What is a Spam Bot?
A spam bot is a type of automated program that can enable or deliver spam, including junk emails, irrelevant comments and posts on user-fillable forms and discussion forums, and variations of these spamming activities.
The Open Worldwide Application Security Project® (OWASP) defines the activity of spamming as “malicious or questionable information addition that appears in public or private content, databases or user messages.”
In this article:
Spammers frequently send out large volumes of emails to try to install malware or steal account information via phishing attacks. They may also use spoofed email addresses to make it appear as though the messages originate from a legitimate source that the recipient may know or use.
Spammers utilize bots to post spam in forms or user-generated comment forums by looking for and posting in discussions that may not require an account. If an account is required to post comments, spam bots can also create fake user accounts and post comments.
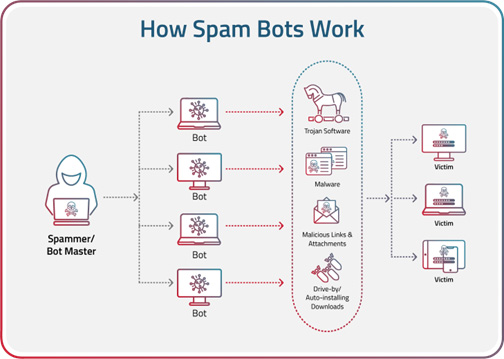 Infographic: How Spam Bots Work
Infographic: How Spam Bots Work
Email Spam Bot
Email spam bots are automated programs designed to send bulk unsolicited emails, targeting users with phishing attempts, advertisements, or malware. They often scrape email addresses from websites, forums, and public directories using specialized web crawlers. These bots can exploit vulnerabilities in email servers or send emails through hijacked accounts, further complicating detection.
To evade spam filters, these bots employ techniques like address spoofing, making their messages appear as if they originate from legitimate and trusted senders.
Form Spam
Form spam is one of the chief types of spam targeting real estate portals, classified ad listings, job search sites and businesses with web forms. It involves bots that constantly post spam, affecting user interactions and makes it hard for marketing teams to get accurate lead generation information.
Social Media Spam Bots
Social media spam bots operate by infiltrating platforms like Twitter, Instagram, and LinkedIn, exploiting their popularity to spread misleading or harmful content. These bots can create fake profiles en masse or take control of compromised accounts to post spammy links, comments, or messages.
Often mimicking real users with stolen profile photos and personal details, they aim to gain trust and drive engagement with their deceptive posts. Social media spam bots frequently promote scams, phishing links, sexual content, fake giveaways, and advertisements. They can also distort platform metrics by generating fake likes, shares, and followers.
SMS Spam Bots
SMS spam bots are automated systems that deliver spam messages to large groups of recipients via text messaging services. They exploit vulnerabilities in telecommunications systems to send fraudulent offers, phishing links, or unsolicited advertisements.
These bots frequently impersonate legitimate entities, such as banks, government agencies, or retail brands, to deceive recipients into sharing personal information or clicking on malicious links. SMS spam bots are particularly dangerous because users are more likely to trust and act on text messages than emails.
Comment and Forum Spam Bots
Comment and forum spam bots target websites with user-generated content, such as blogs, discussion boards, and social media comment sections. These bots are programmed to post irrelevant or harmful content, often including links to phishing sites, low-quality products, or malicious downloads.
By exploiting open comment systems or bypassing weak CAPTCHA protections, they can flood platforms with spam at scale. This behavior disrupts meaningful conversations, discourages user engagement, and imposes a significant moderation burden on administrators.
Spam bots can have several negative impacts on a website or organization:
Reduce User Engagement and Traffic: Websites and applications that have high volumes of comment and form spam usually encounter lowered user engagement and harm to their brand and user loyalty.
Skew Traffic Analytics: Spam on forms hinders websites and marketers from getting accurate data on traffic statistics, which leads to difficulties in decision making and developing effective strategies.
Slow Website and Application: Spam bots can reduce the performance of websites and applications by overloaded servers and increasing page and application load times. Spam botnets have also been known to create conditions similar to a DDoS attack.
Increase Infrastructure Costs and Waste of Resources: Increase Infrastructure Costs and Waste of Resources Spam bot traffic generally leads to higher infrastructure and network expenditure, leading to wasted time and effort to filter spam leads and manually block spammy accounts.
Lower Search Engine Rankings: Search engines consider spammy websites and applications less useful to their users. They regularly downgrade their search rankings or even remove these web pages from search results.
Fake Registrations and Leads: Spammers use spam bots to post form spam, i.e., junk information on lead generation forms commonly used by marketers to solicit inquiries.
Behavioral Indicators
Spam bots typically exhibit repetitive and unnatural behaviors that stand out from genuine user activity. For instance, they might post identical or highly similar content across multiple platforms, forums, or posts within a very short time frame, often targeting public sections that require minimal authentication.
Bots frequently display relentless activity patterns, such as posting, commenting, or sending messages around the clock without pauses or varying time intervals, which is inconsistent with human behavior. Additionally, spam bots often ignore conversational context, failing to engage in meaningful interactions, instead focusing solely on promoting links, ads, or phishing attempts.
Account Characteristics
Spam bot accounts often share specific characteristics that make them easier to identify upon closer inspection. These accounts might use auto-generated usernames comprising random strings of letters, numbers, or nonsensical patterns. Their profile photos, if present, may be stock images or stolen from other sources, making them inconsistent with the user’s claimed identity.
Many bot accounts lack detailed profiles, showing minimal personal information, few or no posts, and little to no engagement with other users. They often appear newly created and show signs of mass production, such as a large batch of accounts registered on the same day or with sequential email domains. Furthermore, their friend or follower lists might include only other suspicious or inactive accounts, further indicating automated origin.
Content Analysis
The content generated by spam bots often includes key markers of automation and low quality. These posts are frequently repetitive, sharing identical text or links across different platforms or threads.
The language used is often generic, impersonal, and designed for mass appeal, with no tailoring to the context of the discussion or audience. Spam bot posts commonly use attention-grabbing tactics, such as all caps, excessive exclamation points, or an overload of emojis, to lure readers into clicking their links. However, this is changing with the use of large language models (LLMs), which can generate more natural-looking communications.
Additionally, links shared by bots often lead to dubious destinations, including phishing websites, malware downloads, or counterfeit product pages. By examining the language structure, keyword usage, and destination URLs of suspicious posts, spam bots can often be distinguished from genuine contributors.
Traffic Analysis
Traffic analysis can provide clear evidence of spam bot activity by revealing unusual patterns and anomalies. Spam bots frequently cause unexpected spikes in web traffic, form submissions, or account registrations that deviate sharply from normal user behavior. These spikes often lack the natural ebb and flow seen with legitimate user activity, such as peaks during business hours.
Bots may generate high bounce rates, where visitors leave a page almost immediately after landing, suggesting low engagement and automated interaction. Traffic originating from improbable geographic regions or a concentration of unusual IP addresses can also indicate bot activity, especially if tied to known proxy servers or data centers.
However, botnets, which involve multiple bots working in coordination, can create a distributed pattern of visits from seemingly random locations, complicating detection.
Despite many advances in the long-running battle against form spam, spam bot developers are constantly upgrading bot programs to make them exhibit certain human-like patterns to evade detection by conventional security systems.
Recommended actions to stop spam include:
1. Field Validations
Some web forms have built-in field validation that can help control fake submissions to some extent. This helps automatically reject invalid email IDs and those known to carry out form spam.
3. Crypto Challenge (CAPTCHA-less mitigation)
Using Radware’s Crypto Challenge mitigation, users can enjoy a seamless browsing experience without having to solve a CAPTCHA. Machines that run bots are presented with increasingly difficult challenges to solve. This effectively turns the tables on attacks due to the high computing cost of trying to maintain a bot attack against such a bot mitigation system.
2. CAPTCHA and ReCAPTCHA
CAPTCHAs and variations such as Google reCAPTCHA are now widely deployed to validate genuine users during form fills. These systems require users to perform tasks that are simple for humans but difficult for bots, such as identifying objects in images, solving puzzles, or recognizing distorted text. Modern reCAPTCHA versions are less intrusive, using behavioral analysis to determine if a user is a human without requiring active input.
However, tests that differentiate between bots and humans can also be solved or bypassed with the help of software tools, browser extensions and outsourced teams of solvers who are paid based on how many CAPTCHAs they solve.
4. Rate Limiting
Rate limiting involves setting restrictions on how frequently a user or IP address can perform specific actions within a given timeframe. For example, it can limit the number of form submissions, login attempts, or comments a user can make per minute.
This method is effective against simple bots that rely on high-speed automation to flood websites with spam. Rate limiting is implemented at the server level, ensuring that traffic exceeding normal usage patterns is throttled or blocked.
5. Bot Prevention Protocols
Bot prevention protocols combine various security measures to create an environment that is hostile to automated traffic. These protocols often include tools like JavaScript challenges, device fingerprinting, and IP reputation checks to detect and block bots.
Device fingerprinting analyzes unique characteristics of the device and browser accessing the website, such as screen resolution, installed plugins, or user-agent strings, to identify patterns associated with bots. IP reputation services track known malicious IPs and prevent them from accessing the site.
6. Web Application Firewalls (WAFs)
A Web Application Firewall (WAF) acts as a barrier between a website and incoming traffic, filtering requests based on predefined security rules. WAFs are effective at detecting and blocking bots by analyzing request headers, patterns, and behaviors. They can detect common indicators of bot activity, such as irregular traffic patterns, missing headers, or repeated access attempts from the same IP range. WAFs can also be configured to block requests from known botnet IPs.
WAFs can stop basic bots that are more programmatic in their function and can be easily detected. On the other hand, WAFs are not designed to reliably detect the latest, most sophisticated bots that are programmed to exhibit human-like behavior to evade detection.
7. Bot Mitigation Solutions
Bot mitigation solutions are specialized tools or platforms designed to detect and prevent advanced bot activity. These solutions use a combination of heuristics, machine learning, and behavior analysis to identify bots with high accuracy. They can distinguish between human users and sophisticated bots that attempt to mimic human behavior.
Features such as anomaly detection, traffic scoring, and geolocation tracking allow these systems to respond dynamically to evolving bot threats. Many bot mitigation solutions also provide detailed analytics, enabling organizations to understand bot behavior and refine their defenses over time.
Radware offers advanced bot mitigation that has received top scores from clients and consistent accolades from respected analyst organizations:
Bot Manager
Radware Bot Manager is a multiple award-winning bot management solution designed to protect web applications, mobile apps, and APIs from the latest AI-powered automated threats. Utilizing advanced techniques such as Radware’s patented Intent-based Deep Behavior Analysis (IDBA), semi-supervised machine learning, device fingerprinting, collective bot intelligence, and user behavior modeling, it ensures precise bot detection with minimal false positives. Bot Manager provides AI-based real-time detection and protection against threats such as ATO (account takeover), DDoS, ad and payment fraud, and web scraping. With a range of mitigation options (like Crypto Challenge), Bot Manager ensures seamless website browsing for legitimate users without relying on CAPTCHAs while effectively thwarting bot attacks. Its AI-powered correlation engine automatically analyzes threat behavior, shares data throughout security modules and blocks bad source IPs, providing complete visibility into each attack. With a scalable infrastructure and a detailed dashboard, Radware Bot Manager delivers real-time insights into bot traffic, helping organizations safeguard sensitive data, maintain user trust, and prevent financial fraud.
Account Takeover (ATO) Protection
Radware Bot Manager protects against Account Takeover attacks, and offers robust protection against unauthorized access to user accounts across web portals, mobile applications, and APIs. Utilizing advanced techniques such as Intent-based Deep Behavior Analysis (IDBA), semi-supervised machine learning, device fingerprinting, and user behavior modeling, it ensures precise bot detection with minimal false positives. The solution provides comprehensive defense against brute force and credential stuffing attacks, and offers flexible bot management options including blocking, CAPTCHA challenges, and feeding fake data. With a scalable infrastructure and a detailed dashboard, Radware Bot Manager delivers real-time insights into bot traffic, helping organizations safeguard sensitive data, maintain user trust, and prevent financial fraud.