Who is to blame when hackers take control of thousands of internet-connected devices to carry out a DDoS attack?
That's what security researchers have been asking since the Dyn attack hamstrung dozens of major websites in October. Using the Mirai malware, hackers harnessed 100,000 internet-connected devices in a DDoS attack that reportedly reached 1.2 Tbps. Those devices, from cameras to DVRs, are often consumer-owned, and we wanted to see what consumers thought of their devices being co-opted for these attacks.
We asked them where they’d point fingers if their devices are compromised and used as part of an IoT botnet.
Some 69 percent of consumers hold device manufacturers responsible for making sure devices in consumers’ homes can’t be manipulated by hackers to launch attacks against others, according to a new study among over 2,000 U.S. adults conducted online on behalf of Radware by Harris Poll.
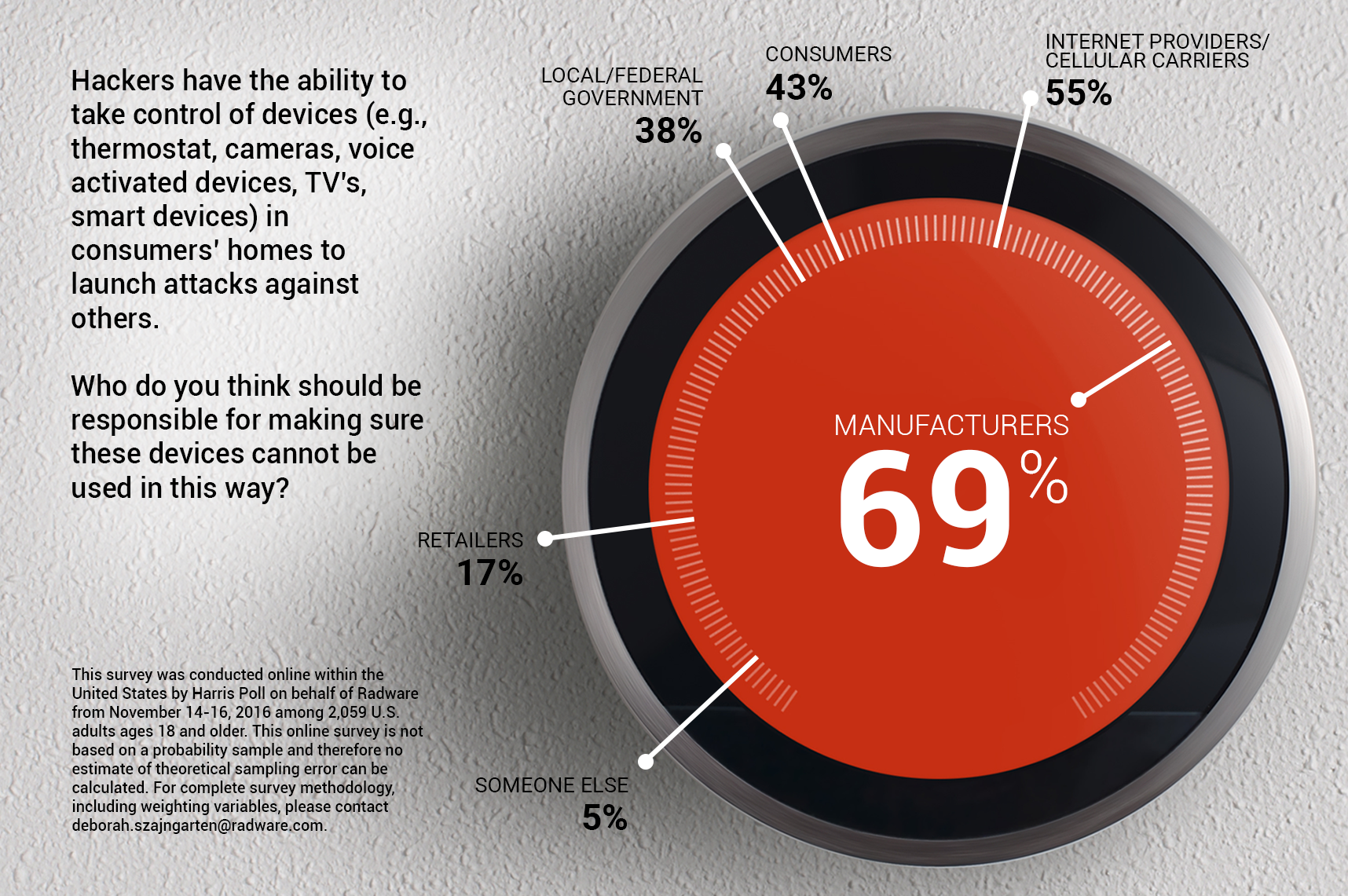
This makes sense, and manufacturers deserve the pressure consumers are putting on them. An HP study shows that 70 percent of IoT devices contain vulnerabilities. It turns out the race to bring the world online has included a few shortcuts.
Because these devices often use factory default credentials, have root passwords that can’t be changed, and have Telnet or SSH enabled, the devices are essentially Trojans with a secret backdoor. And when many manufacturers source their boards and software from the same sources, it creates vast numbers of devices easily compromised.
[You might also like: How Friday’s Massive DDoS Attack on the U.S. Happened]
Manufacturers’ software development lifecycles should take the security of the devices more seriously, and a number of simple steps could prevent future attacks, including requiring a change to default passwords and enabling Over The Air (OTA) software updates to patch vulnerabilities.
Without manufacturer action to secure these devices, IoT botnet attacks will only continue to grow, as we saw recently when hackers attempted to infect 900,000 internet routers in Germany with malware. Had they successfully harnessed a botnet that large, the DDoS attack they would be capable of generating an unprecedentedly massive DDoS attack.
But manufacturers aren’t the only ones consumers feel should be responsible for preventing misuse of their devices by hackers. More than half of consumers (55 percent) point fingers at internet service providers (ISPs) and cellular carriers.
Manufacturers have clear steps they could take to better secure devices, but blaming ISPs and cellular carriers is more complicated. While some attacks come in through a single ISP, collective attacks originate from many thousands of IoT devices that are presumably sending traffic across a large number of ISPs and carriers. That immediately makes detection and mitigation of some vectors difficult if not impossible for an ISP. Not to mention that some attacks look like legitimate traffic and ISPs would have trouble blocking them without network or application behavioral visibility.
Security solutions enterprises deploy should have device fingerprinting. IP addresses have lost the security value they once held, given dynamic IP addresses, global Network Address Translation (NAT), and anonymous proxies. While in the past, an IP address might lead back to a device or user, they’re all but meaningless today. Device fingerprinting, however, uses dozens of attributes to identify a device and track activities, creating a behavioral and reputational profile.
Ultimately manufacturers need to fix the vulnerabilities in their many internet-connected devices, but there’s no clear sign of when or how that will happen.
Survey Methodology:
This survey was conducted online within the United States by Harris Poll on behalf of Radware from November 14-16, 2016 among 2,059 U.S. adults ages 18 and older. This online survey is not based on a probability sample and therefore no estimate of theoretical sampling error can be calculated. For complete survey methodology, including weighting variables, please contact Deborah.szajngarten@radware.com.

Download Radware's DDoS Handbook to get expert advice, actionable tools and tips to help detect and stop DDoS attacks.
Download Now