state and city websites were hit by DDoS attacks, and confidential data – mostly related to officials - was stolen and later published on the web.
Just as it happened in the US, it can happen anywhere else. In Africa, the Anonymous community has launched an operation (OpAfrica) against governments and leading corporations whom they hold accountable for corruption and child abuse.
Hackers also protest around universal causes such as animal rights. On top of targeting industries for trading animal-made products, every year during the whale hunting season Japan, Denmark and Norway suffer continuous attempts of DDoS attacks against government and leading enterprises. Examples include the network outages at Tokyo Narita airport and the take-down of Nissan’s websites.
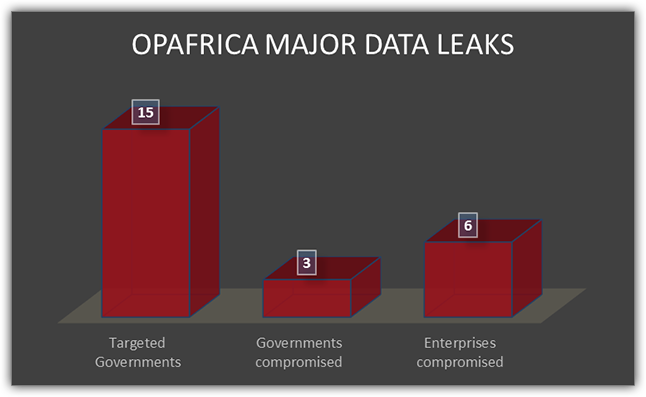
4. Elections
This particular example of the cyber protest may have the biggest impact of them all. Recently, Donald Trump and his business holdings have been victims of DDoS attacks & SQL injections. Hackers have penetrated the U.S. DNC, stealing classified information. The national election committee in the Philippines was breached and doxed, followed by a debate around the security of the e-voting system in Australia. On May 3, Anonymous members in Spain were arrested for hacking the central electoral board.
Here are a few questions we should ask following the rising engagement of the cyber community in national elections:
- Personal cyber-attacks – any influential person should expect them. Trump’s case suggests that every person with power and influence is subject to potential resistance from hacktivists, and should have a cyber-attack mitigation plan in place to protect personal and business holdings. By nature, political defiance may result in ongoing, continuous attempts.
- Security of electric voting systems. The Philippines COMELEC breach has shown e-voting systems may be prone to be compromised. What happens if the government saves a few dollars when designing the security architecture, or not constantly patching it? That gives hackers the power to steal population records and alter the vote data.
- Can cyber activity change election results? Beyond the general concern to election voting systems, such an event can potentially lead to psychological bias of voters, reduce election participation rates, undermine the governing party's support, and more.
- Rift among hacktivists over political affiliation. Another interesting aspect which is not directly linked to cyber security is the evolving debate between hackers about the core identity of Anonymous - whether it can or cannot be politically affiliated, or remain loyal to universal causes such as freedom of information, opposing oppression and correcting injustice.
The long debate, resulting in withdrawing of hackers from participation, created a lot of uncertainty around the attack operations, and definitely reduced their impact.
[You might also like: Malware and Botnet Attack Services Found on the Darknet]
5. IoT botnets
Right before the semester ended, we saw the long predicted threat come true.
PCWorld has reported “25,000 digital video recorders and CCTV cameras were compromised and used to launch distributed denial-of-service (DDoS) attacks, flooded targets with about 50,000 HTTP requests per second”.
There are 3 main takeaways from that incident:
- “Smart Appliances” manufacturers have to be mindful of producing resilient products with robust security components
- Network carriers have to be able to detect and manage traffic originated from such devices, to protect enterprise customers
- Enterprise customers should understand that when making a security investment to protect their infrastructure and assets, they need to be able to protect not only from today’s threats, but also from those which rise in the next 3-5 years

Download Radware's DDoS Handbook to get expert advice, actionable tools and tips to help detect and stop DDoS attacks.
Download Now