User Datagram Protocol (UDP) is a connectionless, unreliable protocol used in computer networks. It operates on the transport layer of the Internet Protocol (IP) and provides fast, efficient data transfer across networks. Unlike TCP – its more reliable counterpart – UDP does not provide end-to-end reliability or flow control.
A UDP flood attack is a type of Distributed Denial of Service (DDoS) attack in which an attacker sends a large number of User Datagram Protocol (UDP) packets to a target port, causing the server to become overwhelmed and unable to respond to legitimate requests. This results in the target system becoming unresponsive.
Learn more in our detailed guide to DDoS examples.
A UDP flood attack works by overwhelming a targeted system with User Datagram Protocol (UDP) packets. An attacker will send a large number of UDP packets with random data to the target port.
The receiving host checks unreachable applications and ports (by design by the attacker) associated with these datagrams and responds back with a “Destination Unreachable” response. The attackers may also spoof the return IP address making it unreachable as well. As more and more such packets are received, the server becomes flooded and unable to process legitimate requests or respond to other client requests.
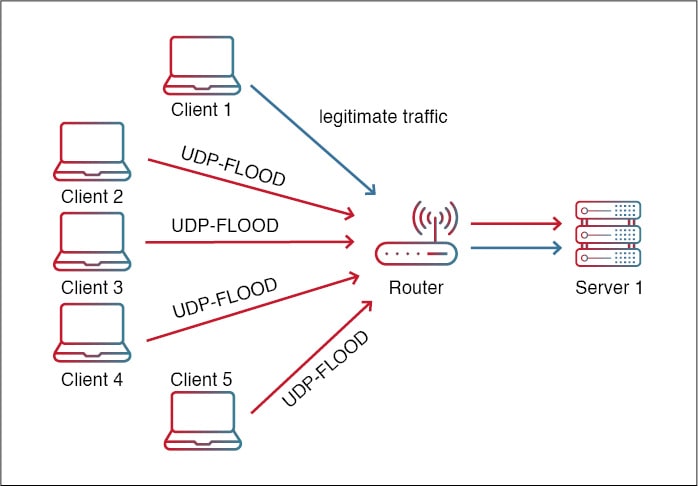
A UDP flood attack can be mitigated by utilizing a variety of methods. One of the most effective measures is to implement rate-limiting on incoming traffic. Rate-limiting is a technique that allows the server to limit the number of packets sent by each individual source address over a certain period of time. However, rate limiting may prevent legitimate traffic during surge conditions.
Radware DDoS protection (DefensePro, Cloud DDoS Protection Service), WAF (AppWall and Cloud WAF) and application delivery (Alteon with integrated WAF) solutions mitigate UDP Flood attacks by using machine-learning and behavioral-based algorithms to understand what constitutes a legitimate behavior profile and then automatically block malicious attacks. Radware manages user connections effectively without impacting legitimate requests, increasing protection accuracy while minimizing false positives and disruption to legitimate users.
Related content: Read our guide to TCP flood attacks.