A reverse proxy is a type of physical or virtual network device, software, or cloud service that plays a crucial role in managing, scaling and securing traffic. It deploys in front of applications, intercepting requests from clients. This is different from a forward proxy where the proxy sits in front of the clients rather than the servers.
Basic Functionality and Role in Managing Web Traffic
The primary function of a reverse proxy is to direct client requests to the appropriate backend application server. By deploying in front of applications, a reverse proxy decouples applications and user connections and provides an additional level of abstraction and control to ensure the smooth flow of network traffic between clients and applications. This is particularly useful in enhancing security, performance, and reliability.
Acting as a “Middleman”
A reverse proxy server acts as a “middleman” between clients and applications. Instead of clients connecting directly to applications serving content, a reverse proxy like Alteon Application Delivery Controller can sit in the middle. When Alteon receives a request from a user, it will send forward, or “proxy,” that request to the final application server. This server is called the “origin server” since it’s what will be responding to requests.
The origin server does not have a direct connection to the user and will only see requests originating from the reverse proxy’s IP address. This can be a problem, but most proxy services like Alteon will add headers like X-Forwarded-For to the request. These headers will inform the origin server of the client’s actual IP address.
A reverse proxy server is a vital tool in any system administrator’s toolkit. By decoupling user requests from the applications that serve them and distributing user requests between applications, a reverse proxy can scale to process millions of user connections and reduce the number of application instances required. The additional capabilities of reverse proxies such as application protection, caching and compression help increase the scalability, performance, resilience and security of a deployment with reverse proxies.
A reverse proxy typically operates in three primary stages:
Origin Server Connection: The reverse proxy, which acts as a middleman, forwards the client connection request to the application, establishing a connection between the client and the application instance serving the request.
Connection Request Collection: The reverse proxy receives incoming requests from clients at the network’s edge.
TCP Three-Way Handshake: A connection to the reverse proxy is established after a TCP connection protocol is satisfied. In addition, the SSL handshake is followed if the request is an HTTP/S request.
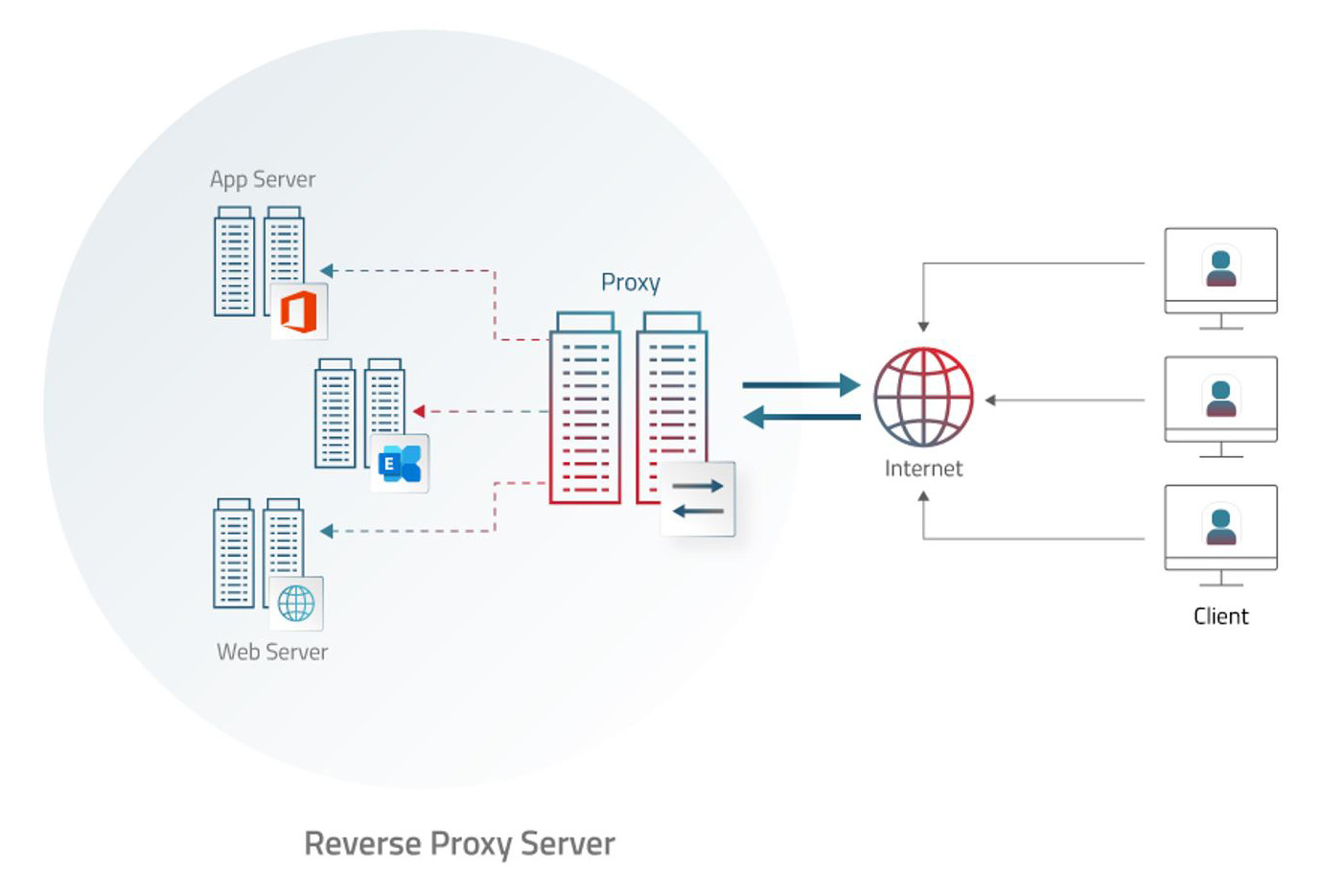
A reverse proxy sits in front of one or more web application servers, intercepting client requests. This is different from a forward proxy, where the proxy sits in front of the clients. While a forward proxy serves the clients and fetches content from the internet on their behalf, a reverse proxy does the opposite—it receives client requests and directs them to the appropriate backend server.
Comparison Between Forward and Reverse Proxies
Forward Proxies
A forward proxy, often called a “proxy server,” is a server that sits in front of one or more client machines. When the clients make requests to sites and services on the Internet, the forward proxy server intercepts those requests and then communicates with external web servers on behalf of those clients. In essence, a forward proxy ensures that clients don’t communicate directly with external sites.
Advantages of Forward Proxies
Enhancing Privacy and Anonymity: Forward proxies can provide anonymity by masking the original IP address.
Using Automation Tools for Web Scraping: They are often used in web scraping, where they can help prevent IP bans and improve the efficiency of the scraping process.
Accessing Geo-Restricted Content: They can be used to access content that is restricted in certain geographical locations.
Bypassing Bans and Blocks: Forward proxies can be used to bypass bans and blocks on websites.
Reverse Proxies
A reverse proxy sits in front of one or more web applications, intercepting client requests. Unlike a forward proxy, a reverse proxy makes sure that clients don’t communicate directly with applications. By decoupling the applications from the clients, the reverse proxies can scale them independently.
Advantages of Reverse Proxies
Caching: They can cache content from an origin server in temporary storage, and then send the content to clients that request it without further transacting with the server. This reduces latency and improves performance.
Load Balancing: Reverse proxies can distribute client requests across multiple application server instances, preventing any one application instance from becoming a bottleneck.
SSL Termination: They can handle the SSL encryption/decryption process, offloading this task from the applications and thus improving performance and reducing cost of application infrastructure.
Network Protection & Security: Reverse proxies can protect applications from exposure by scrubbing requests from clients.
Radware’s Solutions with Reverse Proxy Functionality
Radware’s Alteon load balancer, also called Alteon Application Delivery Controller (ADC), is a reverse proxy. Radware’s AppWall, a web application firewall (WAF) that’s available to be integrated with Alteon, also operates as a reverse proxy. It ensures fast, reliable and secure delivery of mission-critical web applications and APIs for corporate networks and in the cloud. It provides patent-protected technology to create and optimize security policies in real-time for the widest security coverage with the lowest false positives and minimal operational effort.
A reverse proxy and a virtual private network (VPN) are both types of servers that play crucial roles in network infrastructure, but they serve different purposes and work in different ways.
Key Differences
The main difference between a reverse proxy and a VPN is that proxies will only reroute application traffic, while VPNs can do this for the whole operating system. From a security perspective, proxy servers are generally less safe than VPNs. While they’re great for anonymous web browsing and bypassing geo-restrictions, they won’t encrypt your data as it’s sent to another server and can be vulnerable to cyber-attacks.
Reverse Proxy
A reverse proxy is an intermediary server positioned in front of web and application servers, directing client requests (e.g., from web browsers) to these servers. The deployment of reverse proxies is primarily intended to provide a public access point, DNS, and to enhance security and performance.
Advantages of a Reverse Proxy
Makes Public Access Easy: A reverse proxy is a simple way to make your server publicly accessible, and to add things like SSL encryption without having to do much configuration.
Centralized Auditing Point: If you are running many servers, a reverse proxy can handle all incoming requests with a single firewall.
Reduces Server Workload: A reverse proxy can compress data before transmitting it to different servers within your internal network.
Disadvantages of Reverse Proxy
Susceptible to DDoS: Since the reverse proxy is typically accessible over the Internet, a DDoS attack is possible. This may be alleviated by either selecting reverse proxies with DDoS protections or adopting DDoS prevention solutions before traffic reaches a proxy.
Creates a Single Point of Failure: If a reverse proxy encounters a failure, anything behind it can become inaccessible or compromised. However, this limitation may be prevented by adoption of high availability options.
Opens You Up Publicly: The reverse proxy will give you a public access point. This may be restricted by having secure IT administration to prevent non secure applications being exposed to the Internet as virtual IP (VIP).
VPN
A VPN establishes a secure connection directly to the remote server. This connection is safe and encrypted. However, it’s difficult to share with users. A VPN service protects you from ISP tracking, government surveillance and hackers. Proxies do not provide such protection, so they should never be used to handle sensitive information.
Advantages of a VPN
Protects from Tracking and Surveillance: A VPN service protects you from ISP tracking, government surveillance and hackers.
Encrypts Your Traffic: VPNs encrypt your traffic while proxy servers do not.
Disadvantages of a VPN
The main disadvantages of using a VPN compared to a reverse proxy are:
Geographical Restrictions: Free VPNs often get blocked by streaming services like Netflix. A reverse proxy can be used for geolocation, routing client requests to different servers based on the geographic location of the client.
Restrictions: It isn’t always possible to bypass restrictions with a VPN. A reverse proxy can be configured to bypass certain types of restrictions.
Performance: VPNs reroute and encrypt your Internet connection through a server, which might decrease your internet speed, especially when using free VPNs. On the other hand, a reverse proxy can improve performance by load balancing and caching content.
Compatibility: Some devices may not support VPNs. Reverse proxies are generally compatible with all web-enabled devices.
Data Privacy: Free VPNs may log and sell your data, including your browsing activity, to third parties. A reverse proxy enhances the security of web applications by hiding the details of the backend servers from the clients.
Cost: A safe, top-quality VPN will cost you money. Depending on your needs, a reverse proxy might be a more cost-effective solution.
Data Protection: VPNs do not protect you from malware or phishing attacks. Reverse proxies can help protect backend servers from malicious traffic by filtering requests and blocking suspicious traffic.
Note:These disadvantages are not inherent to all VPNs. Many of these issues can be mitigated by choosing a reputable, paid VPN service.
A reverse proxy is a powerful tool that can greatly enhance the performance, security and reliability of web applications. Here are some reasons why you might want to use a reverse proxy:
Advantages of Using a Reverse Proxy
Load Balancing: A reverse proxy can distribute client requests across multiple servers, preventing any one server from becoming a bottleneck.
Improved Performance: Reverse proxies can cache content from an origin server in temporary storage, and then send the content to clients that request it without further transacting with the server.
Enhanced Security: By acting as an intermediary for requests from clients, reverse proxies can protect the web server from exposure.
Single Point of Entry: Reverse proxies provide a single point of entry for traffic filtering and routing, which can improve network efficiency.
SSL Termination: Reverse proxies can handle the SSL encryption/decryption process, offloading this task from the web server.
Disadvantages of Using a Reverse Proxy
While reverse proxies offer many benefits, there are also some potential drawbacks to consider:
Single Point of Failure: If a reverse proxy encounters a failure, anything behind it can become inaccessible or compromised.
Risk to Stored Information: Since a reverse proxy can track IP addresses and encrypt/decrypt information, it is also able to store data such as passwords.
Not Immune to Hackers: Reverse proxy servers aren’t immune to hackers.
Setup Can Be Difficult: Many reverse proxy systems require a bit of technical know-how and skill to combine with existing systems.
HTTP Request Smuggling: This is a web application attack that exploits differences between web servers and their reverse proxies.
In conclusion, while there are some potential risks associated with using a reverse proxy, the benefits often outweigh the drawbacks for many organizations. The improved performance, enhanced security, and load balancing capabilities make reverse proxies a valuable tool in many network infrastructures.
There are several types of reverse proxies, each with its own unique features and use cases. Here are some of the most common types:
HTTP Reverse Proxies
HTTP reverse proxies are the most common type of reverse proxy. They receive client requests and forward them to the appropriate backend server. Examples of software that can function as HTTP reverse proxies include Alteon, Apache HTTP Server, NGINX and HA Proxy.
FTP Reverse Proxies
FTP reverse proxies are used to make an FTP server accessible via the Internet. They work by accepting client requests and forwarding them to the appropriate FTP server.
SSL Reverse Proxies
SSL reverse proxies handle the SSL encryption/decryption process, offloading this task from the web server. This can improve performance and allow the backend servers to focus on serving content.
Other Types of Reverse Proxies
Hardware Load Balancers: These are physical devices used to distribute web traffic across multiple network servers. They can prevent any one server from becoming a bottleneck, thereby improving the performance and reliability of web applications.
Reverse Proxy Software: This includes software solutions like Alteon and NGINX, which can act as a load balancer, reverse proxy, web server.
Open-Source Reverse Proxies: There are several open-source reverse proxies available, such as HA Proxy, Envoy, NGINX, Varnish, Træfɪk, Apache Traffic Server, Squid, Pound and Apache.
Integration with Radware’s Solutions
Radware’s solutions can be integrated with various types of reverse proxies such as Radware Alteon, Amazon AWS, Microsoft Azure and Citrix NetScaler to enhance security and performance. For instance, Radware’s Attack Mitigation System (AMS) can be used with HTTP, FTP and SSL reverse proxies, as well as hardware load balancers, open-source reverse proxies and reverse proxy software. AMS provides state-of-the-art attack mitigation based on DefensePro X (DDoS Protection) and AppWall (Web Application and API Protection), which can mitigate attacks on the network, server and application levels. This makes it a versatile solution for integrating with various types of reverse proxies.
A reverse proxy is a server that sits between client devices and web servers, forwarding client requests to the web servers. It provides a variety of functionalities that enhance the performance, security and reliability of web applications. The primary uses of a reverse proxy are:
Load Balancing
Load balancing is one of the most common uses of reverse proxies. By distributing client requests across multiple servers, reverse proxies ensure that no single server is overwhelmed, and all requests are handled in a timely manner. This can help improve website performance and ensure that users have a seamless experience.
For example, a popular website that gets millions of users every day may not be able to handle all of its incoming traffic efficiently on a single server. Deploying multiple servers and using a reverse proxy to distribute the traffic can prevent any one server from becoming a bottleneck, thereby improving the performance and reliability of the website.
Threat Prevention
Reverse proxies can help protect backend servers from malicious traffic by filtering requests and blocking suspicious traffic. By blocking or rate-limiting suspicious requests, reverse proxies can prevent servers from being overwhelmed and keep the application running smoothly.
For instance, a reverse proxy can be configured to block traffic from known malicious IP addresses or limit the rate of requests from a single IP address to prevent denial-of-service attacks.
SSL Encryption
Reverse proxies can handle the SSL encryption/decryption process, offloading this task from the web server. This can improve performance and allow the backend servers to focus on serving content.
For example, a website that receives a large volume of HTTPS traffic may use a reverse proxy to handle the computationally expensive task of encrypting and decrypting the traffic, thereby reducing the load on the web server.
Cache Static and Dynamic Content
Reverse proxies can cache both static and dynamic content, reducing the load on the origin server and resulting in faster website loading times. When clients request the same resources, the reverse proxy serves the cached content directly, reducing server load and improving response times.
For instance, a news website with many static articles and images can use a reverse proxy to cache this content. When a user requests an article, the reverse proxy can serve the cached version instead of requesting it from the backend server, resulting in faster load times.
Security
Reverse proxies can enhance the security of web applications by hiding the details of the backend servers from the clients. This can make it harder for attackers to directly target the backend servers. Reverse proxies can also provide additional security features such as web application firewalls and intrusion prevention systems.
Implementing a reverse proxy involves several steps, from choosing the right software to configuring and testing your setup. Here’s a detailed guide:
Choosing Your Reverse Proxy Software
The first step in setting up a reverse proxy is selecting the right Application Delivery Controller such as Alteon, NGINX, Envoy or HA Proxy. Consider factors such as ease of configuration, performance and community support when making your choice.
Installation and Configuration
Once you’ve chosen an ADC, install the reverse proxy device or software. Follow the installation instructions provided by the server’s documentation.
Next, configure your DNS settings. Create a DNS record that points your domain or subdomain to the IP address of your server. This will ensure that requests for your website are directed to the reverse proxy server.
Securing your website with SSL/TLS is crucial for protecting sensitive data and building trust with your users. Generate or obtain an SSL/TLS certificate for your domain and configure your server to enable HTTPS connections.
Configure virtual hosts in your reverse proxy to handle incoming requests for different domains or subdomains. This will ensure that each website is correctly routed through the reverse proxy. The reverse proxy forwards client requests to the appropriate backend application servers based on the configured rules.
Finally, configure your backend servers to handle requests forwarded by the reverse proxy. Ensure that the backend servers are properly configured and running before proceeding.
Testing Your Reverse Proxy Setup
After setting up your reverse proxy, it’s crucial to test the setup to ensure that it’s working correctly. This involves sending a request from a client machine to the IP address of your reverse proxy server and checking if the request is properly forwarded to one of your backend servers.
Integration with Radware’s Solutions
Radware’s solutions can be integrated with various types of reverse proxies to enhance security and performance. For instance, Radware’s Attack Mitigation System (AMS) can be used with HTTP, FTP, and SSL reverse proxies, as well as hardware load balancers, open-source reverse proxies and reverse proxy software. The AMS provides state-of-the-art attack mitigation based on Radware’s DefensePro and AppWall, which can mitigate attacks on the network, server and application levels.
Reverse proxies offer a range of advanced techniques that can enhance the performance, security, and reliability of web applications. Here are some of these techniques:
Splitting Traffic with a Reverse Proxy
Traffic splitting is a technique where a reverse proxy load balances and distributes incoming requests to different servers. This can be based on various factors such as the type of content requested, the load on the servers, or even the time of day. For example, a reverse proxy could send 50% of requests to one server, and 50% to another, effectively doubling the capacity of the website.
Radware’s Alteon ADC and load balancer can function as a reverse proxy and provide advanced traffic splitting capabilities. Alteon can be used as a reverse proxy to rewrite the URL from one domain to another to avoid getting an “access denied” alert on the host name of the original domain.
Using a Reverse Proxy for Geolocation
A reverse proxy can also be used for geolocation. This involves routing client requests to different servers based on the geographic location of the client. For example, a website might have servers in different countries, and a reverse proxy could route requests from clients to the server that is geographically closest to them.
Radware’s solutions can be integrated with various types of reverse proxies to enhance geolocation capabilities. For instance, Radware’s Attack Mitigation System (AMS) can be used with HTTP, FTP, and SSL/TLS reverse proxies, as well as hardware load balancers, open-source reverse proxies, and reverse proxy software. The AMS provides state-of-the-art attack mitigation based on Radware’s DefensePro and AppWall, which can mitigate attacks on the network, server, and application levels.
Other Advanced Techniques
There are several other advanced techniques that can be used with reverse proxies, such as:
Caching: A reverse proxy can cache content from an origin server in temporary storage, and then send the content to clients that request it without further transacting with the server.
Content Compression: A reverse proxy can compress data before transmitting it to different servers within your internal network.
SSL Termination: A reverse proxy can handle the SSL encryption/decryption process, offloading this task from the web server.
Radware’s solutions, such as the Alteon ADC balancer and AppWall, Radware’s WAAP, can enhance these capabilities. For instance, AppWall, a Web Application and API Protection (WAAP), operates as a reverse proxy and ensures fast, reliable and secure delivery of mission-critical web applications and APIs for corporate networks and in the cloud. It provides patented technology to create and optimize security policies in real-time for the widest security coverage with the lowest false positives and minimal operational effort.