Ideology, politics and religious differences are at the core of operation OpIsrael. OpIsrael is launched by Anonymous with the stated goal of “erasing Israel from the internet” in protest against the Israeli governments’ conduct in the Israeli- Palestinian conflict. This is a yearly operation and was created in 2012. It starts every year on April 7th and ends on April 20th. This operation sees participants from Anonymous, AnonGhost, Red Cult, Anonymous Lebanon, Mauritania Attackers, Cyber Team Tox, M0oDyPL, MCA DDoS Team and LaResistance Hacking Team along with other independent attackers.
In the past years, Israel has seen moderate attacks launched against its networks and infrastructure. The most common tactics are website defacements and denial-of-service attacks but have also included application attacks and data dumps. Each year, hackers organize in public channels like Internet Relay Chats (IRCs), Telegram, Twitter and Facebook to discuss operational details. Attackers provide others with tools and technical guidance leading up to the operation. They will post links to videos, attack tools and recommend VPN’s along with target lists and content for social media.
OpIsrael receives a large amount of attention for several reasons; one of them being the global media coverage surrounding the Israeli-Palestinian conflict. The other is due to past operational successes by Anonymous, but in recent years this has been slowly fading. OpIsrael is losing its reputation as a successful operation overall. In recent years, pro-Israeli hackers have launched counter attacks against OpIsrael. These attacks are often more successful and gain more attention than the operation itself.
This year OpIsrael was very mild. The main activity only took place on the 7th with limited attacks for the rest of the campaign. There was very limited participation this year in most IRCs. Most users in the #OpIsrael IRC on AnonOps were just idling, and were likely researchers from other companies monitoring the events as well. This channel was eventually overrun by pro-Israeli hackers and eventually abandoned as the operation fell apart.
[caption id="attachment_6814" align="aligncenter" width="624"]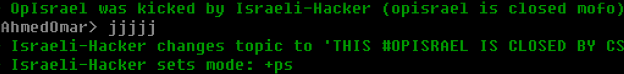 #OpIsrael on AnonOps[/caption]
#OpIsrael on AnonOps[/caption]
Inside other IRC channels there was very limited support or guidance for those looking to participate. Most of the activity on social networks was concentrated on Facebook. Normally Anonymous operates around IRC channels and Twitter, but has been favoring Telegram and Facebook lately.
AnonGhost for the last few years has used Telegram over IRC’s as their main channel of communication. This year their channel #OpIsrahell was the main channel by AnonGhost but was ultimately shut down after noticing details about their tactics and procedures were published by Radware.
[caption id="attachment_6815" align="aligncenter" width="462"]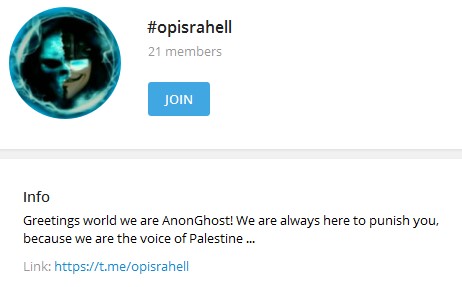 AnonOps IRC / #OpIsrael[/caption]
AnonOps IRC / #OpIsrael[/caption]
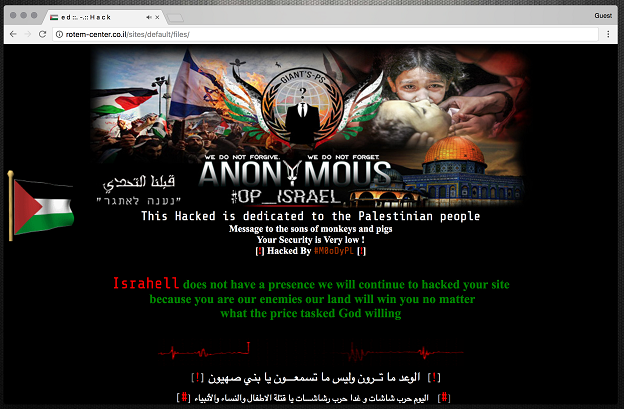
Defacements are the most common attacks seen during the operation. A defacement is when an attacker changes the visual appearance of a website by breaking into the webserver and replacing a page. This is a low level of vandalism often used to spread propaganda related to the operation. During OpIsrael dozens of small websites that are poorly maintained are temporarily vandalized with this form of electronic graffiti. Websites typically stay defaced for a few hours or until the admin realizes what happened. Website hxxp://fitwelpharma.com was targeted several times. It was originally used to host infected tools targeting OpIsrael attacks but was later defaced by Ghost Israel Cyber Army.
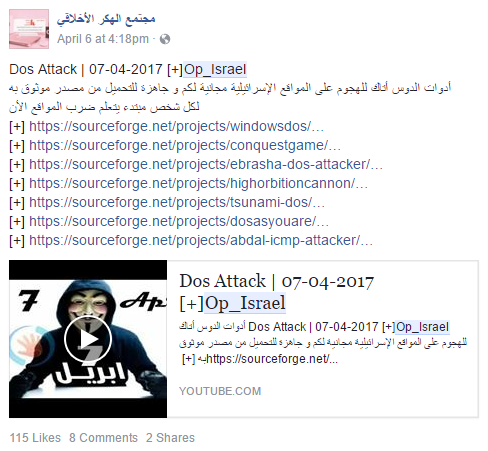
This year OpIsrael saw a limited number of DDoS attacks. Successful attacks only last a few moments as most attackers did not have enough power to keep a website offline. To add to this problem, many claims of success were false where no outage occurred. Several tools were shared leading up to April 7th, but most of these tools are outdated and easy to mitigate due to existing signatures. The Anonymous care package that was being shared inside the operation this year was a repost from 2012. Some GUI based tools shared publicly included Windows DoS, LOIC, HOIC, Tsunami, DAYA, Abdal ICMP, EbraSha DoS and An0nStr3ss.
MajHoul, aka CyberRog of Redcult, was directing potential attackers to three different tools. CyberRog was spreading three different denial-of-service tools specifically designed to be used on mobile devices. These tools where Redcult Doser, LOIC RedCult edition and RC Doors. RC Doors is a clone of the app Packet Generator in the Google Play store. These tools can generate HTTP, ICMP, UDP and TCP floods from mobile phones but are often too weak to cause major damage.
[You might also like: The Expansion of IoT since Mirai.]
[caption id="attachment_6819" align="aligncenter" width="442"]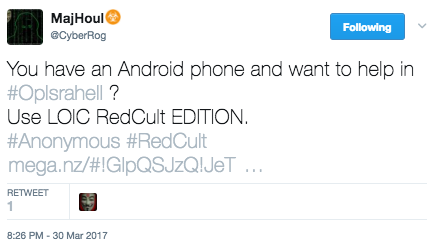 CyberRog Distributing Android DoS Tools[/caption]
CyberRog Distributing Android DoS Tools[/caption]
LOIC RedCult Edition
RedCult Doser
RC Doors
[caption id="attachment_6820" align="aligncenter" width="487"]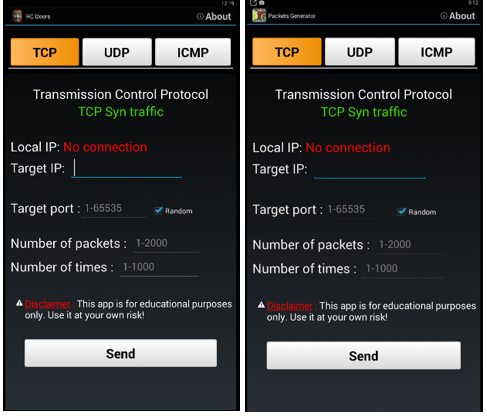 RC Doors from Red Cult (left) and Packet Generator from Google Play (right)[/caption]
RC Doors from Red Cult (left) and Packet Generator from Google Play (right)[/caption]
This year during OpIsrael there were two main actors in distributed tools for activists looking to participate, MajHoul and another user named @Eng_Hassaniashe. Eng_Hassaniashe was spreading two tools, DDoS_Ano.exe and ddos_android.apk. Both tools contained malware most likely designed to target OpIsrael attackers. DDoS_Ano.exe contained DarkKomet while ddos_android.apk contained an Android backdoor spy tool. The first site used to host these tools was fitwelpharma.com which was compromised and later defaced. Both tools where ultimately hosted on SendSpace.
[caption id="attachment_6821" align="aligncenter" width="436"]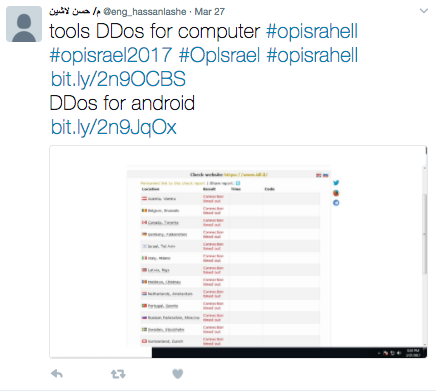 @Eng_Hassaniashe Distributing malicious tools[/caption]
@Eng_Hassaniashe Distributing malicious tools[/caption]
DDoS_Ano.exe
ddos_android
No script tools were created this year for OpIsrael. Last year HaxStroke from AnonGhost posted a series of modified Python attack scripts. This year a few attackers were seen posting links to the attack scripts BlackHorizon, Saphyra and Crescent Moon by HaxStroke. Last year SadAttack, an attack script nearly identical to the tool HTTP Unbearable Load King, also known as HULK was widely used by attackers. This year attackers also recommended the use of TorsHammer, a slow-rate HTTP POST (Layer 7) DoS tool that can be carried out through the Tor network.
[caption id="attachment_6822" align="aligncenter" width="624"]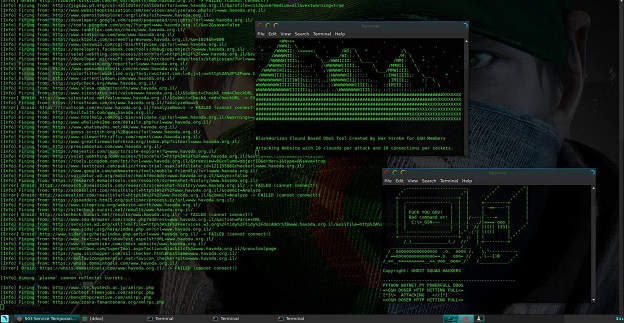 Attacker using BlackHorizon[/caption]
Attacker using BlackHorizon[/caption]
[You might also like: Don’t Fall Into the Ring of Fire]
The group MCA DDoS Team during OpIsrael claimed to have taken down Justice.gov.il but I was not able to verify their claim in real time. Moments after the tweet, MCA claimed they attacked the site but did not have enough power to keep them offline. Attacks like this are very common during this operation. Normally sites are back online before the attacker can publicly claim credit for the attack.
[caption id="attachment_6823" align="aligncenter" width="439"]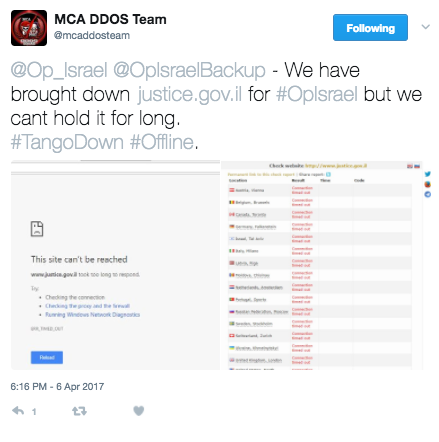 MCA DDoS Team fail to keep site offline[/caption]
MCA DDoS Team fail to keep site offline[/caption]
SQL attacks are rarely witnessed during OpIsrael. Most content leaked, such as data, during the operation is reposted material from past operations. During successful operations, attackers will use this technique to take advantage of poor application security. When application inputs are not sanitized it creates a possible vulnerability for an attacker. Attackers can modify an application’s SQL query to gain access and view unauthorized data, run remote commands on the server or drop and create objects in the database. These attacks are often launched ahead of the operations start date. The data is released during the operation to gain further attention and cause more fear.
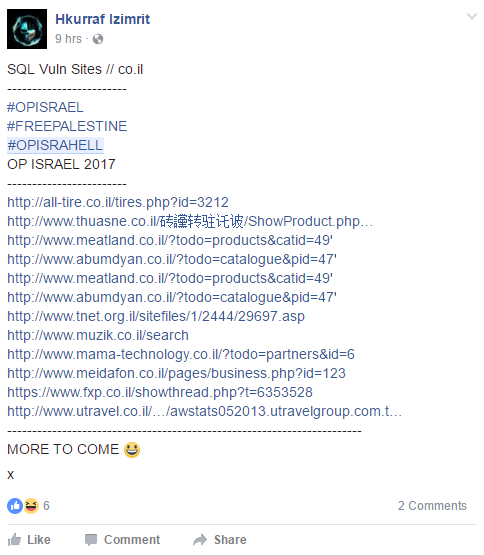
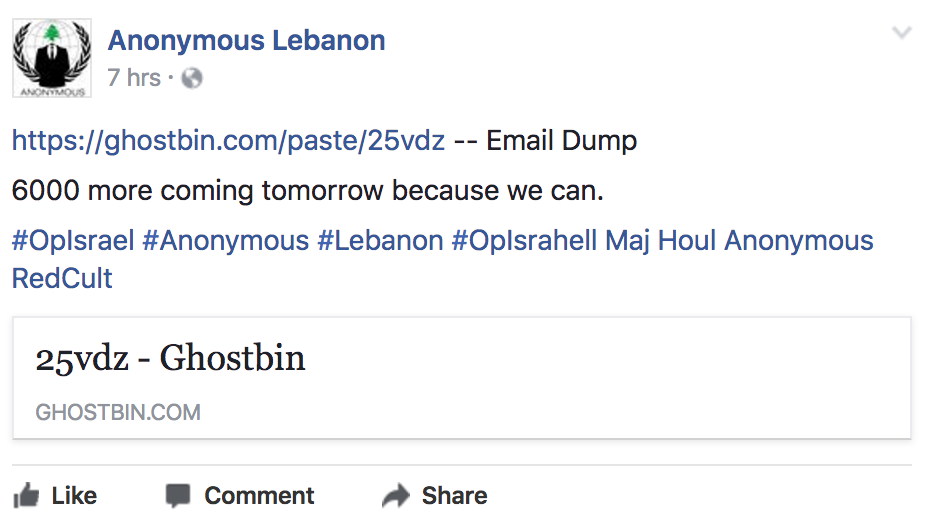
OpIsrael is full of opportunists looking to gain internet fame, eFame, based on previous hacks. These tricksters often fool the media by reposting what appears to be legitimate data. This year Anonymous Lebanon claimed to have dumped thousands of emails but upon further inspection, the two pastes are actually just a repost of a leak by Dark-Man team in May, 2013.
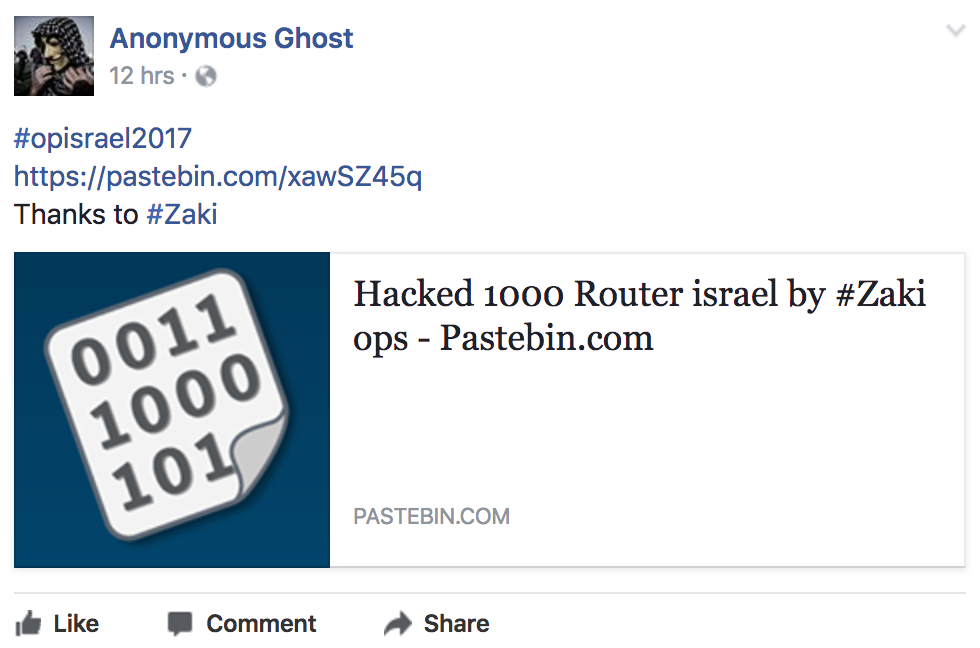
During OpIsrael this year, attacker Giant’s-ps posted a paste containing the IP addresses and credentials for over 1,000 Internet of Things (IoT) devices in Israel. These devices appear to have been brute forced with a simple password list. All of the devices listed suffer from weak credentials. Some common usernames and passwords used are support:support, Admin:Admin, guest:guest and user:user.
Other tools recommend during Anonymous operations usually include a variety of VPNs and anonymization software. This year attackers recommended the use of SaferVPN and Tor. These tools are designed to provide privacy but also to mask the origin location of the attacker. Lower level attackers will opt for free VPN services or Tor to mask their identity.
The Darknet has many uses. Sometimes attackers will use IRC’s on the Tor network or use services like Zerobin to post recent leaks and operational details. During OpIsrael 2017, the IRC channel #LaResistance on the Darknet, anonops532vcpz6z.onion:443, contained a series of dumps if you used the command !dumps. The command presented the users with several pastes found on the Darknet.
[caption id="attachment_6827" align="aligncenter" width="624"]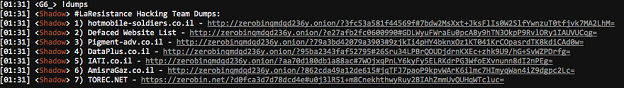 anonops532vcpz6z.onion:443 / #LaResistance[/caption]
anonops532vcpz6z.onion:443 / #LaResistance[/caption]
[You might also like: “For Educational Purposes Only”]
[caption id="attachment_6828" align="aligncenter" width="624"]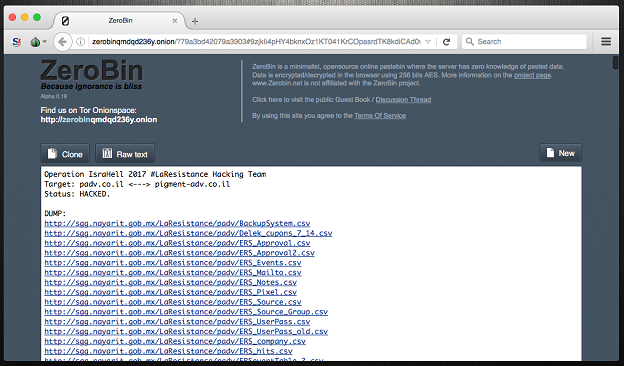 Dump from IRC channel #LaResistance[/caption]
Dump from IRC channel #LaResistance[/caption]
This year’s content produced by OpIsrael was particularly shameful for the operators. The content that was distrusted was identical to the content from 2012, with many alleged accounts participating in OpIsrael 2017 inactive or no longer existing. Additionally, some claims of successful attacks were false. Attackers posted links to new pastes containing alleged leaked information from successful hacks. Upon verification, it was determined that attackers were reposting leaks from a 2013 operation.
The tools and techniques publicly being used by Anonymous are outdated. Most of their denial-of-service attacks are conducted with old Graphical User Interface, GUI, tools for Windows and script tools mainly coded in Python, Perl or C. The attacks are often very weak and easily blocked by signatures already created for the tools.
The deeper issue with Anonymous seems to be their inability to evolve with the changing times. At one point, a few dozen kids with the Anonymous tool set was something to be concerned about. Today is a totally different landscape that includes 1Tbps attacks and massive IoT botnets. Even just a single hacker with a few compromised servers and a list of open resolvers can pack a punch. The old attackers from inside the collective have moved on and no one is teaching anyone anymore.
Attackers that are still launching DDoS attacks under the name Anonymous do so quietly and by themselves. They no longer need to control and orchestrate an attack from IRC. And still, with lone wolves out there with their IoT botnets, we still don’t see the network-crippling attacks promised by OpIsrael every year.
Next year will be a make-or-break moment for the operation. If Anonymous fails to follow through again, their threats will likely not be taken seriously in the future. Defacing small, low traffic websites, falsely claiming DDoS attacks and reposting leaked data from previous years has damaged the collective reputation for OpIsrael.
To read the full threat alert, click here.

Read the 2016–2017 Global Application & Network Security Report by Radware’s Emergency Response Team.
Download Now