DDoS-for-hire has been around for a while. Until recently, “booters” were known as paid online services used by gamers to initiate DDoS attacks against their opponents to gain a competitive advantage.
Now, DDoS attacks can be launched by anybody with a credit card and a motive. No longer exclusive to gamers and hackers, a competitive DDoS-for-hire market has expanded nearly to the point of commoditization.
Why?
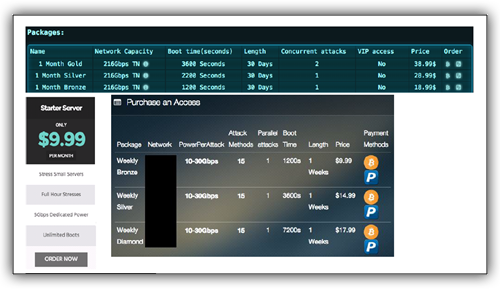
- Prices Are Decreasing – In the past, attacks cost hundreds of dollars. They are now offered in several models from weekly subscriptions to others that are only a few dollars per week.
- Quality of Service Increasing – Interfaces to the services, usability and visibility are looking professional and entail significant investment. Service offerings also include support and ticketing systems.
- Attack Sophistication Increasing – Both in terms of firepower and in terms of persistency of infections.
The DDoS-for-hire products are maturing into platforms that offer sophisticated financial fraud and spam capabilities, while providing customers with a cheap, high-quality service. Whether it’s financial gain, espionage, cyber war or hacktivism, attackers are finding reasons to uncover and exploit security vulnerabilities in servers and applications daily. The abundance of publicly exposed servers and routers with weak password and protection policies enables malware herders to quickly and inexpensively assemble a robot army.
Organizations should now, more than ever, deploy protection and mitigation technologies…and watch out whose wrath their activities awaken. Anybody who’s angry enough can easily rent themselves a vicious botnet for the low price of a coffee and sandwich.
A Case Study on Malware
A little more than a month ago, the Radware Emergency Response Team (ERT) noticed a significant increased usage of the Tsunami SYN Flood attack against a large customer. This was a strong indication of a service related robot.
Radware security researchers managed to obtain a sample of the malware binary used to generate these DDoS attacks. We then deployed the malware in an isolated and controlled environment to study its behavior and its different attack vectors.
During a period of 10 days (June 14-23, 2015), we monitored more than 2000 attacks against more than 60 different targets in 7 different countries.
Visit here to read the full case study and an analysis on the malware and incident.