Being caught up in all the events and media attention stemming from the Russo-Ukrainian conflict, one could forget that there is still activity outside the realm of the war. True, the war shifted the focus and priorities of the nations and some crime groups alike, but others went on with their business as usual. The war, and its repercussions on the threat landscape, did not entirely eliminate pre-existing threats. I would argue that some threats are showing potential for growth in the shadow of the war. There is an upside or opportunity for rogue, organized and nation-linked agents to roam undetected and even accelerate their offensive operations.
This is the third and final blog in our three-part series, which was written to shine a light on cyber activities in the first half of 2022. This particular blog covers events, attacks and heists that took place outside the Russian and Ukraine cyber war.
Roaming APTs
The undeniable focus on threats and events relating to the invasion of Ukraine by Russia does not mean other threat actors suspended their activities. On the contrary, while the eyes of the world are upon Russia, other actors have been roaming across the internet almost unnoticed.
On January 13, 2022, Trend Micro linked cyberespionage campaigns against governments, which are typically seen in state-backed campaigns, as well as financially driven attacks against several gambling companies in China and various cryptocurrency platforms to a new Chinese actor, dubbed “Earth Lucsa.” Earth Lucsa targeted government institutions in Taiwan, Thailand, the Philippines, Vietnam, the United Arab Emirates, Mongolia and Nigeria; educational institutions in Taiwan, Hong Kong, Japan and France; media agencies in Taiwan, Hong Kong, Australia, Germany and France; pro-democracy and human rights political organizations and movements in Hong Kong; COVID-19 research organizations in the United States; telecom companies in Nepal; religious movements that were banned in mainland China; and various cryptocurrency trading platforms. The threat actors leveraged spear-phishing, watering hole attacks and known vulnerabilities, such as ProxyShell and Oracle GlassFish. The payloads used during the campaigns included backdoors (CobalStrike, Doraemon, FunnySwitch, ShadowPad and Winnti malware) and webshells (AntSword, Behinder).
On January 13, 2022, Chainalysis published a preview of their 2022 Crypto Crime Report, concluding that North Korean cybercriminals had a banner year in 2021, launching at least seven attacks on cryptocurrency platforms and extracting nearly $400 million. Attacks primarily targeted investment firms and centralized exchanges, mostly leveraging phishing lures, code exploits and advanced social engineering to siphon funds out of “hot” wallets. The attacks were mainly attributed to Lazarus Group (APT 38), which was led by the DPRK’s Reconnaissance General Bureau.
On March 23, 2022, a cryptocurrency heist of $540 million impacted video game Axie Infinity’s Ronin Network. It was the second-largest cyber-enabled theft to date. One month later, the FBI, in coordination with the U.S. Treasury Department, implicated the North Korean Lazarus Group. According to a report published, first by The Block on July 6, the hack was the consequence of one of Axie Infiniti’s former employees being tricked by a fraudulent job offer on LinkedIn. Hackers duped a senior engineer at Axie Infinity into applying for a job at a fictitious company. After multiple rounds of interviews, the engineer was offered a job with an extremely generous compensation package. The offer document subsequently acted as a conduit to deploy malware designed to breach Ronin’s network, ultimately facilitating one of the crypto sector’s biggest hacks to date.
On June 7, 2022, the CISA, NSA, and FBI released a joint Cybersecurity Advisory (AA22-158A) explaining how the People’s Republic of China (PRC) state-sponsored cyber actors continue to exploit publicly known vulnerabilities in order to establish a broad network of compromised infrastructure, across public and private sector organizations. The advisory details how PRC state-sponsored actors targeted and compromised major telecommunications companies and network service providers.
Philippine Elections
On February 27, 2022, as CNN Philippines was gearing up to live stream a debate between candidates running in the country’s presidential elections, its website went down. It was the second time in a matter of months that the site had been hit, as Peter Guest, enterprise editor for Rest of World, reported. Since June 2021, opposition politicians, independent media, and fact-checking websites in the Philippines had been hit over and over with DDoS attacks. CNN, major news network ABS-CBN, Rappler (the outlet founded by the 2021 Nobel Peace Prize winner, Maria Ressa), and VERA Files, a fact-checking organization, were all targeted, along with the website of Vice President Leni Robredo, who was a staunch critic of the current president, Rodrigo Duterte. For the preceding 10 months, the attacks escalated in frequency and aggression as the country moved towards the 2022 general elections in May. Some of the organizations have been under a constant barrage of DDoS attempts. “It’s like being under siege,” Ellen Tordesillas, VERA Files’ president, told Rest of World. “You’re always on alert.”
In April, 2022, Meta announced preparations for the upcoming Philippine election on Facebook by activating an Elections Operations Center to detect and respond quickly to potential abuse and developing stronger policies in collaboration with the Commission on Elections, election watchdogs, independent fact checkers and civil society organizations. Meta removed a network of Facebook pages, groups and accounts maintained by the New People’s Army (NPA), a banned terrorist organization. As part of tackling other emerging harms, Meta also removed a network of over 400 accounts, pages, and groups in the Philippines that worked together to violate community standards and evade enforcement systematically. The people behind this activity claimed to be hacktivists. They relied primarily on authentic and duplicate accounts to post and amplify content about DDoS attacks, account recovery and defacing and compromising news entities’ websites in the Philippines.
Iran
On March 14, 2022, the Iranian state television reported that the paramilitary Revolutionary Guard arrested members of a “network” working for Israel that planned to sabotage Iran’s major underground nuclear facility at Fordo. The TV report said that those who were arrested approached employees at Fordo’s IR-6 section, where it is believed that centrifuges for spinning uranium were developed, paying them in cash or cryptocurrency, and instructing them on how to connect with an Israeli agent, who was acting as a manager of a company based in Hong Kong. According to the report, the alleged sabotage was to take place ahead of the Persian New Year, or Nowruz, which started on March 21.
Also on March 14, later in the day, Israel experienced a large scale cyberattack targeting the government. The attackers were able to take down several websites, including those of the ministries of health, interior, justice and welfare. The Israeli government did not officially attribute the attacks but said that all sites with a gov.il domain were targeted by DDoS attacks. The attacks came just a day after Iran fired missiles at the Iraqi city of Erbil in an apparent warning to the U.S. and its allies. The Jerusalem Post reported that an Iranian-affiliated threat group had claimed responsibility for the apparent attack and that this may have been retaliation for an alleged Israeli operation against an Iranian nuclear facility. However, neither incident was confirmed.
In April 2022, Iran’s underground Natanz nuclear facility experienced a mysterious blackout that damaged some of its centrifuges. In 2020, unexplained fires struck the advanced centrifuge assembly plant at Natanz, which authorities later described as sabotage. Iran is now rebuilding that facility deep inside a nearby mountain. Iran blamed Israel for carrying out the Natanz sabotage, although Israel never claimed it. Iran also blamed Israel for the November killing of a scientist who started the country’s military nuclear program decades earlier.
On April 20, 2022, dozens of Israeli websites, including the Israelian Airport Authority website and the Channel 9 news site, were targeted by DDoS attacks. ALtahrea, a group of pro-Iranian hackers in Iraq, claimed credit for temporarily taking down the websites at 1:02 a.m. on Wednesday, April 20, coinciding with the two-year anniversary of Qassem Soleimani’s assassination by the U.S. in Baghdad. Soleimani was head of the Quds Force of the Islamic Revolutionary Guard Corps, a U.S.-designated terrorist organization.
On April 28, 2022, two Israeli radio stations were taken over by the pro-Iranian hacker group Hackers of Savior, operating under the banner OpJerusalem. On Radio 91FM, also known as Radio Lev Hamedina, the hackers disrupted the live video broadcast, while the broadcast of Radius 100 FM was replaced by pro-Palestinian propaganda, which included recordings in Hebrew – with an Arabic accent – of “Palestine will be liberated” soon. The attacks came one day ahead of Quds Day, which fell on April 29 this year. Iran initiated Quds Day, or Jerusalem Day, in 1979, the year of the Islamic Revolution. It commemorates the day with anti-Israel speeches, events and threats to “liberate” Jerusalem from Israeli control. The radio stations said they were prepared for such an attack as the Israel National Cyber Directorate had issued, ahead of Jerusalem Day, the annual warning for potential breaches of Israeli websites expected on or around April 29. Hackers of Savior has a history of breaching Israeli institutions. In 2022, it already claimed to have hacked into a system to transfer funds between Israeli banks and people’s personal accounts. However, the Cyber Directorate found no indication of this.
OpIsrael, DragonForce Malaysia targeting Israel
OpIsrael, a yearly operation targeting Israelian businesses and citizens, was nearly nonexistent this year due to Anonymous’ focus on the Russo-Ukranian conflict. OpsBedil, a hacktivist operation targeting Middle Eastern organizations in 2021, did however make a return this year. OpsBedil can be considered the replacement for the now-defunct OpIsrael operations. The new OpsBedil operations were conducted by DragonForce Malaysia and its affiliates throughout Southeast Asia, specifically Malaysia and Indonesia. The current operation, OpsBedilReloaded, is considered a political response to events that occurred in Israel on April 11, 2022. During OpsBedilReloaded, hacktivists executed website defacements, sensitive data leaks and denial-of-service attacks. Hacktivist campaigns like OpsBedil, while nowhere near as notorious as OpIsrael once was, present a renewed level of risk for the region. Unlike Anonymous, DragonForce Malaysia and its affiliates had the time, the resources and the motivation to execute these attacks and present a moderate-level threat to Israel.
 DragonForce Malaysia OpsBedil Reloaded Campaign Flyer
DragonForce Malaysia OpsBedil Reloaded Campaign Flyer
OpsPatuk, DragonForce Malaysia Targeting India
On June 10th, 2022, DragonForce Malaysia launched a series of cyberattacks against the government of India and numerous organizations across the country, Radware reported. OpsPatuk is a new campaign, and like previous operations run by DragonForce Malaysia, it is reactionary and in response to a controversial statement made by a Bharatiya Janata Party (BJP) spokesperson who condemned the Prophet Muhammad, SAW. As a result, DragonForce Malaysia, with the assistance of several other threat groups, began to indiscriminately scan, deface and launch denial-of-service attacks against numerous websites in India. More advanced members of the group were observed leveraging current exploits, breaching networks and leaking data.
 DragonForce Malaysia OpsPatuk Campaign Badge
DragonForce Malaysia OpsPatuk Campaign Badge
Record-Level DDoS Attacks
In April 2022, Cloudflare detected one of the largest HTTPS DDoS attacks on record. Cloudflare announced it blocked a 15 million request per second HTTPS DDoS attack, originating from 6,000 unique bots that targeted a crypto launchpad. The attack lasted for 15 seconds, and no actor claimed credit for it.
In May, 2022, Radware announced it blocked a volumetric DDoS attack peaking at 1.1Tbps. While the peak attack throughput was not the highest ever recorded, this attack lasted for 36 hours and sustained over 700Gbps in a single attack vector for more than 8 hours. In contrast, most other record-breaking DDoS attacks reported in the last two years had durations of less than 60 seconds. According to Radware, the attack targeted one of the largest service providers in the U.S.
[You may also like: Radware Mitigates 1.1 Tbps DDoS Attack]
Ransom Denial-of-Service
The first half of the year was marked by a significant increase in DDoS activity across the globe. Attacks ranged from cases of hacktivism to terabit attacks in Asia and the United States. In the previous months, ransom denial-of-service (RDoS) groups claiming to be Phantom Squad and REvil resurged. In May 2022, Radware discovered several ransom demand letters from a group posing as Phantom Squad.
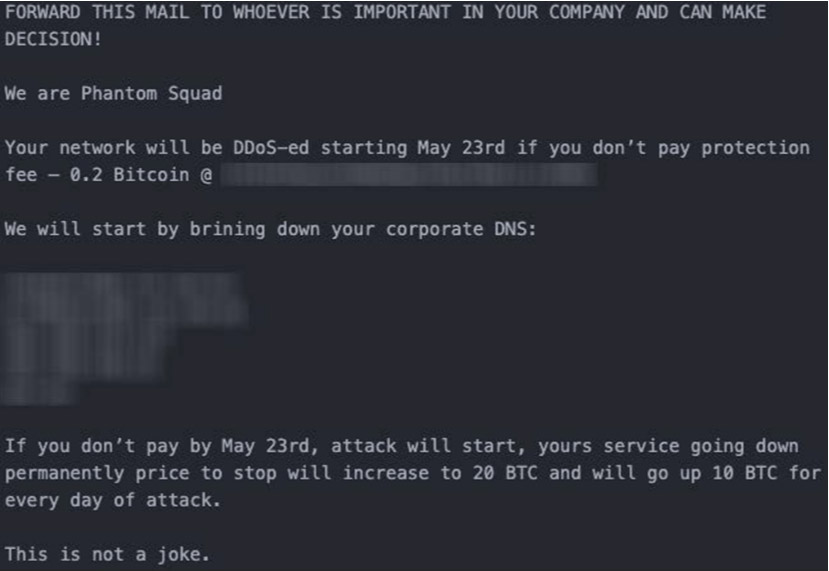 Phantom Squad Ransom Note
Phantom Squad Ransom Note
During one of the many waves of RDoS campaigns in 2021, a group claiming to be REvil targeted several VoIP providers worldwide. At the time, REvil, a notorious ransomware group, had just returned to action after disappearing following the Kaseya VSA ransomware attack. The RDoS campaign sparked concern as critical infrastructure was impacted. The campaign resulted in an industry-wide warning from Comms Council UK, stating that a “coordinated extortion-focused international campaign by professional cyber criminals” was targeting IP-based communication services providers during October 2021. And while RDoS attacks typically were considered lower tier threats that are easy to mitigate, Bandwidth.com went on record that the RDoS attacks caused a $700,000 dent in their Q3 revenues and would cost up to $12 million in actual and reputation damages.
[You may also like: Ransomware & Ransome DoS, Why They Are Similar But Different]
During the first half of 2022, a renewed campaign of RDoS attacks by a group claiming to be REvil emerged. This time the group was not only sending warning ransom notes before the attack started, but also embedded the ransom note and demands in the attack payload. The attacks were high-frequency HTTPS GET request floods that lasted several minutes and ranged up to several million requests per second. These attacks targeted online applications and hosts and embedded the ransom message as a readable string in the URL.
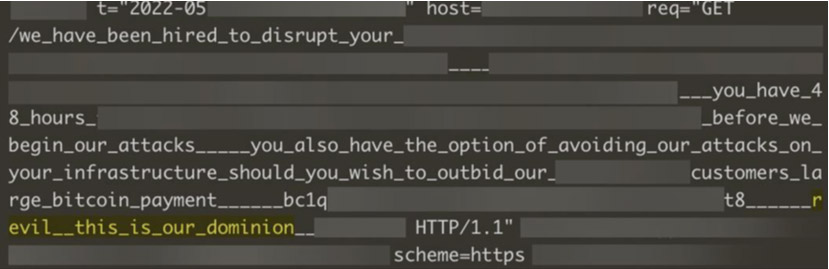 REvil RDoS Note Embedded in URL and Recorded in Server Log Files
REvil RDoS Note Embedded in URL and Recorded in Server Log Files
DDoS Attacks on Gaming
In January, 2022, APEX Legends pros went to twitter to complain that “Ranked is unplayable due to DDoS attacks.” Apex Legends was a competitive game at its heart and that meant players were desperate to win every match they queued up for, especially in Ranked. While the majority of the community abided by the rules and relied on their own skill to pick up wins, others preferred to use third-party software to gain a massive advantage. Although this could include aimbots and wallhacks, at the very top of Ranked, the preferred method tended to be DDoS attacks to disrupt the entire server, effectively disconnecting all the players in a match.
On January 22, 2022, the high stakes Squidcraft Games were plagued by DDoS attacks, resulting in the elimination of Team Andorra. Twitch Rivals Squidcraft Games was a Minecraft tournament for streamers held in a custom mode, inspired by the popular TV series “The Squid Game.” Twitch’s most famous Spanish-speaking creators, totaling 150 participants, were competing in various mini-games with direct elimination over five days. On the second day of the tournament, many Andorran streamers were eliminated after disconnecting repeatedly. NetBlocks, a group that tracked network disruptions and shutdowns, claimed in a tweet that the DDoS attack were actually targeting the competition. Unfortunately, the rest of Andorra also went down with the eliminated streamers. The internet outage lasted for over half an hour after the start of the DDoS attacks as Andorra Telecom worked to restore service.
On March 25, 2022, a DDoS attack left ‘Among Us’ unplayable in North America and Europe.
Is DDoS a Crime?
The first half of the year had a vibe of “DDoS is not a crime.” Vigilantes on both sides of the Russo-Ukrainian war leveraged whatever knowledge and resources they had to support their nation through hacking campaigns, convinced of the fact that their actions were morally acceptable and legal. These actions, however, could have serious consequences. Referring to an earlier paragraph in this blog, the FSB detained a 29-year-old Yalta, resident of Crimea, for launching DDoS attacks against Russian media outlets and financial institutions in service of Ukraine, from a program which he installed on his work computer. The detainee is facing five years in a Russian prison.
On March 10, 2022, Canadian pop star Grimes said during a Vanity Fair interview that she was behind a 2012 hack and “blackmail” of the popular culture blog Hipster Runoff after it ran a story and photo of her kissing an unnamed woman. Grimes admitted to her “coolest hacker moment” and explained how she, with the help of a friend, orchestrated a DDoS attack and held Hipster Runoff offline until the owner agreed to take down the story. Jackie Singh, author of the blog ‘Hacking, But Legal’ said that even “A decade later, unfazed by time and experience, Grimes remains convinced this was a triumphant moment for her, and not an ethical lapse for which she should feel ashamed.” She added that “Grimes doesn’t seem concerned about any actual risk associated with admitting crimes to a major magazine, despite the fact that Canada does not have a statute of limitations on cybercrime.”
Vulnerabilities
On February 22, 2022, Mitel disclosed a vulnerability (CVE-2022-26143) in their MiCollab and MiVoice devices, which would allow malicious actors to leverage the PBX VoIP gateways as powerful amplifying reflectors for DDoS attacks. About 2600 exposed systems on the public internet would facilitate high packet rate DDoS attacks with amplification rations up to 4 billion to 1. At the beginning of the year, spikes in DDoS attacks sourced from UDP port 100074 were observed and determined to originate from Mitel devices.
On March 13, 2022, iRZ, a Russian manufacturer working in the rocket and space industry, disclosed a vulnerability in its routers which allowed an attack to remotely execute commands by adding entry to crontab via simple API call to ‘/api/crontab’. The vulnerability was tracked as CVE-2022-27226 and quickly got exploited by Keksec’s latest botnet, Enemybot, discovered mid-March.
On March 29, 2022, a remote code execution (RCE) in Spring Cloud Function was disclosed by Spring, a VMWare subsidiary. The vulnerability, tracked as CVE-2022-22963, was fixed at disclosure. This disclosure came closely after another remote code execution vulnerability in Spring Cloud Gateway (CVE-2022-22947) that was patched earlier in March. In addition, Spring reported a denial-of-service vulnerability in Spring Expressions. The DoS condition could be triggered by a specially crafted Spring Expression Language (SpEL) expression and tracked as CVE-2022-22950.
On March 31, 2022, an unauthenticated remote code execution vulnerability in Spring Core was disclosed (CVE-2022-22965) and fixed. The disclosure came after a Chinese account tweeted screenshots of a new proof of concept (PoC) zero-day exploit in Spring Core. The PoC code was removed soon after initial publication, but not before being captured and confirmed by Praetorian and Rapid7. The vulnerability was dubbed SpringShell or Spring4Shell in analogy to the Log4Shell vulnerability, which also took the security community by storm in December 2021.
On May 4, 2022, F5 disclosed a new vulnerability (CVE-2022-1388) in its BIG-IP iControl REST API. The vulnerability would allow undisclosed requests to bypass the iControl REST authentication and enable remote unauthenticated attackers to access to BIG-IP devices and execute arbitrary system commands, create or delete files, or disabled services. The vulnerability was quickly leveraged by threat actors and used to deploy IoT botnets and Remote Access Trojans (RAT). On May 11, CISA added the critical flaw to its Known Exploited Vulnerabilities Catalog and later also warned that it expected to see widespread exploitation of unpatched F5 BIG-IP devices (mostly with publicly exposed management ports or self IPs) in both government and private sector networks.
On June 3, 2022, the CISA released an ICS advisory (ICSA-22-154-01) detailing vulnerabilities affecting the Dominion Voting Systems ImageCast X, an in-person voting system that allows voters to mark their ballot. The ImageCast X can be configured to allow a voter to produce a paper record or to record votes electronically. According to the advisory, the vulnerabilities include improper verification of cryptographic signatures, hidden functionality, path traversal vulnerabilities, execution with unnecessary privileges, authentication bypass spoofing vulnerabilities, incorrect privilege assignment and origin validations errors. The Dominion voting systems has been the target of conspiracy theorists, who falsely claim there was large-scale fraud in the 2020 election. The CISA, however, concluded that these vulnerabilities present risks that should be mitigated as soon as possible, but had no evidence that these vulnerabilities have been exploited in any elections. The CISA also assessed that these vulnerabilities would require access to individual ImageCast X devices, access to the Election Management System (EMS), or the ability to modify files before they are uploaded to ImageCast X devices. Mitre Corp., a federally funded nonprofit, conducted a review of the state’s election systems; and while the Mitre report has not been made public, Gabriel Sterling, Georgia’s deputy Secretary of State, said in a statement the report showed “existing procedural safeguards make it extremely unlikely for any bad actor to actually exploit any vulnerabilities.”
On June 9, 2022, JFrog Security Research disclosed a denial-of-service vulnerability they discovered in Envoy Proxy and which was assigned CVE-2022-29225. Envoy is an open-source edge and service proxy, designed for cloud-native applications. The proxy can decompress GZip and Brotli data. But the Brotli code in charge of decompressing user supplied data did not implement a size limit for the output buffer, allowing an attacker to create a Brotli ‘zip bomb’ and cause acute performance issues on the Envoy Proxy server.
Zero-Days
On June 2, 2022, Atlassian disclosed an unauthenticated OGNL Injection Remote Code Execution vulnerability affecting its Confluence Server and Data Center products. Confluence is a web-based corporate wiki written in Java. It is used by organizations across the globe as a team workspace to share knowledge and collaborate on projects documentation. The vulnerability was discovered by Volexity while conducting an incident response investigation on internet facing web servers, belonging to a customer that was running Atlassian Confluence Server software during the Memorial Day weekend in the U.S. Volexity was able to recreate the exploit and identify a zero-day vulnerability that impacted fully up-to-date versions of Confluence Server. On May 31, Volexity reported the vulnerability to Atlassian who verified and confirmed the vulnerability and subsequently assigned the issue to CVE-2022-26134. The critical vulnerability with a CVSS score of 9.8 affected all supported versions and was fixed and disclosed by Atlassian on June 2. By June 3, PoC code was available on Github and wider exploitation was observed. The Confluence RCE is caused by OGNL Injection that can be exploited by sending a crafted HTTP GET request with OGNL payload in the URI. Object Graph Navigation Language or OGNL is used for service side templates in Java Server Pages, and has been the cause of several vulnerabilities that exploit the Expression Language interpreter by passing improperly validated user-supplied data. A user in the DragonForce Malaysia forums demonstrated and shared information on how to leverage the Confluence exploit to breach servers during the OpsPatuk hacktivist operation. The Dark.IoT and Kinsing botnet operators were among the first to leverage the freshly disclosed vulnerabilities in the hope to integrate some new and very capable server systems in their botnets.
On June 23, 2022, CrowdStrike published a blog after investigating a suspected ransomware intrusion attempt in one of its customer’s environment. The malicious activity had originated from an internal Linux-based Mital VOIP application that was present on the network perimeter. After taking the device offline and conducting further analysis, CrowdStrike’s team was able to recover forensic data from the device, after the threat actor deleted all files from the device’s filesystem. They discovered a two-step exploit that enabled a remote threat actor to establish a reverse shell. Through close and immediate cooperation with the Mitel product security incident response team (PSIRT), the zero-day exploit was confirmed and patched. The vulnerability was assigned a CVSS 9.8 critical score, tracked as CVE-2022-29499, and disclosed in a security advisory from Mitel. The Remote Code Execution vulnerability, affecting a Mitel Service Appliance, was caused by incorrect data validation and impacted all Mitel Service Appliances SA 100, SA 400, and Virtual SA 19.2 SP3 and earlier.
Software Supply Chain Attacks
On March 15, 2022, in an act of protest against the invasion of Ukraine, the maintainer of a popular Node.js module called ‘node-ipc’, deliberately sabotaged his module. The module, providing local and remote inter-process communication (IPC), was leveraged by many neural network and machine-learning tools. The developer altered his code to deliberately corrupt files on systems that were running applications which depended on the node-ipc module, but only if the systems were geolocated in either Russia or Belarus, in what can only be described as a software supply chain attack impacting the npm ecosystem.
On May 10, 2022, the Rust Security Response Working Group published an official security advisory about a supply-chain attack against the Rust development community. The Rust Security Response WG and the crates.io team were notified on May 2 about the existence of a malicious crate, rustdecimal, which contained malware. The crate name was intentionally similar to the name of the popular rust_decimal crate, hoping that the potential victims would misspell its name, a favorite tactic leveraged by attackers in software supply chain attacks and known as “typosquatting.” The malicious crate contained identical source code and functionality compared to the legit rust decimal crate, except for the Decimal::new function. When the function was called, it checked whether the GITLAB_CI environment variable was set; and if so, it downloaded a secondary binary payload and executed it. The secondary payload supported both Linux and macOS, but not Windows. An analysis of the secondary payload was not possible, as the download URL was offline at the time of analysis.
On May 10, 2022, the JFrog Security Research team published a blog about disclosing new malicious packages in the Node package manager (npm) registry aimed to compromise the leading industrial organizations in Germany. Compared with most malware found in the npm repository, the new payload was a highly sophisticated, obfuscated malware that acted as a backdoor and allowed the attackers to take control over the infected system. The malware was a complete in-house development and was not based on publicly available tools. The malware contained a dropper that would send information about the infected machine to a remote telemetry server, before decrypting and executing a second stage payload which contained a JavaScript backdoor. The attackers targeted a number of prominent media, logistics and industrial organizations based in Germany, including Bertelsmann, Bosch, Stihl and DB Schenker. A day after the publication of their findings, JFrog published an update stating that a German penetration testing company named “Code White” took responsibility for the attack, adding that it was an attempt to “mimic realistic threat actors for dedicated clients.”
On May 17, 2022, threat actors uploaded a malicious package named PyMafka onto PyPI. The module’s name was similar to PyKafka, a widely used Apache Kafka client that counted over four million downloads. On Linux systems, the Python script is connected to a remote URL and piped the output to the bash shell, acting as a reverse shell. On Windows and macOS, the payload consisted of a Cobalt Strike beacon. The typo-squatted package only reached a download count of 325 before it was detected and removed.
Read the other two blogs in our three-part series, which also highlight first half 2022 cyber activities. Our first post takes a look at the increased efforts and successes of law enforcement and the global security community in their fight against cybercrime. Our second blog reviews the cyber events leading up to and occurring as a consequence of Russian’s invasion of Ukraine — a story of modern-day cyber warfare.
Like this post? Subscribe now to get the latest Radware content in your inbox weekly plus exclusive access to Radware’s Premium Content.