A web application firewall is a type of firewall designated to protect web applications. It continuously inspects HTTP traffic to detect and block malicious traffic and web application attacks. This can include access violations, API manipulations, advanced HTTP DDoS attacks, cookie poisoning, and many more.
The web application firewall (WAF) marketplace is diverse, with various deployment options based on an organization’s application and security requirements. There are three primary types of WAFs: a cloud-based WAF, software-based WAF, and hardware-based WAF. Each type of WAF has its own advantages and disadvantages.
Lastly, WAFs are increasingly part of a larger application security strategy: web application and API protection (WAAP). Originally coined by Gartner, WAAP defines the evolution of the WAF marketplace into a more comprehensive, unified approach to web application security versus the outdated, siloed strategy of using a collection of heterogenous security tools. WAAP is comprised of four core features:
This article reviews the three primary types of WAFs, advantages and disadvantages of each type and who should consider each type.
TABLE OF CONTENTS
There are two types of cloud-based WAF deployments: inline and out of path
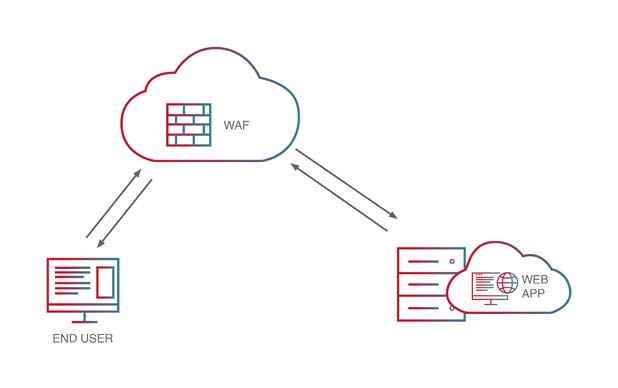
In-line cloud-based WAF deployment
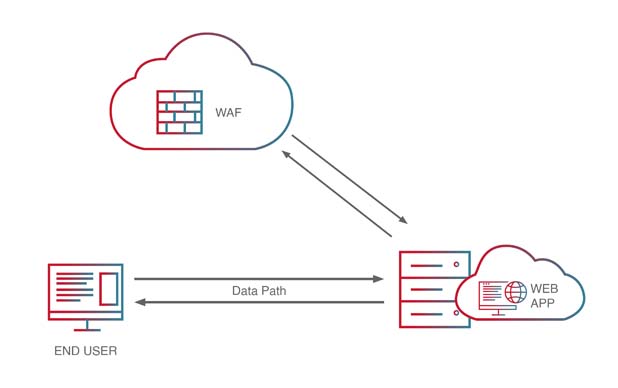
Out-of-path, API-based cloud WAF deployment
Three Different WAF Deployment Types
| Cloud-Based WAF |
Software-Based WAF |
Hardware-Based WAF |
| A cloud-based WAF is a managed by a service provider that offers the WAF as a security-as-a-service. |
A software-based WAF is a virtual applicance that is hosted either locally or in the application cloud environment . |
A hardware-based WAF is deployed through a hardware appliance, installed locally within the network close to the web application servers. |
A cloud-based WAF is an affordable and easy to implement turnkey deployment option that can be rapidly deployed. Cloud-based WAFs have minimal upfront costs and are typically subscription based. Cloud-based WAFs have access to constantly-updated threat intelligence, and may also offer managed services to help you define security rules and respond to attacks as they happen.
Ideally, a cloud-based WAF should provide the option to be deployed either in-line or as an API-based, out-of-path (OOP) service. An API-based, OOP deployment offers several unique advantages that enable it to be optimized for multi-cloud environments, on-premise environments, hybrid environments, etc.
In recent years, cloud-based WAFs have become the predominant deployment type for the majority of organizations globally for reasons listed below.
Who Should Use A Cloud-Based WAF
Cloud-based WAFs have become a popular choice for organizations of all sizes, from enterprises to small businesses, as they’re capable of providing high levels of security with minimal upfront investment costs and without the need for extensive in-house security expertise.
The Advantages and Disadvantages of a Cloud-Based WAF
Cloud-based WAFs have numerous advantages and a few disadvantages that a prospective buyer should consider.
Advantages
-
Affordable
-
Easy to implement/deploy
-
Minimal upfront investment
-
Consistent levels of protection/centralized management and reporting across any/all environments.
-
Subscription-based or security-as-a-service subscription
-
Automatically updated by third-party provider
-
Best deployment option for multi-cloud environments
Disadvantages
-
Certain industries (such as government or defense) are required to maintain all infrastructure and data on-premise, thereby eliminating cloud-based WAFs as a potential deployment option
-
The majority of cloud-based WAFs require redirection of application traffic, thereby increasing the chance of latency.
A software-based WAF is an alternative to a hardware-based WAF. A software-based WAF runs the WAF as a virtual appliance or an agent, either locally (on-premise), in a private cloud or in a public cloud.
Additionally, there are other WAFs specifically designed to be embedded in container-based microservices environments such as Kubernetes to protect east-west traffic.
Who Should Use A Software-Based WAF
Software-based WAFs are typically leveraged by organizations with applications hosted in private and/or public cloud data centers. They can also be popular with organizations that don’t have the budget and/or ability to support hardware-based WAFs, but still want to manage their own WAF or are reluctant to deploy a cloud-based WAF.
The Advantages and Disadvantages of a Software-Based WAF
Software-based WAFs have numerous advantages and a few disadvantages that a prospective buyer should consider.
Advantages
-
Additional customization options (if you have the in-house security expertise and/or resources)
-
Lower upfront, deployment and ongoing maintenance costs than a hardware-based WAF (see below)
Disadvantages
-
Complex deployment
-
Requires installation of code on application server
-
Relies on application server resources to run effectively
-
Updates must be managed by the end user
A hardware-based WAF (or commonly referred to as network-based WAF) is installed locally on a network. These are more often than not the most expensive forms of WAFs as they require maintenance and storage space. Their primary purpose is to minimize latency.
In recent years, hardware-based WAFs have become increasingly obsolete as cloud-based WAFs have become the predominant deployment type.
Who Should Use A Hardware-Based WAF
Hardware-based WAFs are commonly leveraged by large organizations who have the budget and headcount to manage on-premise appliance and IT infrastructure. Additionally, organizations will leverage hardware-based WAFs when application speed and performance is critical, or when running sensitive applications in on-premise environments, such as government institutions, national security agencies, the defense industry, etc.
The Advantages and Disadvantages of a Hardware-Based WAF
Hardware-based WAFs have numerous advantages and a few disadvantages that a prospective buyer should consider.
Advantages
-
Reduced latency
-
Highly customizable
-
Completely air-gapped
Disadvantages
-
Large upfront investment
-
Ongoing maintenance costs
-
High IT operational costs/headcount
-
Updates and maintenance managed by the end user
| |
Cloud based WAF |
Software based WAF |
Hardware based WAF |
| Suitable for |
Organizations of all sizes |
Medium to large-size organizations |
Large organizations |
| Advantages |
- Affordable
- Easy to implement/deploy
- Minimal upfront investment
- Consistent levels of protection/centralized management and reporting across any/all environments.
- Subscription-based or security-as-a-service subscription
- Automatically updated by third-party provider
- Best deployment option for multi-cloud environments
|
- Additional customization options (if you have the in-house security expertise and/or resources)
- Lower upfront, deployment and ongoing maintenance costs than a hardware-based WAF (see below)
|
- Reduced latency
- Highly customizable
- Completely air-gapped
|
| Disadvantages |
- Certain industries (such as government or defense) are required to maintain all infrastructure and data on-premise, thereby eliminating cloud-based WAFs as a potential deployment option
- The majority of cloud-based WAFs require redirection of application traffic, thereby increasing the change of latency.
|
- Complex deployment
- Requires installation of code on application server
- Relies on application server resources to run effectively
- Updates must be managed by the end user
|
- Large upfront investment
- Ongoing maintenance costs
- High IT operational costs/headcount
- Updates and maintenance managed by the end user
|
| Recommended Solution |
Cloud WAF Service |
Kubernetes WAF |
AppWall |