The New Frontier of DDoS Attacks is Serverless
Hackers are now using serverless computing as a means of launching DDoS attacks. This new trend has significant implications regarding the scale of these attacks and the complexity of mitigating them.
Radware recently mitigated a large-scale and prolonged web DDoS attack against one of our customers. The attack was remarkable not just for the size and duration of the attack, but also because it was launched by the serverless computing infrastructure of a large public cloud provider.
We believe that this attack is a harbinger of a greater trend — the adoption of serverless computing by DDoS attackers. The significant problem is that beyond the technical novelty of this approach, it introduces the potential for bigger attacks that are more easily launched and more difficult to mitigate.
A Short History of DDoS Attacks
Denial of Service (DoS) attacks have been around since the dawn of computing. The very first DoS attack occurred as early as 1974 by a 13-year-old middle-school student. He launched the attack against the PLATO mainframe at the University of Illinois Urbana-Champaign’s Computer-Based Education Research Laboratory (CERL).
While that attack was more a prank and experiment by a curious teenager, Denial of Service (DoS) attacks have evolved over the years into large-scale and technically complex criminal activities. Moreover, hackers have learned to use globally distributed botnets to launch large-scale attacks and complicate mitigation efforts, hence the additional ‘D’ in DDoS, standing for Distributed Denial of Service attacks.
Today, hacker groups and criminal rings routinely maintain large-scale, globally distributed botnets to launch DDoS attacks. These botnets are typically based on both compromised PCs and vulnerable IoT (internet of things) devices, including routers, IP cameras, refrigerators, and even electric vehicles.
The downside of this approach, however, is that building such a botnet requires considerable effort by hackers. They have to scan for vulnerable devices, access them, find vulnerabilities to exploit and develop binaries that will run on the devices. Moreover, maintaining such a botnet can be surprisingly difficult, as hacker groups often compete with, and steal, each other’s compromised devices.
Mitigating a Serverless DDoS Attack
On April 21st, 2023, Radware detected a DDoS attack targeting one of our customers, a global communications provider protected by our Cloud Application Protection service.
The attack was a fairly sizable HTTPS GET flood with dynamic parameters. It consisted of four major peaks. Each peak was over 110K requests per second (RPS) and reached as high as 140K RPS. While it wasn’t the largest attack we’ve seen, it was certainly significant and could have easily brought down unprotected web applications. Also, it was a very persistent attack, lasting nearly 3 days.
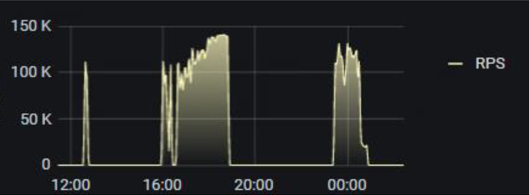
Figure 1: Incoming waves of DDoS attack traffic originating from serverless computing services, peaking at over 140K requests per second (RPS)
The attack was remarkable for more than just the size and persistence of the assault. It didn’t originate from a botnet, but from the serverless computing service of a large public infrastructure provider — Cloudflare.
Radware observed large numbers of requests originating from IP ranges associated with Cloudflare Workers, the company’s serverless computing service.
Attack traffic came from both multiple IP subnets and multiple geographies worldwide. When combined with the dynamic nature of the HTTPS GET requests, mitigating the attack using traditional DDoS defense tools would have been very challenging at best.
Radware mitigated the attack using our behavioral-based web DDoS protection algorithms combined with custom signatures put in place by our Emergency Response Team (ERT).
While the attack was successfully mitigated, it provided a glimpse of future trends and how hackers are beginning to leverage serverless computing to launch DDoS attacks.
Serverless Computing has Advantages for Hackers, Too
Serverless computing has been one of the hot trends of the past few years. Organizations and developers are enticed by its decreased overhead, fast deployment and the scalability it offers, and many infrastructure-as-a-service (IaaS) providers offer it, including AWS, Azure, Cloudflare, and others.
The problem, however, is that many of the advantages serverless computing offers developers also apply to hackers.
Compared to the overhead of maintaining their own botnets, serverless computing offers hackers the following key advantages:
- They don’t need an infrastructure of their own. Serverless computing removes from hackers the burden of maintaining their own botnet infrastructure (and defending it against other hackers), which allows them to use a publicly available infrastructure.
- It’s easier to create. With serverless code, hackers no longer need to detect exposed devices, exploit them and create full-stack binaries to run on routers, IP cameras, and other IoT devices. With serverless computing, all that’s needed is for the hacker to write high-level application code; the infrastructure provider takes care of the rest.
- They have instant scale at their fingertips. The instant scalability afforded by serverless computing enables attackers to launch devastatingly massive attacks with ease.
Serverless Computing Complicates Mitigation Efforts
Apart from offering attackers opportunities to enhance the potency of DDoS attacks, serverless computing also presents the following key challenges to defenders, which complicates mitigation efforts:
- They are large in scale. The scalability of serverless computing services allows attackers to create large-scale attacks with ease, which means organizations will have to protect against larger attacks more than ever.
- They are highly distributed. With serverless scripts, attackers can create highly distributed attacks that come from multiple sources at once and utilize large pools of IP addresses and geographic locations. This means traditional DDoS mitigation tools, such as access control lists (ACLs) or geo-blocking, will be rendered useless because they won’t be able to cover all attack sources.
- They can hide behind legitimate traffic. By using publicly available serverless computing services offered by cloud infrastructure providers like AWS, Azure, Cloudflare, and others, attackers can hide behind legitimate traffic that also originates from these networks. This makes distinguishing between legitimate and attack traffic very difficult and attempt to completely block those providers means large numbers of requests by legitimate users or services will be blocked, as well. This results in high false positive rates.
- Application layer requests. Serverless computing eliminates the need for developers to create the lower levels of application code (e.g., operating system, network interfaces, etc.) and focus directly on application layer code. This enables attackers to easily write scripts that target the application layer and bypass the traditional network layer. This means they can create DDoS attacks that home in on the business logic of targeted web applications.
These challenges brought about by serverless-based DDoS attacks mean that traditional DDoS mitigation techniques won’t block these sophisticated attacks. That’s why organizations must seek new ways to protect themselves.
You Need Behavioral Detection To Cut Through the Noise
While serverless computing makes writing applications and services more easily, it also enables attackers to launch DDoS attacks that are not only larger, but harder to mitigate. The characteristics of serverless scripts launched from public infrastructure-as-a-service (IaaS) providers make it difficult to distinguish between legitimate and malicious traffic.
This means organizations need mitigation techniques that look beyond the IP address, source or geo-location. They need a solution that can distinguish between good and bad requests based on traffic characteristics.
For more information about how Radware can protect your organization from cyber-attacks, including DDoS attacks launched via serverless computing, reach out to our cybersecurity professionals here. They would love to hear from you. And click here to get more information about Radware’s industry-leading DDoS Protection solutions.



