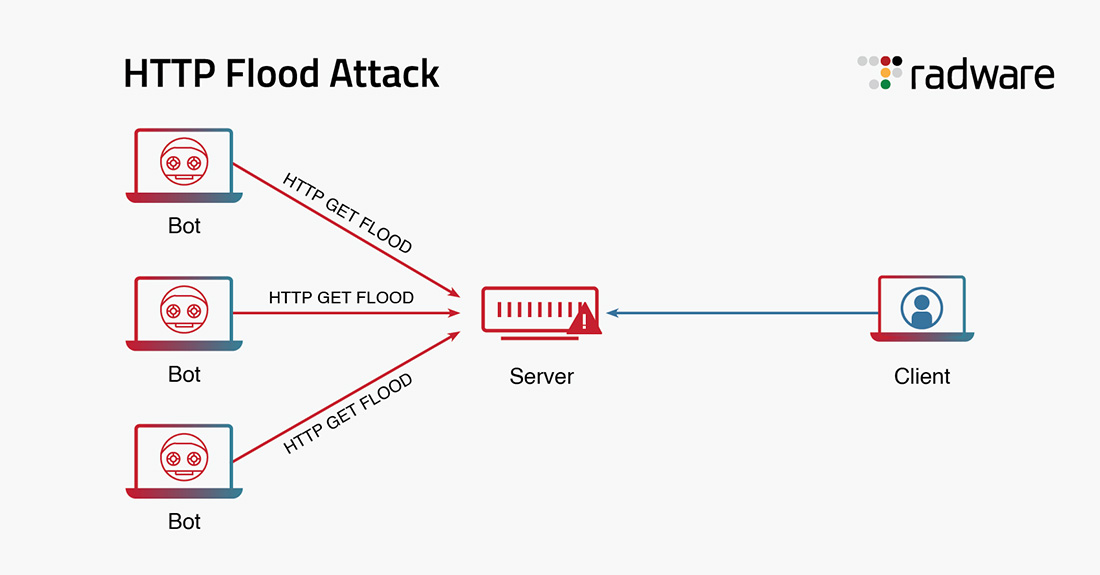
An HTTP Flood attack is a Layer 7 distributed denial-of-service (DDoS) attack that targets web and application servers. The HTTP Flood attack executes a DDoS attack by using HTTP GET or HTTP POST requests. The requests are valid and target available resources, hence making HTTP Flood attacks difficult to protect against.
Anonymized HTTP Flood attacks may also spoof a client IP address to prevent tracking the attacker.
How does an HTTP Flood attack work?
During an HTTP Flood attack, the attacker floods the target application and web servers with HTTP GET or POST requests. The numerous HTTP GET and POST requests cause the web and application server connection threads to allocate system resources to process incoming requests. The connection requests may also be initiated by botnets and cause the exhaustion of web and application server resources. The web and application servers thus enter a denial-of-service state for processing any requests from legitimate traffic.
How is an HTTP Flood attack mitigated?
Due to the unique nature of its mechanism, the best approach to mitigate an HTTP Flood attack is a combination of network and application layer security.
Network security focuses on blacklisting attackers and IP addresses known to be associated with HTTP Flood attacks, rate-limiting requests, and checking the behavior profile of each request. Application layer security focuses on patching vulnerabilities in web applications, implementing rate limits from known bad actors and addresses, and using CAPTCHA and crypto challenges. It also uses DDoS protection services, load balancers, and web application and API protection.
Organizations can take these steps to mitigate HTTP Flood attacks:
- Increase web and application server connection limits: This can help reduce vulnerability to HTTP Flood DDoS attacks by increasing the number of concurrent HTTP connections that may be processed. Additionally, timeouts may be implemented to free up web and application server connection resources.
- Implement rate limiting: Rate limiting involves restricting incoming requests from any given IP address in order to prevent DDoS attacks such as those launched by HTTP Flood attackers. Note that, if anonymized, IP addresses could be spoofed which may lead to incorrect rate limits.
- Use load balancers and web application firewalls (WAFs): WAFs help protect against HTTP Flood attacks using HTTP GET and POST by using various mechanisms such as CAPTCHA and crypto challenges, and applying bot mitigation techniques. Load balancers and reverse proxies can buffer connections and implement multiple connection management techniques to prevent HTTP GET and POST requests from affecting applications and web server resources.
- Use services such as cloud-based DDoS protection or botnet tracking: These solutions can help to identify suspicious activity quickly and respond appropriately.
- Always maintain Security best practices: Keep software updated and patch vulnerabilities regularly. This will help to minimize risk and protect against all types of threats, including those posed by malicious actors who use techniques like HTTP Flood DDoS attacks.
- Use Radware DDoS protection (DefensePro, Cloud DDoS Protection Service), WAAP and Cloud WAAP, and Alteon (with integrated WAAP) solutions: Mitigate HTTP Flood DDoS attacks by using approaches that block attacks without impacting legitimate traffic and use machine-learning and behavioral-based algorithms to understand what constitutes a legitimate behavior profile. Then, automatically block malicious attacks while managing user connections effectively without impacting legitimate HTTP requests. This increases protection accuracy while minimizing false positives and disruption to legitimate users.