
A Web DDoS Tsunami attack is an evolved type of HTTP DDoS Flood cyberattack that is sophisticated, aggressive and very difficult to detect and mitigate without blocking legitimate traffic.
Characteristics of a Web DDoS Tsunami attack include:
- Very high level of requests per second (RPS)
- Attack traffic is encrypted
- Once decrypted, traffic appears legitimate
- Multiple methods of evasion: randomized headers, IP spoofing and more
Web DDoS Tsunami attacks were developed during the new era of hacktivist activity sparked by Russia’s invasion of Ukraine on February 24, 2022. Attack tactics began with high-volume network-based Flood attacks. Later, they evolved to more sophisticated multi-vector application-level attacks that are hard to detect and mitigate. As many of these attacks are launched by state-sponsored groups or by organized cyber hacktivism/terrorism, they are better thought out and planned and take advantage of large-scale resources and sophisticated scripts.
These cyberattacks focus on denial of service and the defacement of websites around the world. Targets include:
Web DDoS Tsunami attacks combine application layer attack vectors, leveraging new tools to create sophisticated attacks that are harder—and sometimes impossible—to detect and mitigate with traditional methods.
They leverage sophisticated evasion techniques to bypass traditional app protections, such as randomizing HTTP methods, headers and cookies. They impersonate popular embedded third-party services and spoof IPs and other key targets. Application-level attack methods include HTTPS Get, Push and Post request attacks with changing parameters behind proxies and dynamic IP attacks. All look like legitimate requests.
The time it takes to analyze the attack and deploy a rule means significant downtime—lasting from minutes to hours—in every iteration of the attack. All of this and the continuous morphing of the attack result in continuous downtime.
Network-based DDoS Protection solutions cannot detect and accurately mitigate Layer 7 DDoS attacks. Because this would require the decryption of attack traffic and deeper inspection of Layer 7 headers, attacks go undetected by network-based protection solutions. And while standard on-prem or cloud-based web application firewalls (WAFs) are effective against standard web-based threats, they fail to protect against Web DDoS Tsunami attacks for these reasons:
Scale
The rate of some of these attacks, measured by RPS, is reaching new heights. Over the past year, several multi-million RPS attacks were observed by multiple third parties and publicly disclosed. The rates and volume of traffic by far exceed the capacity of on-prem solutions.
Attack Sophistication
These attacks appear as legitimate traffic requests and are constantly randomized. There is no pre-defined signature or rule-based mechanisms because requests appear legitimate and do not contain any specific bad arguments. Only behavioral-based algorithms with self-learning and auto-tuning can detect and mitigate.
Morphing Attacks
The dynamic nature of these new threats—the frequency in which they change and sustain these changes over a long period of time—is unprecedented. To protect against such attacks, organizations need solutions that can quickly adapt in real-time to the attack campaign. A standard on-prem or cloud-based WAF is not able to provide that.
Human Factor
The sophistication of attack campaigns requires security experts that can handle the complexity of the attacks and ensure the quality of protection is not compromised during an attack. Self-managed teams, limited in personnel, tools and budgets, cannot cope with a 24x7 attack campaign. Also, on-prem tools are mainly rule-based and require definition of new rules for mitigation.
To protect against Web DDoS Tsunami attacks, organizations must use a cybersecurity solution with dedicated, behavioral-based algorithms to quickly detect and surgically block Layer 7 DDoS attacks without blocking legitimate traffic. It’s important to choose a solution that is uniquely designed to protect against these large and sophisticated attacks and provide customers with advanced protection at the scale needed.
The solution should include:
Accurate, Automated Detection and Mitigation
Dedicated, behavioral-based algorithms with advanced learning capabilities to quickly detect and surgically block Layer 7 DDoS attacks while minimizing false positives and allowing legitimate traffic. In contrast to the common volumetric approach of most vendors, Layer 7 behavioral-based protection can accurately distinguish between a legitimate surge in traffic (aka flash crowd) and a flood of attack traffic generated by adversaries. It must ensure that only malicious traffic is blocked—even during Web DDoS Tsunami attacks.
Widest Layer 7 DDoS Attack Coverage
Protection from a wide range of Layer 7 DDoS threats includes smaller-scale, sophisticated attacks, new Layer 7 attack tools and vectors, and large-scale, sophisticated Web DDoS Tsunami attacks. Your solution must be able to analyze advanced threats as well as their numerous variants. It also needs to adapt to any attack patterns, randomization methods and attack techniques.
Immediate and Adaptive Protection
The right solution must leverage proprietary behavioral analysis and real-time signature generation to detect and block HTTPS floods and continuously adapt the mitigation in real-time to the hyper-dynamic changes in attack traffic to prevent downtime.
As an organization grows and applications evolve, a comprehensive, adaptive cloud application protection service is needed to protect against threat vectors, eliminate management overhead and enable the fastest time to protection.
Radware’s Cloud Web DDoS Protection is the only known solution that stops Web DDoS Tsunami attacks without affecting legitimate traffic. It works alongside other best-of-breed solutions as part of Radware’s Cloud Application Protection Service. This best-of-suite service protects through a single platform including industry-leading WAF, bot management, API protection, client-side protection and cloud web DDoS protection.
Notice the high rate of requests per second (RPS) in this attack that Radware immediately detected and mitigated:
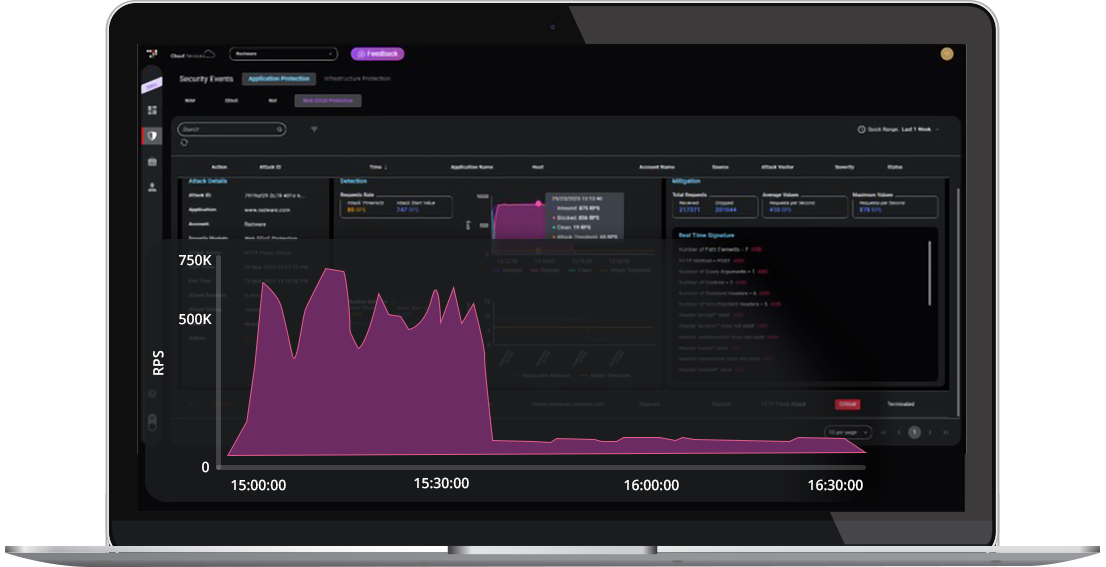 Two-hour Web DDoS Tsunami attack peaking at 738,000 RPS
Two-hour Web DDoS Tsunami attack peaking at 738,000 RPS