User and Entity Behavior Analytics (UEBA) is a type of cybersecurity that uses machine learning (ML) to monitor and analyze the behavior of users and entities (such as devices, applications, servers, etc.) in a network. UEBA can detect anomalous or malicious activities in real time and alert security teams or take automated actions. UEBA solutions can complement or integrate with other security tools, such as Security Information and Event Management (SIEM) systems, to provide a more comprehensive and proactive approach to UEBA security. UEBA can help organizations prevent data breaches, insider threats, fraud, compromised accounts, and other cyberattacks by identifying and responding to deviations from normal behavior patterns.
How Does UEBA work?
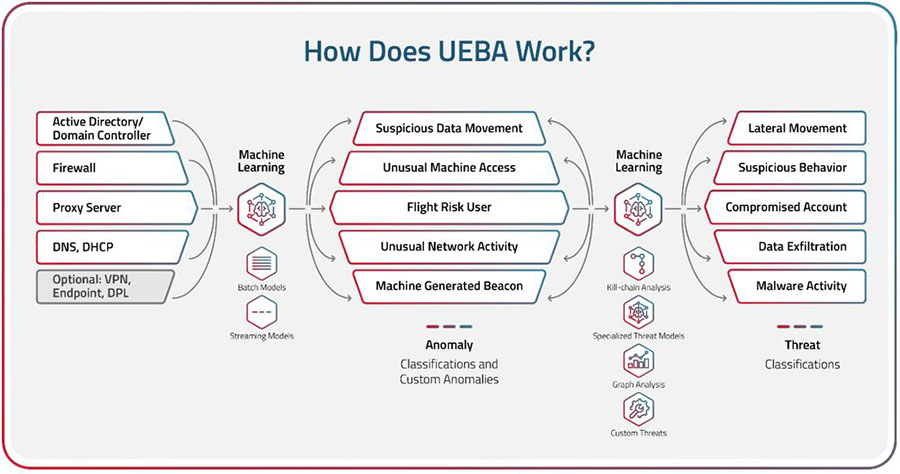
User and Entity Behavior Analytics (UEBA) discovers threats by identifying activity that deviates from a normal baseline. It can be used to monitor and detect unusual traffic patterns, unauthorized data access and movement, or suspicious or malicious activity on a computer network or endpoint. UEBA solutions work by analyzing activity from network users and other entities, such as hosts, applications, data repositories, and network traffic. They apply machine learning to real-time and historical data to develop a baseline of normal activity. Once they establish this baseline, UEBA solutions apply a host of analytics methods such as simple statistics, pattern matching, and signature rules to look for anomalies that indicate potentially suspicious or malicious activity.
For UEBA solutions to perform behavioral analytics effectively, an organization must first have a robust and integrated data set for the machine learning tools. UEBA systems can detect insider threats, malware, and advanced attacks by applying machine learning and behavioral analytics to users, machines, and entities. They provide the insights to find abnormal activity in real time and provide investigative insights so analysts can quickly verify and mitigate threats before they cause further damage.
UEBA Architecture and Components
UEBA architecture is based on an "outside-in" approach, which is inspired by Gartner’s paradigm for UEBA solutions. It is based on three frames of reference: use cases, data sources, and analytics.
Use Cases
Use cases prioritize relevant attack vectors and scenarios based on security research aligned with the MITRE ATT&CK framework of tactics, techniques, and sub-techniques that puts various entities as victims, perpetrators, or pivot points in the kill chain. Analytics uses various machine learning algorithms to identify anomalous activities and presents evidence clearly and concisely in the form of contextual enrichments.
Data Collection and Analysis
A UEBA system collects data about user and entity activities from system logs. It applies advanced analytical methods to analyze the data and establishes a baseline of user behavior patterns. UEBA continuously monitors entity behavior and compares it to baseline behavior for the same entity or similar entities to detect abnormal behavior. The system builds profiles of how each normally acts regarding application usage, communication and download activity, and network connectivity. Statistical models are then formulated and applied to detect unusual behavior.
Machine Learning Algorithms and Models
UEBA machine learning (ML) algorithms and models can be classified into two main categories: supervised and unsupervised. Supervised learning algorithms require labeled data to train and test the models while unsupervised learning algorithms do not need labels and can discover patterns and clusters from the data itself. Examples of supervised learning algorithms for UEBA are logistic regression, decision trees, support vector machines, and neural networks. Some examples of unsupervised learning algorithms for UEBA are k-means clustering, principal component analysis, anomaly detection, and auto-encoders.
Another example is Radware Bot Manager’s ML detection engine which combines Browser Anomaly Detection, Time Series-based Anomaly Detection, Clustering-based Detection, and Intent-based Deep Behavior Analysis (IDBA). Radware’s patented detection technology leverages a combination of supervised and unsupervised ML modules (illustrated below).
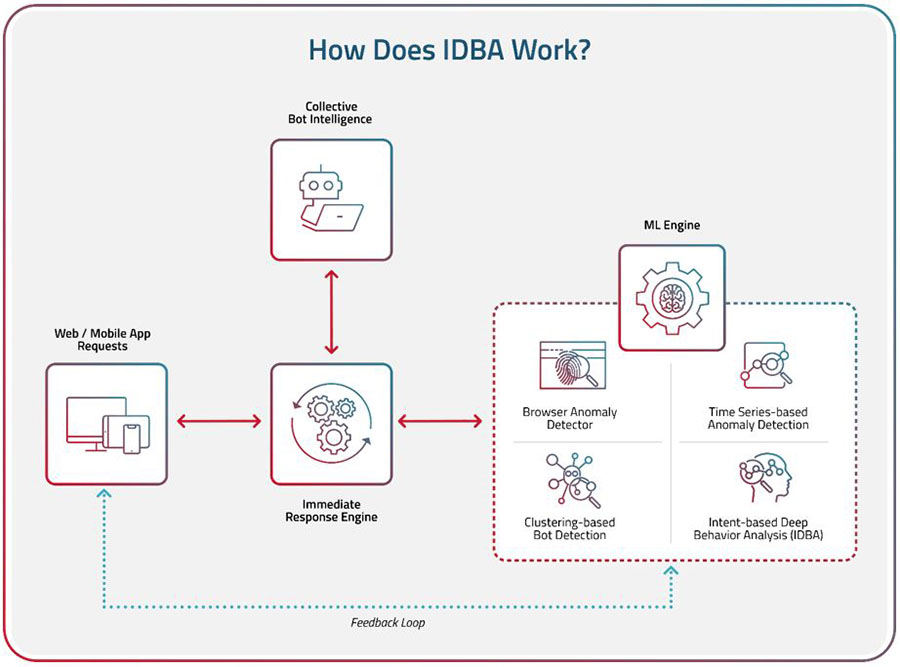
What Are the Benefits of UEBA?
UEBA provides several benefits, including:
- Improved threat detection and response: UEBA can detect complex and sophisticated threats that traditional security tools may miss, such as insider threats, compromised accounts, data exfiltration, lateral movement, privilege escalation, etc. UEBA can also provide contextual information and actionable insights to help security teams respond faster and more effectively to incidents.
- Real-time monitoring and analysis: UEBA can collect and analyze large volumes of data from various sources in real time, such as logs, events, and network flows. This enables UEBA to provide continuous visibility into user and entity behavior and detect anomalies as they occur.
- Detecting a wider range of cyberattacks: UEBA can detect a wide range of cyberattacks that target users and entities, such as phishing, malware, ransomware, denial-of-service, and more. UEBA can also detect emerging and unknown threats that may evade signature-based or rule-based security tools.
- Enhanced visibility into user and entity behavior: UEBA can provide a comprehensive view of user and entity behavior across the network, including who is accessing what resources, when, where, how, and why. This can help security teams understand the normal patterns of behavior and identify the outliers that may pose a risk.
- Reduces costs: UEBA can help reduce the costs associated with security operations by automating the detection and analysis of threats, reducing the workload and alert fatigue of security analysts, and minimizing the impact and damage of breaches.
- Lowers risk: UEBA can help lower the risk of data breaches, compliance violations, reputational damage, and financial losses by enhancing the security posture and resilience of organizations.
Use Cases for UEBA
Some of the main use cases of UEBA are:
- Detecting Suspicious User Accounts: UEBA can identify user accounts that exhibit abnormal or risky behavior, such as accessing sensitive data or systems without authorization, logging in from unusual locations or devices, or performing unauthorized actions. UEBA can alert security teams to investigate these accounts and take appropriate actions such as blocking, quarantining, or suspending them.
- Detecting Suspicious User-Like Entities: UEBA can also detect entities that mimic user behavior, such as bots, malware, or rogue applications. These entities may try to evade traditional security tools by blending in with normal user activity such as browsing the web or sending emails. UEBA can analyze the behavior patterns of these entities and flag them as suspicious if they deviate from the expected norms or show signs of malicious intent.
- Monitoring User Activity: UEBA can provide a comprehensive view of user activity across the network, such as what data or systems they access, when and how often they log in, what actions they perform, and who they interact with. UEBA can help security teams understand the normal baseline of user behavior and detect any deviations or anomalies that may indicate a security incident or a compliance violation.
- Detecting Suspicious Account Creation Attempts: UEBA can provide a comprehensive view of user and entity behavior across the network, including who is accessing what resources, when, where, how, and why. This can help security teams understand the normal patterns of behavior and identify the outliers that may pose a risk.
- Speeding Up Cybersecurity Investigations: UEBA can help security teams accelerate their investigations by providing them with relevant and actionable insights into user and entity behavior. UEBA can correlate different events and alerts across the network and provide a timeline of activities and interactions for each user and entity involved in an incident. It can also provide contextual information, such as the risk score, the motivation, and the impact of each behavior.
- Other uses for UEBA: These can include detecting data exfiltration, preventing fraud, enforcing policies, optimizing performance, and enhancing user experience. UEBA can provide valuable insights into user and entity behavior that can help organizations improve their security posture, compliance level, operational efficiency, and customer satisfaction.
Best Practices for UEBA Implementation
To implement UEBA effectively, organizations should follow some best practices, such as:
- Define the scope and objectives of the UEBA project.
Organizations should determine what types of behaviors and risks they want to monitor and mitigate, and how they will measure the success of the UEBA solution.
- Collect and integrate relevant data sources.
Organizations should collect data from various sources that can provide insights into user and entity activities such as logs, network traffic, endpoints, applications, identity and access management systems, etc. They should also integrate the data into a centralized platform that can support data ingestion, normalization, enrichment, and analysis.
- Choose a suitable UEBA solution.
Organizations should evaluate different UEBA solutions based on their features, capabilities, scalability, performance, ease of use, and compatibility with existing systems and tools. They should also consider the deployment model (on-premises, cloud-based, or hybrid) and the licensing model (perpetual, subscription-based, or pay-as-you-go) of the UEBA solution.
- Configure and tune the UEBA solution.
Organizations should configure the UEBA solution according to their specific needs and preferences by setting up user profiles and baselines, defining policies and rules, and creating alerts and notifications. They should also tune the UEBA solution to reduce false positives and false negatives, and to optimize the accuracy and efficiency of anomaly detection.
- Monitor and review the UEBA results.
Organizations should monitor the UEBA results regularly and review them for any anomalies or incidents that require further investigation or response. They should also use the UEBA results to generate reports and dashboards that can provide visibility and insights into user and entity behaviors and risks.
UEBA vs. Other Security Technologies
UEBA vs. UBA (User Behavior Analytics)
UEBA and UBA are two types of security solutions that use behavioral analytics to detect and prevent cyberattacks. The main difference between UEBA and UBA is that UEBA analyzes not only user behavior but also entity behavior such as devices, applications, servers, and networks. UBA focuses only on user behaviors including log-in patterns, file access, and network activity.
The pros of UEBA are that it can provide a more comprehensive and accurate view of the security posture of an organization as it can detect anomalies and threats from both insiders and outsiders, as well as from compromised or malicious entities. UEBA can also leverage machine learning and artificial intelligence to learn from normal and abnormal behaviors and adapt to changing environments.
The cons of UEBA are that it can be more complex and costly to implement and maintain as it requires more data sources, processing power, and storage capacity. UEBA can also generate more false positives and false negatives as it can be harder to distinguish between legitimate and malicious behaviors.
On the other hand, the pros of UBA are that it can be simpler and cheaper to deploy and operate since it requires fewer data sources, less processing power, and less storage capacity than UEBA. UBA can also provide a clear insight into user behavior and activity, which can help identify insider threats such as rogue employees or contractors.
The cons of UBA are that it can be less effective and reliable in detecting and preventing cyberattacks, as it can miss anomalies and threats from external actors or from compromised or malicious entities. UBA can also be more vulnerable to evasion techniques such as spoofing or masquerading.
UEBA vs. SIEM
UEBA and SIEM (Security Information and Event Management) are both types of security software that collect and analyze data from various sources to detect and respond to cyber threats; however, they have some key differences in their features and functions.
SIEM is mainly focused on aggregating log data from multiple devices and applications into a centralized platform where it can be correlated and analyzed to identify anomalies and alerts. SIEM can also provide real-time monitoring, reporting, and compliance capabilities. SIEM is useful for organizations that need to collect and manage large amounts of log data from different sources, while providing a holistic view of their security posture.
UEBA is an extension of SIEM that uses machine learning and data science to model the normal behavior of users and entities (such as machines, routers, servers, etc.) within a network, and to detect deviations from that baseline which may indicate a threat. UEBA can also use risk scores to prioritize alerts and reduce false positives. UEBA is useful for organizations that want to have more visibility into the activities and interactions of users and entities within their network, and to detect insider threats, compromised accounts, or data exfiltration.
Pros of SIEM:
- Collect and store large volumes of log data from various sources
- Provide real-time monitoring and alerting of security events
- Support compliance and auditing requirements
- Provide historical analysis and forensics capabilities
Cons of SIEM:
- Complex and costly to deploy and maintain
- Can generate a lot of noise and false positives
- Limited visibility into user behavior and context
- Scalability and performance issues
Pros of UEBA:
- Leverages machine learning and data science to model user behavior
- Detects subtle and complex anomalies that may indicate a threat
- Uses risk scores to prioritize alerts and reduce false positives
- Provides more visibility into user activity and context
Cons of UEBA:
- Requires a lot of data and processing power to build behavioral models
- Takes time to establish a baseline of normal behavior
- Can be affected by changes in user behavior or network conditions
- May have privacy and ethical implications
UEBA vs NTA (Network Traffic Analysis)
NTA (Network Traffic Analysis) is the process of monitoring and analyzing the data packets that flow through a network. NTA can help detect and prevent cyberattacks, optimize network performance, and troubleshoot network issues. There are several different types of NTA tools, including:
- Signature-based NTA: These tools use predefined rules or patterns to identify known threats or anomalies in network traffic. They are effective at detecting known attacks but they may miss new or unknown threats. They may also generate false positives if the rules are not updated or tuned regularly.
- Behavior-based NTA: These tools use machine learning or statistical models to establish a baseline of normal network behavior and then flag any deviations from it. They are capable of detecting new or unknown threats but they may require more computational resources and training data. They may also generate false negatives if the baseline is not accurate or representative.
- Hybrid NTA: These tools combine both signature-based and behavior-based approaches to leverage their strengths and mitigate their weaknesses. They can provide more comprehensive and accurate detection of network threats, but they may also be more complex and costly to implement and maintain.
Some of the pros and cons of NTA are:
- Pros of NTA: NTA can provide visibility into the network activity and identify potential threats that may evade other security tools. NTA can also help optimize network performance and efficiency by identifying bottlenecks, congestion, or misconfigurations. NTA supports forensic analysis and incident response by providing historical and contextual data on network events.
- Cons of NTA: NTA may require significant storage and processing capacity to handle large volumes of network data. NTA may also pose privacy and compliance risks if the network data contains sensitive or personal information. NTA requires skilled analysts and operators to interpret and act on the results.
Conclusion
UEBA can help identify and prevent threats that traditional security tools may miss such as insider attacks, credential theft, data exfiltration, and advanced persistent threats. UEBA works by establishing a baseline of normal behavior for each user and entity, and then applying various analytics methods to detect deviations from that baseline. UEBA can also integrate with other security products and systems to enhance threat detection and response.
Radware offers a range of UEBA solutions that can help organizations protect their networks from sophisticated cyberattacks:
- Radware Cloud Native Protection: Provides multi-layered protection for application infrastructure and workloads hosted in public cloud environments to prevent accidental exposure, misconfigurations, and malicious activity in the cloud environment
- Radware DefensePro: A real-time network attack prevention device that detects and blocks network-based attacks such as DDoS, zero-day exploits, web application attacks, and encrypted attacks.
- Radware Bot Manager: A comprehensive bot management solution that identifies and mitigates malicious bots and prevents attacks such as DDoS, web scraping, credential stuffing, account takeover, form spam, ad fraud, and other automated attacks.