
Credential stuffing is a technique used by hackers, fraudsters and cybercriminals to carry out account takeover (ATO) attacks on banking, e-commerce, media, gaming and other websites. The Open Worldwide Application Security Project® (OWASP) defines credential stuffing as "mass log-in attempts used to verify the validity of stolen username/password pairs.” ATO attacks are often carried out using credential stuffing techniques to illegally gain access to a user account and then steal funds or cash out other forms of stored value (such as reward points and gift vouchers), or to make purchases through the compromised account. Credential stuffing attacks can also be used to gain unauthorized access to confidential corporate or personal data which can then be abused and exploited in various ways.
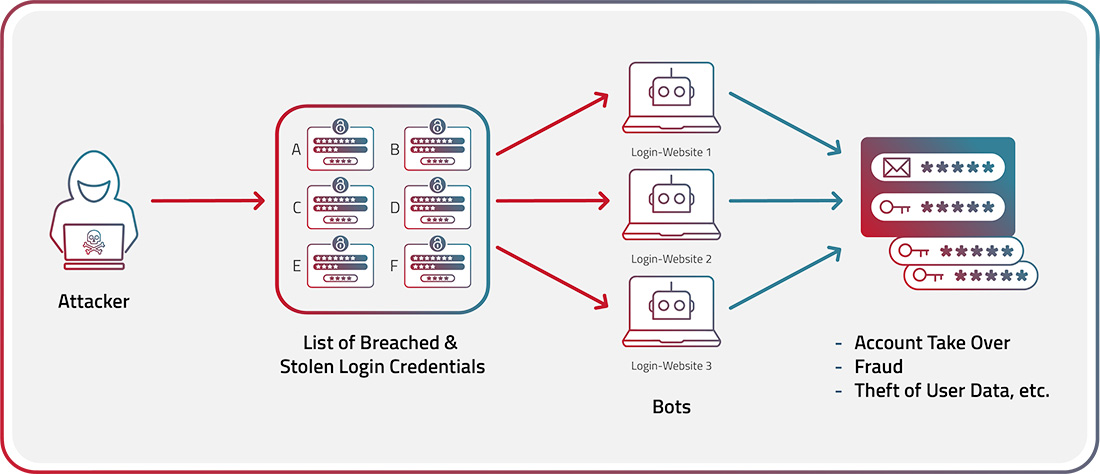
Credential stuffing attacks take advantage of the propensity of many internet users to reuse the same username and password on multiple websites. This type of attack is usually executed by cybercriminals who use bots to test lists of log-in credentials obtained from data dumps of stolen credentials or purchased from the dark web. Credential stuffing attacks differ from brute force attacks, also known as credential cracking, in that brute forcing is a technique to identify valid credentials by trying to guess different values for usernames and password combinations. It uses the power of bots to rapidly cycle through millions of combinations of characters in the hope of “cracking” the right username and password for a given account. Criminals also use dictionary attacks, entering large numbers of words and variations of words—such as using special characters to substitute for letters—to identify valid log-in credentials.
Why is Credential Stuffing a Cause for Concern?
Credential stuffing is among the most harmful and insidious types of bot attacks because it allows attackers to gain unauthorized access to user accounts, a practice also known as an account takeover (ATO). Once bad actors gain access to a user account, they have access to confidential business data and private, personally identifiable information (PII). This can then be abused to execute other types of attacks and perpetrate various forms of theft, fraud, espionage, misinformation, blackmail and other malicious activities.
Organizations receiving high volumes of fraudulent log-in attempts can experience a network saturation scenario that is akin to a DDoS attack originating from random IP addresses and devices, including those operating through web proxies. These requests will look like legitimate log-in attempts if the attacker is not directing a brute-force attack. If the entered credentials do not work—such as when the username entered by the attacking bot does not exist or if the password is incorrect—the bot simply moves on to continue stuffing more sets of log-in credentials from the list that the bot master has programmed into it.
Mitigating credential stuffing attacks requires a combination of measures. These might include limiting log-in attempts, implementing robust authentication processes, training account holders not to reuse passwords across multiple websites, and blacklisting IP addresses known to originate bot attacks. Organizations might also use solutions like Radware’s Cloud WAF for rule configuration or turn to CAPTCHAs or the alternative Crypto Challenge from Radware. Currently, dedicated bot detection and mitigation solutions like Radware Bot Manager are widely considered by security experts to be the most effective way to protect against credential stuffing attacks and eliminate account takeover attempts.