A newly discovered botnet targets TCP port 8291 and vulnerable Mikrotik RouterOS-based devices. MikroTik, a Latvian hardware manufacturer, products are used around the world and are now a target of a new propagating botnet exploiting vulnerabilities in their RouterOS operating system, allowing attackers to remotely execute code on the device. Such devices have been making unaccounted outbound winbox connections. Radware’s Emergency Response Team (ERT) has spotted an increase in malicious activity following Kaspersky’s publication about the Slingshot APT malware that infected Mikrotik routers. It is believed this botnet is part of the Hajime botnet. Radware is witnessing the spreading mechanism going beyond port 8291 into others and rapidly infecting other devices other than MikroTik (such as AirOS/Ubiquiti). The concern is that this new botnet will be leveraged to launch DDoS attacks. This is another event demonstrating the struggle for control between various bot-herders.
[caption id="attachment_7999" align="aligncenter" width="551"]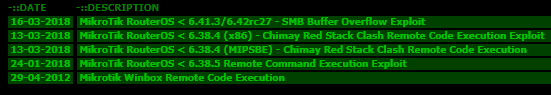 Figure 1: Multiple MikroTik exploits are available on GitHub and other sites[/caption]
Figure 1: Multiple MikroTik exploits are available on GitHub and other sites[/caption]
RouterOS Vulnerability
RouterOS is an operating system based on the Linux kernel, which implements functionalities normally used by ISPs, such as BGP, IPv6, OSPF or MPLS. RouterOS supported by MikroTik and its user community, providing a wide variety of configuration examples. RouterOS is embedded in MikroTik’s RouterBOARD product line, focused on small- and medium-sized Internet access providers that typically provide broadband access in remote areas.
[You might also like: Putinstresser.eu, a Simple and Powerful Booter and Stresser Service]
Preliminary analysis suggests that the botnet is exploiting known Mikrotik vulnerabilities (HTTP, SMB) as well as password brute-forcing. The worm has a highly efficient propagation mechanism by aggressively scanning for port 8291 in order to identify publicly available Mikrotik devices and using the password cracking capabilities to infect neighbor devices.
Mikrotik RouterOS SMB Buffer-OverflowVulnerability
A buffer overflow state occurs in MikroTik’s RouterOS SMB service when processing NetBIOS session request messages. Remote attackers exploiting this vulnerability can execute code on the system. As the overflow occurs before authentication takes place, an unauthenticated remote attacker can easily exploit it.
ChimayRed HTTP Exploit
The MikroTik RouterOS software running on the remote host is affected by a flaw in its HTTP web server process due to improper validation of user-supplied input. An unauthenticated, remote attacker craft a POST request to write data to an arbitrary location within the web server process, resulting in a denial-of-service condition or the execution of arbitrary code.
Infection Method
On 2018-03-24, 15:00 UTC time, Radware ERT research team has detected a huge spike on activity for TCP port 8291 in its global honeypot network.
[caption id="attachment_8000" align="aligncenter" width="648"]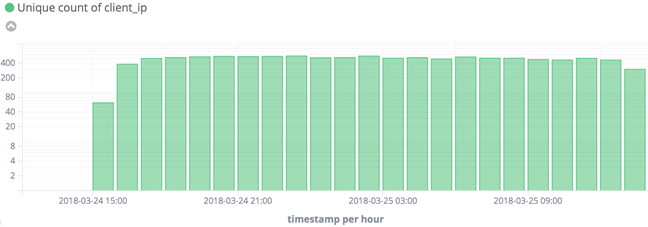 Figure 2: Unique IPs per hour, targeting TCP port 8291. Logarithmic scale[/caption]
Figure 2: Unique IPs per hour, targeting TCP port 8291. Logarithmic scale[/caption]
After near-zero activity for months, Radware witnessed over 10,000 unique IPs hitting port 8291 in a single day.
[caption id="attachment_8001" align="aligncenter" width="375"]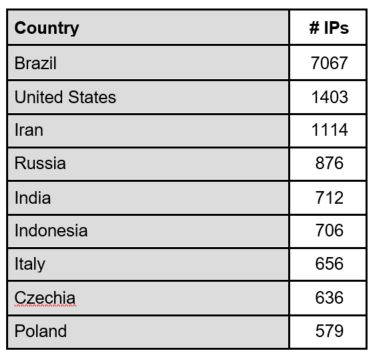 Figure 3: Distribution of unique IPs scanning for the vulnerability[/caption]
Figure 3: Distribution of unique IPs scanning for the vulnerability[/caption]
The worm aggressively scans the Internet with SYN packets to port 8291, but it never actually establishes a 3-way handshake on that port, e.g. no payload is sent to the point.
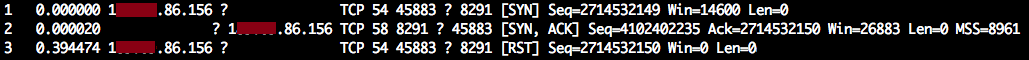
It appears the worm utilizes this stealth-SYN scan method to quickly identify vulnerable Mikrotik devices, as this port is used almost exclusively by the Mikrotik RouterOS platform. In addition to scanning port 8291, the worm targets the following ports: 80, 81, 82, 8080, 8081, 8082, 8089, 8181, 8880.
Exploits
The worm uses the ChimayRed exploit targeting vulnerable web servers on Mikrotik devices.
The worm will try to send the malicious payload to port 80 as well as other ports described earlier (80 81 82 8080 8081 8082 8089 8181 8880).
[You might also like: New Satori Botnet Variant Enslaves Thousands of Dasan WiFi Routers]
The worm has a very high success rate of exploiting and spreading, as mentioned in MikroTik’s own forum (*Update 1), “Our network had a major attack today as well. It seems like they opened some devices via the http port (quite an old firmware) and they tried to spread or access by brute forcing mikrotik neighbors."
This means that the worm utilizes exploits as well as password brute-forcing attempts to nearby neighbors, speeding up the infection rate.
[caption id="attachment_8003" align="aligncenter" width="948"]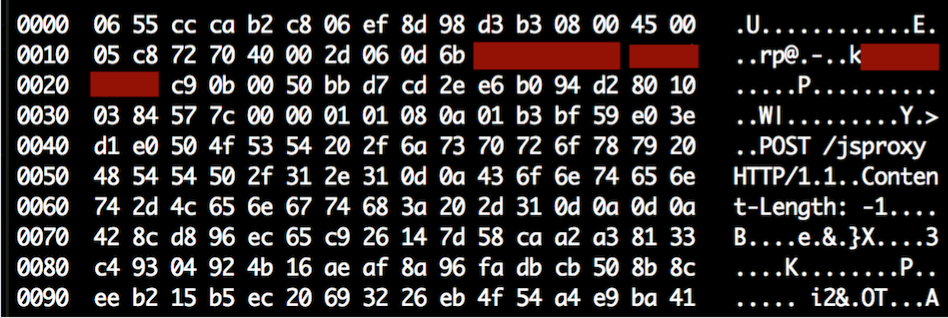 Figure 5: The exploit payload that Radware caught in its honeypot network[/caption]
Figure 5: The exploit payload that Radware caught in its honeypot network[/caption]
Hashes / IOCs
- /flash/bin/.telnetd
- /flash/bin/fifo
- /flash/bin/.p
- /flash/etc/rc.d/run.d/S99telnetd
- POST /jsproxy HTTP/1.1\r\nContent-Length:
Recommendations
Mikrotik recommends to Firewall ports 80/8291(Web/Winbox) and upgrade RouterOS devices to v6.41.3 (or at least, above v6.38.5 - *Update 2) Follow MikroTik’s thread on Twitter.
*Update 1: We regret the confusion caused by a wrong choice of wording that might have given the impression that MikroTik’s own network was compromised. We changed the wording from ‘own post’ to ‘own forum’ as the post was not originating from a MikroTik employee.
*Update 2: Updated MikroTik original recommendation that was posted in a deleted Twitter message (https://twitter.com/mikrotik_com/status/978160202380972032) and replaced with new recommendation as per the later Tweet (https://twitter.com/mikrotik_com/status/978533853324283904).

Download "When the Bots Come Marching In, a Closer Look at Evolving Threats from Botnets, Web Scraping & IoT Zombies" to learn more.
Download Now