The cyber security world is in turmoil. A new generation of HTTPS DDoS attacks is disrupting the market, bypassing organizations' DDoS protection and WAF solutions. As we explained in our detailed threat analysis report, many of these attacks are launched by hacktivist groups — such as Killnet, NoName057(16), Team Insane PK, Mysterious Team, Passion Group and Anonymous Sudan — that are leveraging new, sophisticated botnets and tools to launch cyber terrorism and agenda-driven attacks around the world. In a period spanning just two months, from February 18 to April 18, 2023, over 1,800 DoS (denial-of-service) attacks were claimed by hacktivists across 80 Telegram channels. These attacks are high in RPS (Requests Per Second) and sophisticated in behavior, masquerading as legit traffic and going unnoticed upon decryption.
Network-based DDoS protection and Web Application Firewall (WAF) solutions, which have been effective in the past, are no longer capable of protecting against the new type of HTTP DDoS Tsunami Attacks. One of the challenges posed by the new type of HTTP DDoS flood attacks is their high RPS rates. Attackers can generate a vast number of requests per second, overwhelming web servers, load balancers and WAFs, and causing them to crash.
Many DDoS protection and WAF solutions rely on rate limiting to block such attacks, but the cost is very high because doing so means blocking legitimate traffic from accessing the application. Another factor that contributes to the ineffectiveness of standard DDoS protection and WAF solutions against new types of HTTP/S DDoS flood attacks is their reliance on pre-defined signatures. These solutions use signature-based detection, which relies on pre-defined patterns of known attacks. However, the new type of HTTPS DDoS flood attacks is designed to evade signature-based detection, rendering these solutions ineffective. Security teams need to spend hours and days analyzing the attack traffic in order to establish new rules, which by that time won’t be relevant as the attack will have already shifted to a new set of unknown HTTP requests. The attacking botnets are randomizing HTTPS methods, headers and cookies, impersonating popular embedded third-party services, spoofing IPs, and more. Among the application-level attack methods seen in these recent campaigns were HTTPS Get, Push and Post request attacks with changing parameters, behind proxies and dynamic IP attacks. All look like legitimate requests.
Web DDoS Tsunami Attacks in Real Life
Here are a couple of examples of web DDoS Tsunami Attacks the Radware Web DDoS Protection Solution automatically mitigated for one of our customers just last week.
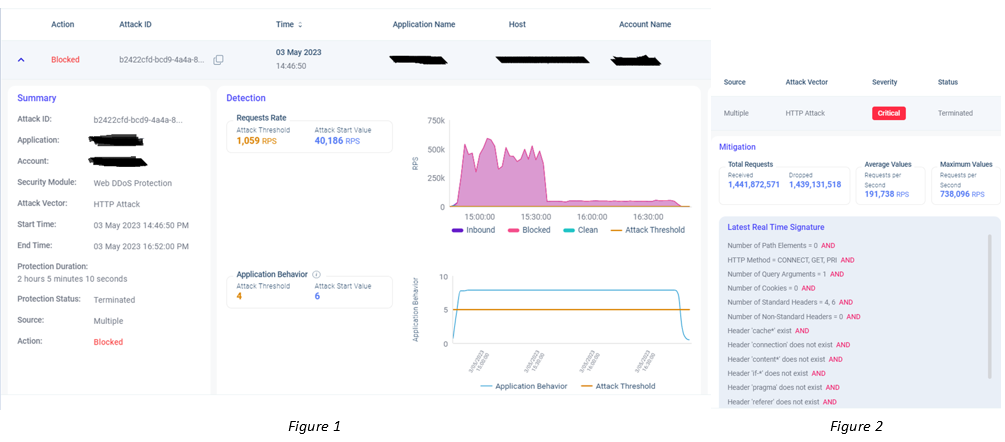
Figures 1 and 2 – 738K RPS HTTPS DDoS attack

Figure 3 – 878K RPS HTTPS DDoS attack
The above images were taken last week just a few days apart on our Cloud Application Protection portal. The first attack lasted four hours and peaked at 880K RPS. Just a few days later a second attack occurred that lasted almost 2 hours and peaked at 738K RPS.
As you can see from the latest signatures that were generated immediately by the Web DDoS protection engine, these web DDoS Tsunami Attacks look like legit traffic with HTTP methods such as GET, DELETE and PUT, and have standard headers and structure.
Our solution was able to stop these two attacks from the get-go while still allowing all legitimate traffic in.
Radware To the Rescue
Radware has foreseen this future that is now a reality. So, to overcome this level of attack sophistication, our product teams developed and recently introduced proprietary, behavioral-based algorithms that can detect and quickly generate new signatures for unknown malicious requests at a high scale on the fly and, in real-time, mitigate these web DDoS Tsunami Attacks without generating false positives and blocking legitimate traffic.
Unlike other vendors that use a volumetric approach that doesn’t distinguish between good and bad traffic, Radware's solution accurately distinguishes between legitimate traffic surges and malicious attack traffic. The solution protects against a wide range of Level 7 (L7) DDoS threats, including sophisticated attacks, new L7 attack tools and large-scale Web DDoS Tsunami Attacks. It continuously and automatically analyzes various threats and their numerous variants, adapting to any attack patterns and randomization methods.
If you would like more information about our industry-leading solution against the latest generation of disruptive web DDoS attack, reach out to Radware’s cybersecurity professionals here. We would love to hear from you.