MyDoom—also known as “Novarg”—is a notorious computer worm that emerged in the early 2000s, leaving a lasting impact on the cybersecurity landscape. Spread primarily through email attachments, MyDoom exhibits self-replicating behavior, swiftly propagating across networks and devices. Once activated, it establishes a backdoor in infected systems, granting unauthorized access to cybercriminals. This enables a range of malicious activities, including data exfiltration, remote control of compromised machines, and the formation of botnets for orchestrating widespread distributed denial-of-service (DDoS) attacks. Its targeted approach of using emails to exploit human behavior underscores the importance of robust email security measures. MyDoom's legacy serves as a stark reminder of the necessity for multi-layered cybersecurity strategies that encompass technical defenses, employee training, and incident response planning.
The History of MyDoom virus development
The history of the MyDoom virus development is marked by its emergence in the early 2000s, signifying a significant milestone in the realm of cybersecurity threats. Discovered in January 2004, MyDoom swiftly gained notoriety due to its rapid propagation and disruptive capabilities. This malicious worm spread primarily through email attachments, exploiting human curiosity and inadvertently prompting users to activate its payload. By capitalizing on the social engineering aspect, MyDoom infiltrated countless systems, creating a network of infected devices that could be harnessed for various cybercriminal activities.
MyDoom quickly surged across the Internet, infecting millions of machines within a remarkably short span of time. Its ability to generate and send a vast number of infected emails, coupled with its stealthy propagation methods, contributed to its extensive reach. Notably, MyDoom's payload included a backdoor component, allowing unauthorized access to infected systems. This granted cybercriminals a foothold to remotely control compromised devices, and even form botnets capable of launching large-scale DDoS attacks. In fact, MyDoom is estimated to have caused billions of dollars in damages due to disrupted services and compromised systems. Its rapid spread and devastating consequences underscored the need for enhanced email security, proactive cybersecurity measures, and heightened user awareness to mitigate its impact.
MyDoom operates as a sophisticated computer worm with intricate technical mechanisms that allow it to propagate, target systems, and inflict substantial damage. Upon activation, MyDoom employs a multi-pronged approach to exploit vulnerabilities and spread its malevolent influence.
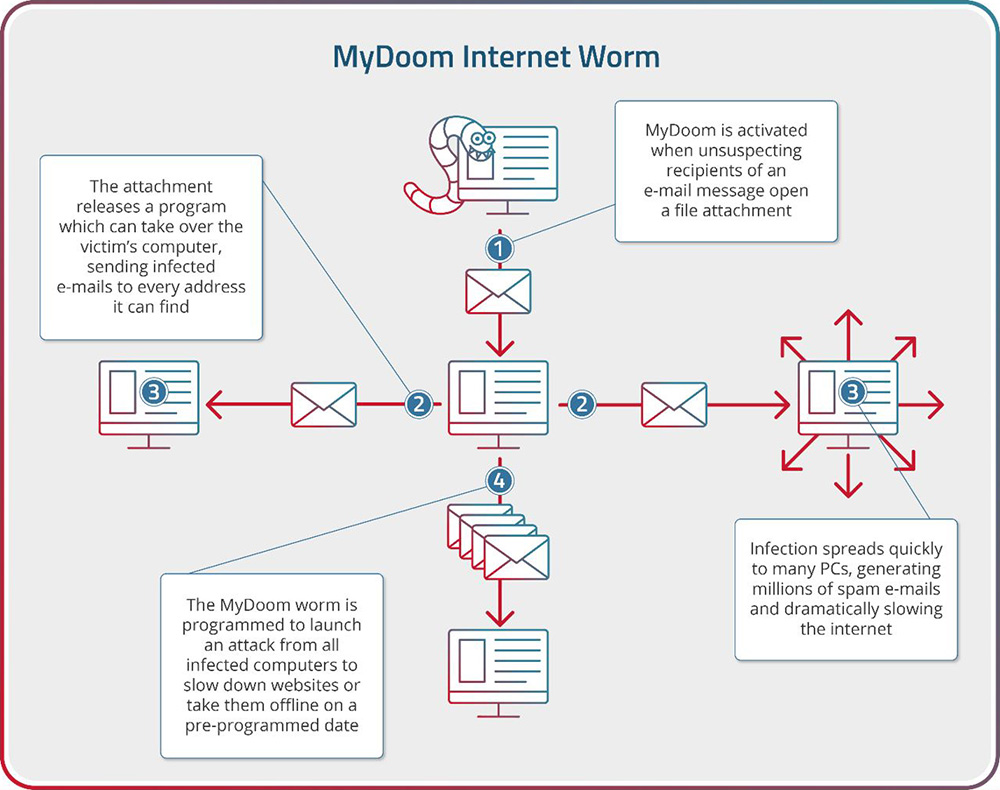
Propagation Mechanism:
MyDoom predominantly spreads through email attachments, often disguised as legitimate files or messages. When a user unwittingly opens the infected attachment, the worm is executed, initiating its propagation. MyDoom's payload includes an SMTP engine that enables it to generate and send a copious number of infected emails to addresses harvested from the infected machine itself, making its distribution exponential. This social engineering approach capitalizes on human curiosity, prompting users to engage with the infected content and unwittingly trigger the worm's proliferation.
Payload and Impact:
Once inside a system, MyDoom initiates its damaging processes. It seeks to exploit vulnerabilities and establish a backdoor, providing cybercriminals unauthorized access to the infected machine. This unauthorized access enables various nefarious activities, including data exfiltration, remote control, and participation in botnets. As part of a botnet, compromised devices can be harnessed to launch coordinated and powerful DDoS attacks, overwhelming targeted websites or services with an avalanche of traffic, rendering them inaccessible.
Moreover, MyDoom possesses the ability to target specific domains, potentially crippling an organization's online presence and communications. Its payload includes mechanisms to thwart attempts to remove or disinfect the worm, making its eradication a challenging endeavor. This persistence, coupled with its rapid propagation, exacerbates the overall impact.
The damage inflicted by MyDoom is multifaceted. It can disrupt business operations, compromise sensitive data, and lead to financial losses due to service interruptions and remediation efforts. In addition, the compromised systems can be enlisted for further cybercriminal activities, amplifying the worm's destructive potential. The propagation rate and wide-ranging capabilities of MyDoom emphasize the importance of robust email security, continuous software updates, and proactive cybersecurity practices.
Protecting both individuals and organizations from threats like MyDoom necessitates a multifaceted approach that encompasses robust cybersecurity practices and the implementation of advanced security solutions, such as those provided by Radware. Employing a combination of proactive measures and cutting-edge tools can effectively mitigate the risks associated with such malicious entities.
Incident Response Planning:
Preparing for potential outbreaks is essential. Organizations should establish detailed incident response plans that outline steps to contain and mitigate threats. Timely action can minimize the impact of a malware outbreak and expedite recovery.
Antivirus Software and Intrusion Detection Systems:
Utilizing reputable antivirus software and intrusion detection systems is fundamental. These solutions can identify and quarantine malicious files and activities, preventing the initial infiltration of worms like MyDoom. Regularly updating these tools ensures they are equipped to detect the latest threats.
Radware Security Solutions:
Radware offers a suite of advanced cybersecurity solutions that are particularly relevant for safeguarding against threats like MyDoom. Our DDoS protection solutions can help prevent large-scale attacks by identifying and mitigating abnormal traffic patterns. Radware's application security solutions provide enhanced protection against application-level attacks, a common vector exploited by worms like MyDoom.
Incorporating Radware's solutions into an organization's cybersecurity strategy can significantly enhance its resilience against evolving threats. By leveraging Radware's expertise and advanced technologies, businesses can ensure their networks, applications, and data remain secure against sophisticated threats such as MyDoom and similar malware. Additionally, fostering a culture of cybersecurity awareness, where employees are educated and empowered to identify and report potential threats, is essential to fortify an organization's defense posture against these malicious entities.
Email Security:
Rigorous email security practices are crucial. Filtering incoming emails for suspicious attachments and links can thwart attempts to spread malware. In addition, user education is vital to avoid inadvertently activating infected content.
Regular System Updates:
Frequently updating operating systems, applications, and software patches is crucial. Vulnerabilities that could be exploited by malware like MyDoom are often addressed in these updates, minimizing the risk of unauthorized access and system compromise.
Safe Internet Usage Habits:
Encouraging safe internet usage habits among employees is essential. This includes avoiding downloading files from untrusted sources, refraining from clicking on unsolicited links, and being cautious with email attachments. A culture of cyber awareness can significantly reduce the risk of falling victim to threats like MyDoom.