A web application firewall (WAF) is a hardware appliance, virtual appliance or cloud-based service that resides in front or before the web-facing applications to detect and protect against a variety of malicious attacks. A WAF is focused on web application traffic (HTTP/S) and protects applications in internet-facing zones of the network.
A WAF can use many techniques to understand whether traffic should be allowed to pass through to an application or should be blocked, including behavioral algorithms (machine learning and a positive security model) or a negative security model.
Lastly, WAFs are transitioning from standalone tools into fully-integrated Web Application and API Protection (WAAP) offerings that include a suite of capabilities, including protecting APIs, bot management and mitigation capabilities, application Layer 7 DDoS protection, web application security, and more.
Learn more in our detailed guide to WAF security.
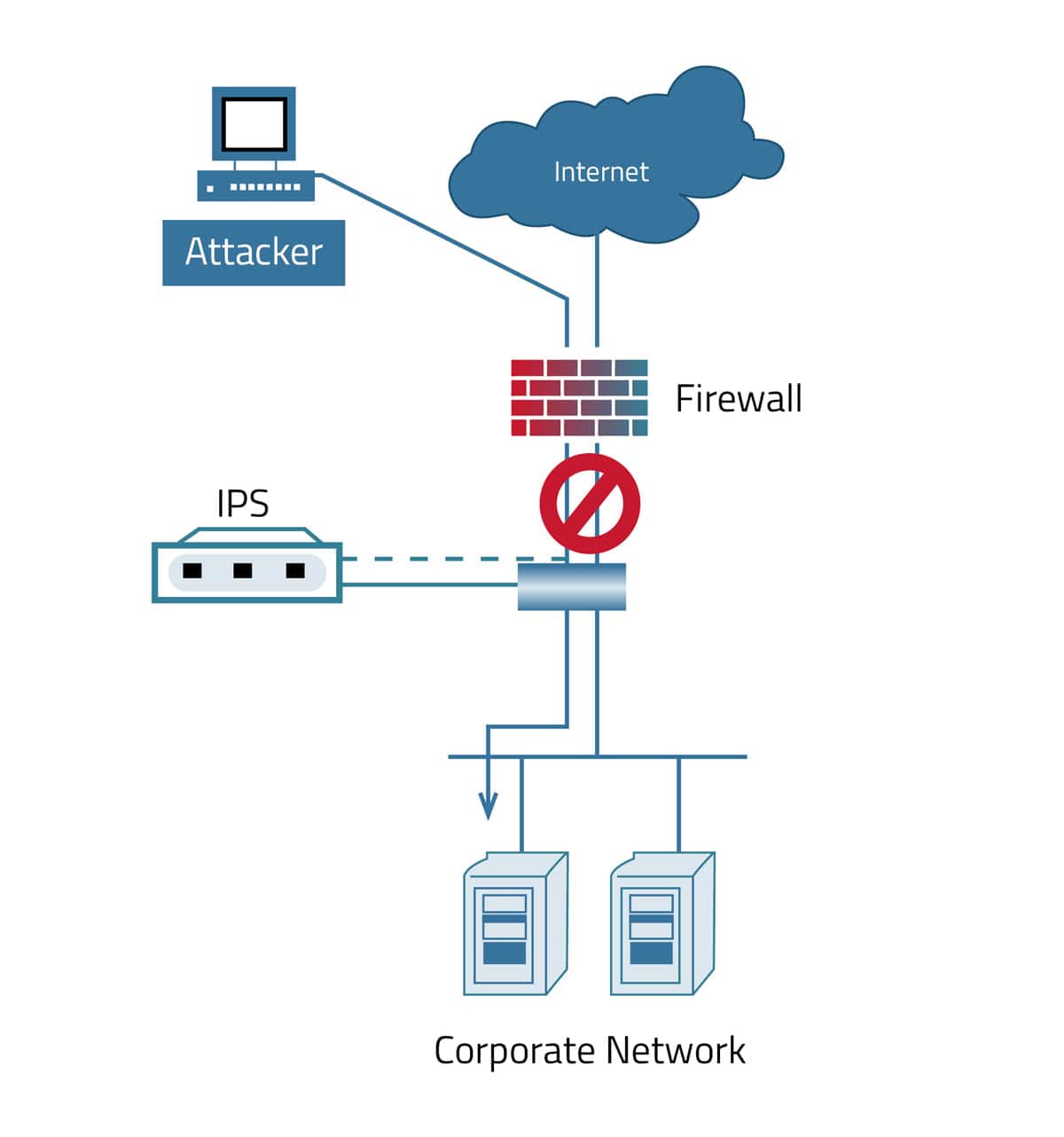
An intrusion prevention system (IPS) is a network security device that monitors a network at strategic points to scan for malicious activity and report, block or drop the malicious traffic as configured. The IPS are usually deployed behind a firewall in a network and before a WAF.
An IPS compliments a WAF/WAAP solution and is typically deployed together. WAF deployments protect web application traffic, while IPS deployments scan and protect at the network level by inspecting all packets. An IPS is typically deployed inline to incoming traffic, scans for threats in most network protocols, and works at OSI Layer 4-7. WAF and WAAP solutions are mainly deployed behind an IPS for incoming traffic and scan for threats to applications at OSI Layer-7.
Comparison Table: WAF vs IPS
| |
WAF |
IPS |
| What they do? |
Protect web applications against layer-7 attacks |
Protect networks |
| Scope |
OSI Layer 7 sessions |
OSI Layer 4-7 packets |
| Protocols |
HTTP/HTTPS |
Network protocols |
| Deployment |
Inline or out-of-path |
Mostly Inline |
| Encrypt/Decrypt |
Yes, SSL/TLS |
No |
| Deployment |
Inline or out-of-path |
Inline |
Additional Resources