NoName057(16) is a pro-Russian hacker group that is known for its cyberattacks on Ukrainian, American, and European
websites of government agencies, media, and private companies. It is regarded as an unorganized and free pro-Russian
activist group seeking to attract attention in Western countries.
NoName057(16) is a pro-Russian hacker group that first declared itself in March 2022, and has carried out cyberattacks on Ukrainian, American,
and European websites belonging to government agencies, media, and private companies.
The first attacks claimed by the group in March 2022 were DDoS attacks targeting Ukraine news and media
websites Zaxid, Fakty UA, and others. Overall, the motivations center around silencing what the group deems to be
anti-Russian.
NoName057(16) operates using Telegram channels where they claim responsibility for their attacks, mock targets, make
threats, and share educational content. They have used GitHub to host their DDoS tool website and associated
repositories. The group has developed a DDoS tool named DDOSIA, which conducts denial-of-service attacks by repeatedly
issuing network requests to target sites.
In the global context of hacking collectives, there are numerous groups with varying objectives and methods.
NoName057(16) seems to be a relatively new entrant in this landscape with a specific focus on Ukrainian digital
infrastructure.
The group's rise to prominence can be traced back to their early operations. One of their most notable early
operations was a series of cyberattacks launched on government websites on the eve of the 2023 G20 Summit in India.
The group participated with other hacktivist groups to carry out approximately 2,450 targeted cyberattacks under
“#OpIndia”, over half of which were DDoS attacks. They targeted various sectors including the
government’s digital infrastructure, non-profit organizations’ websites, the finance and banking sector,
as well as energy and oil industry websites.
Their operations have continued to evolve over time. For instance, they have targeted several Indian businesses and
claimed data leaks. Their targets have included several Indian educational institutes, telecommunications companies,
manufacturing companies, and national archives.
NoName057(16) has evolved from its origins as a relatively unknown entity to a prominent hacking collective through a
series of high-profile cyberattacks. Their operations have grown in scale and sophistication over time, marking them
as a significant player in the global landscape of hacking collectives.
Some of the most notorious and impactful attacks attributed to NoName057(16) are:
Ukrainian Government and Utility Websites:
After targeting news servers, they expanded their targets to include Ukrainian government, utility, armament, transportation,
and postal websites. These attacks began to become more political in mid-June.
Ukrainian News Servers:
In early June 2022, NoName057(16) targeted Ukrainian news servers. This was one of their first attacks and marked the
beginning of their operations.
2023 Czech Presidential Candidates:
In January 2023, NoName057(16) began to target the websites of 2023 Czech presidential candidates. This marked a shift in
their operations as they started targeting political figures.
Canadian Government Websites:
On September 13, 2023, the NoName057(16) group launched a DDoS attack on many Canadian and Quebec government websites. This was one of
their most recent and impactful attacks.
These attacks have caused significant disruption to crucial government infrastructure and businesses, impacting the
average citizen's ability to interact with these entities. The group's operations have grown in scale and
sophistication over time, marking them as a significant player in the global landscape of hacking collectives.
Radware offers a comprehensive suite of products and services designed to protect against a wide range of
cyberthreats, including those posed by hacking collectives like NoName057(16). Key security solutions from Radware
include:
Cloud DDoS Protection Service can help mitigate
DDoS attacks by providing real-time protection for the most sophisticated DDoS and web security threats
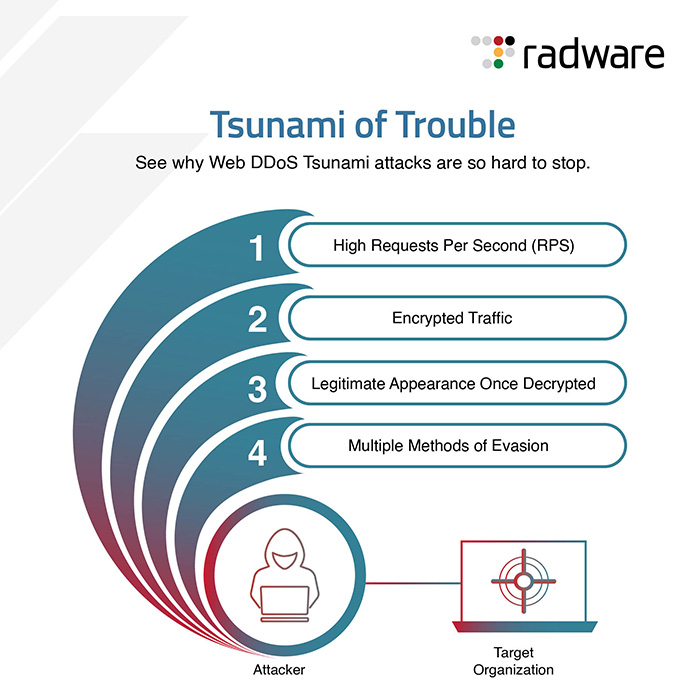
including
the latest type of Web DDoS “Tsunami” attacks that mainly target Layer 7 (known as the application
layer).
Bot Manager provides comprehensive protection of web
applications, mobile apps and APIs from automated threats like bots.
Radware’s Attack Mitigation Solution (AMS) is a set of patented technologies designed to
detect, mitigate and report todays most advanced DDoS attacks and cyberthreats. It offers a set of security
modules to protect infrastructure against a variety of attack vectors.
DefensePro is a real-time, behavioral-based DDoS
mitigation
device that protects against known and emerging network security threats. Its behavioral-based detection enables
it to detect and mitigate emerging network attacks in real time, such as high-rate DDoS attacks and encrypted
threats.
Cloud WAF provides enterprise-grade, continuously
adaptive web application security protection.