Web application firewall (WAF) rules are used to define how to inspect HTTP/HTTPS web traffic (requests) to an application, where and what parameters and conditions to look for in the request, and what action the WAF should take when a request matches those definitions. A set of security rules constitutes a security policy.
As applications constantly evolve with new services and pages alongside a constantly growing threat landscape, security policies need to be updated regularly. Updating a security policy means updating and finetuning the set of rules that comprise that security policy to answer the most relevant security threats and needs of the application.
Learn more in our detailed guide to WAF security.
Each WAF comes with a basic set of rules out of the box. In most cases these rules are based on certain blocklists as per known signatures, bad reputation IP lists, etc.
The better the WAF, the broader and more robust, and more relevant the pre-defined ruleset would be to answer to the most current cyber security threats. Although these rules are pre-defined, WAF vendors must constantly and continuously update them to ensure their customers are protected against the very latest threats.
Advanced WAFs allow analysts, security experts, and other users to define advanced rules with granular customization options to improve their applications’ security and performance and reduce network load on application servers.
Here are some examples of custom rules:
-
Block access to specific sections of a website based on IP address or Headers
-
Prevent search engine bots from accessing a website
-
Redirect traffic to a maintenance page
Rules are usually comprised of rule metadata, a set of conditions, and an action.
Metadata
For each rule, you can set a rule name and a rule description. The rule metadata information is used to describe the rule and is also presented as part of the security event that is generated when a rule is triggered. You can also set the rule state to be enabled or disabled.
Conditions
Conditions are used to trigger the rule by matching a condition to the content of the request. For each rule, you can set multiple conditions.
Action
An action will take place in case the requests matched the conditions described in the conditions section of the rule. The available actions are in dependent on the rule type that is selected.
Rules are usually arranged according to their action type into four major groups:
Priority
In most industry-standard WAFs HTTP/S Requests are matched against rules according to a predefined priority. For instance, Redirect Rules → Security Rules → Rewrite Rules and within each group, you can set the internal priority of existing rules within that group
Radware WAF security policies are comprised of two types of rules – Pre-defined rules and Custom Rules.
Pre-defined rules
This set of rules is what makes Radware WAF a unique turn-key solution. Some of these rules are automatically generated by Radware’s advanced machine-learning algorithms and the Radware data lake, some are updated by Radware’s team of cyber experts at the backend, and some are generated by Radware’s ERT Active Attackers Feed (e.g., Radware’s global intelligence, honey pots, and deception networking, device fingerprinting, etc.)
These rules are dynamic and constantly adapt to protect against the most recent threats. Here are a few types of Radware’s predefined WAF rules:
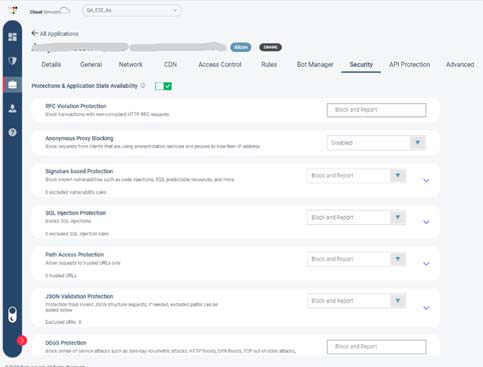
Custom rules
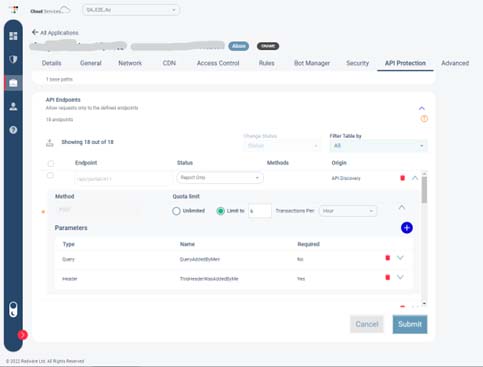
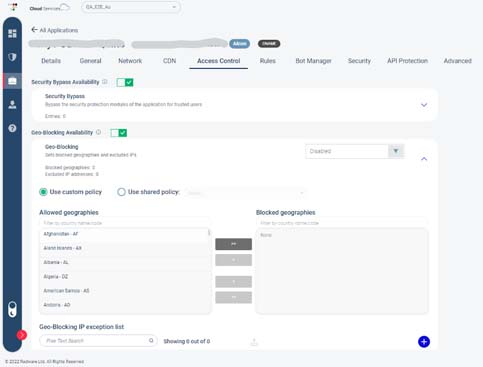
Radware custom WAF rules are advanced rules that contain configurations and settings for advanced application traffic control and manipulation. Here are Radware custom rules’ six main categories:
The best security coverage with minimal impact on legitimate traffic is when WAFs combine negative (defining what’s forbidden and accepting the rest) and positive security models (defining what is allowed and rejecting the rest). Combining the two models allows granular and accurate policy definitions, therefore avoiding false positives and false negatives. The negative security model protection is based on up-to-date signatures against known vulnerabilities that provide the most accurate detection and blocking technology of application vulnerability exploits. The positive security model is useful in stopping zero-day attacks. The positive security rules and mechanisms allow the definition of value types and value ranges for all client-side inputs, included encoded inputs and within structured formats such as XMLs and JSONs. The positive security profiles limit the user input to only the level required by the application to properly function, thus blocking zero-day attacks.
The use of the aforementioned security models requires defining policies and rules which can sometimes be labor intensive. Building a security policy usually demands rigorous work on the part of the administrator, while still leaving a system potentially open to attack due to human errors. Advanced WAF solutions should be able to use automation to reduce the cost of ownership and avoid human errors associated with such manual processes.
What Is Auto-Policy Generation
To reduce the effort involved in creating a positive security policy and avoid the risks of human errors, A WAF should provide auto-policy generation based on machine-learning capabilities for automatic rule definition and maintenance. Auto-policy generation is often based on the ability to identify and profile legitimate application transactions and creating “allow” rules based on it.
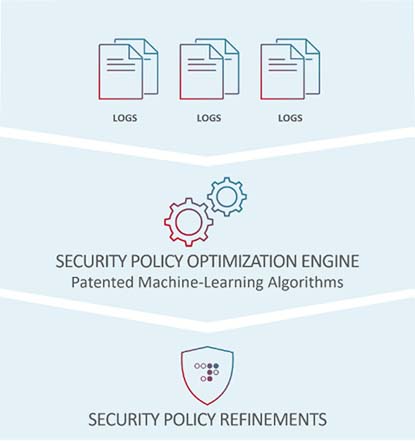
What Is Continuous Policy Optimization
It is critical to constantly optimize security policies to maintain high-security levels and minimize false positives so that security won’t stand in the way of legit traffic. To achieve both without high operational costs and manual intervention requires an application protection solution capable of automatically reviewing log files on a regular basis and artificial intelligence
-
Redirect Rules – used for redirecting traffic to another location when conditions are met
-
Security Rules – used for blocking or allowing traffic when conditions are met.
-
Rate limiting Rules – used for controlling traffic volumes as per set thresholds
-
Remove/Rewrite/insertRules – usually used for modifying the HTTP request and response components when conditions are met.
-
Redirect rules – used for changing headers to redirect traffic to another location when conditions are met
-
Security & Access Control rules – used for blocking or allowing traffic when conditions are met. Within this group of rules, you would find Geo blocking and security bypass rules
-
Rate limiting Rules – used for controlling traffic volumes as per set thresholds
-
Response Delivery rules – used for modifying (Remove, Rewrite, Insert) the headers of the server responses when the conditions of rules are met.
-
API protection rules – used for setting request quotas from specific API endpoints or blocking them altogether, as well as setting specific API conditions to be met such as type, header, body, path, parameters, etc.
-
Bot management rules – used for configuring which action to be taken if a malicious bot was detected, according to the type of bot that was identified
Additional Resources