In a world driven by apps, how do service providers accommodate the masses, meaning the masses of IoT devices, applications, consumers and bandwidth requirements and third-party access required to manage applications?

Underscoring all of this are APIs, which are a double-edged sword. While APIs are the cornerstone of this ubiquitous connectivity and integration, they also represent a massive security threat. Traditionally, application and API exposure had been constrained to IDC infrastructure. This meant that a secure data center (DC) or security gateway framework was used to harden the exposure of numerous applications in the same physical location. These applications communicated to the internet via a common path. In the scope of security design, this was a relatively easy problem to address.
Today's Landscape
In the modern landscape, applications will pay for edge computing resources and require direct access. It means constant interaction with third parties and computing fabrics via APIs.
API and application protection becomes a key component in modern edge security. 5G networks rely heavily on HTTP/2 and APIs, thereby inadvertently exposing critical infrastructure to tech-savvy hackers. Malicious network traffic can evade networking monitoring and attack detection solutions and erode computing resources.
[You may also like: 5G Security Considerations for Security Providers]
In this app-driven world, how do service providers protect themselves from third-party access? First, they must scale protection strategies and architectures to defend against volumetric attacks while addressing new complex attack surfaces, which require more sophisticated defenses. Automated software delivery will be critical and will allow service providers to address the complexity of a widely distributed architecture in a repetitive model. Network and security alignment will improve resource allocation while optimizing consumption-based delivery from edge computing systems.
When cybersecurity is built into the networks from the get-go, attacks can be addressed locally, avoiding backhauling attacks and driving efficiency back into the core computing environments. This scalable infrastructure protection strategy also serves as a point of escalation for more sophisticated or persistent attacks seen in gateways, applications and APIs.
[adbutler zone_id="276005"]
Network Protection Moving Forward
So in this newfound world, what are the primary security strategies that carriers must embrace to provide consumers and businesses with a secure experience? First, there should be an expectation that these instruments of innovation will dramatically increase the threat landscape if implemented incorrectly. Overall, there are three primary strategies that service providers need to execute to “sharpen the edge” and safeguard widely distributed architectures.
[You may also like: The Necessary Burden of 5G Security]
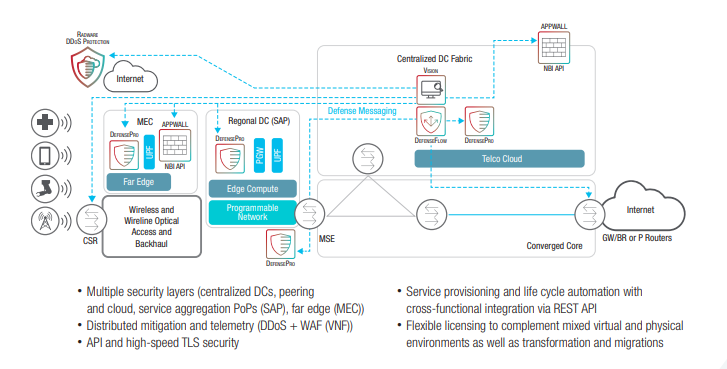
Protect the network from the internet. Service providers must protect the core network and service gateways from inbound attacks.
Protect distributed applications and APIs on edge computing platforms. Distributed applications and APIs are targets across the network. Safeguarding them is critical.
Protect the core from the access network. Infected mobile and IoT devices can be harnessed into large-scale bot attacks that enter the service provider’s network from the RAN.
Opportunity is Knocking
The move to edge computing environments, the deployment of 5G networks and the mass adoption of IoT devices have placed new cybersecurity demands on service providers at a time when the world is becoming increasingly insecure. But with change comes opportunity.
[You may also like: Here’s How Carriers Can Differentiate Their 5G Offerings]
By securing the customer experience, service providers have an opportunity to transform cybersecurity into a competitive advantage. They can establish a competitive advantage and fundamentally increase their addressable market by creating a secure environment that protects customers’ data and devices, building trust with new generations of consumers who demand security of their personal information. With the new reality of network slicing and highly distributed network functions, service providers will be overburdened unless they employ an automated, self-learning defense mechanism.
For service providers, the economics of an increase in security staff is not an option when moving toward 5G — it just doesn’t scale from a cost perspective, and it puts human engineers at the disadvantage of ever-increasing machine-based bot attacks.

Read “Sharpening the Edge: 5G Networks, Edge Computing, IoT and Their Implications on Cybersecurity for Service Providers” to learn more.
Download Now