What Is Anti-Botnet Software?
Anti-bot software helps protect digital platforms from malicious bot attacks by detecting and mitigating suspicious or automated bot activity. This software is crucial for online businesses to prevent harm to their digital assets from bots attempting to perform activities like credential stuffing, content scraping, and DDoS attacks.
Anti-bot software is designed to differentiate between legitimate human users and automated bots accessing a website, mobile application, or API. It aims to block or manage bot traffic that can be used for malicious purposes.
Anti-bot solutions have two primary aspects:
- Detection: Anti-bot solutions use various techniques, including machine learning, behavioral analysis, and threat intelligence, to identify bot activity.
- Mitigation: Once a bot is identified, the software can take action to block or limit its access, preventing it from causing harm.
Common features of anti-bot software:
- Real-time detection and response: This allows for immediate action against emerging threats, minimizing potential damage.
- Behavioral and interaction analysis: This helps reduce both false positives and false negatives.
- Adaptability: The software needs to be able to learn from evolving bot techniques and adjust its defenses accordingly.
- Comprehensive coverage: It should address various attack vectors, including DDoS attacks, credential stuffing, and content scraping.
- Integration: Easy integration with existing systems is important for efficient implementation.
- Scalability: The solution should be able to handle increasing traffic volumes without performance degradation.
This is part of a series of articles about bot protection.
In this article:
Real-Time Detection and Response
Anti-bot software can detect and respond to threats in real time. This involves continuous monitoring of network traffic and application interactions, seeking out signs of bot activity such as abnormal request rates, sequential access patterns, or anomalies in device fingerprints.
When bots are identified, the software can automatically block suspicious traffic, challenge it with CAPTCHAs, or divert it for further analysis. This immediate intervention limits the window of opportunity an attacker has to exploit vulnerabilities or extract data. Automation within real-time response mechanisms also minimizes manual intervention, reducing security team workloads and accelerating threat neutralization.
Learn more in our detailed guide to botnet detection.
Behavioral and Interaction Analysis
By establishing profiles for normal user behavior—including click rates, mouse movements, keystroke dynamics, and navigation paths—anti-bot systems can more accurately differentiate between legitimate users and automated bots attempting to mimic human activity. Detailed behavioral metrics enable software to spot subtle differences that static rules or denylists miss.
Rather than relying on IP reputations or outdated threat intelligence, behavioral analysis adapts to new tactics automatically, ensuring that evolving attack vectors are promptly addressed. It is particularly useful for thwarting credential stuffing, account takeover attempts, and other attacks where attackers blend bot traffic with normal user flows.
Adaptability
Adaptability refers to the software’s capacity to evolve in response to new botnet threats and changing attack techniques. Anti-bot solutions update their detection algorithms using threat intelligence feeds, machine learning observations, and experiences from previously encountered attacks.
This constant adaptation allows the software to remain effective even when attackers adjust their methods, such as changing user agents, using distributed infrastructures, or employing AI-powered bots. Many vendors include cloud-based threat sharing mechanisms and automated signature updates that help customers stay ahead of the latest attack trends.
Comprehensive Coverage
Multi-layered coverage ensures that all potential attack surfaces are monitored and protected. Anti-bot software can analyze traffic across websites, mobile apps, APIs, and backend infrastructure. This prevents attackers from bypassing defensive measures by switching vectors, such as moving from website attacks to API abuse or targeting IoT devices.
In addition to multiple vectors, comprehensive solutions provide visibility into incoming and outgoing traffic, which helps in identifying compromised assets used as part of larger botnets. For organizations with distributed environments or hybrid cloud infrastructure, centralized dashboards and reporting enable consistent policy enforcement and easier incident response.
Scalability and Integration
Scalability ensures that anti-bot solutions remain effective as organizations grow or experience varied traffic volumes. Leading software can handle increased loads, whether from legitimate expansion, marketing campaigns, or sudden surges during attack attempts. Cloud-native platforms offer elastic scaling that adjusts resources on demand.
Integration capabilities are equally important, as anti-bot solutions must interact with existing security stacks, such as SIEMs, firewalls, threat intelligence platforms, and authentication systems. APIs, plugins, and support for industry standards enable streamlined deployment and coordinated incident management.
Related content: Read our guide to bot attacks

Radware Bot Manager is a cloud‑native, award‑winning bot management solution that safeguards web applications, mobile apps, and APIs from sophisticated automated threats—without impacting legitimate users. Leveraging patented Intent‑based Deep Behavior Analysis (IDBA), semi‑supervised machine learning, device fingerprinting, and collective bot intelligence, it delivers precise bot detection, real‑time mitigation, and seamless user experience. Bot Manager’s AI‑powered correlation engine auto‑generates granular protection rules and shares insights across security modules—thwarting account takeover (ATO), DDoS, ad and payment fraud, web scraping, and unauthorized API access.
Key features include:
- Intent‑based Deep Behavior Analysis: Profiles and distinguishes malicious bot actions even at the business‑logic layer with minimal false positives.
- Automated Rule Generation: Continuously analyzes threat patterns and auto‑tunes protection policies, reducing manual effort.
- Device Fingerprinting & Collective Intelligence: Combines client telemetry with Radware’s global bot database to identify and block advanced bots.
- AI‑Driven API Discovery & Protection: Automatically maps APIs and applies tailored defenses against abuse.
- Customizable Mitigations: Offers Crypto Challenge and other challenge‑based options that exponentially raise attacker costs.
- OWASP Top 10 & Data Leak Prevention: Defends against common vulnerabilities and stops sensitive data exfiltration.
- Scalable, Real‑time Dashboard: Provides live visibility into bot traffic and performance, scaling elastically to any request volume.
- Seamless User Experience: Eliminates reliance on CAPTCHAs, ensuring frictionless access for legitimate users and “good bots.”
- Certifications & Compliance: NSS Labs recommended, ICSA Labs certified, and PCI‑DSS compliant for enterprise assurance.
Limitations (reported by users on G2 & Capterra):
- Reporting & Dashboard Customization: Built‑in reports are functional but offer limited customization for bespoke analytics.
- Native Integration Connectors: No out‑of‑the‑box plugins for SIEM or ticketing systems—requires custom integration via API or SDK.
- Custom Rule Configuration: Fine‑tuning or creating new rules sometimes necessitates a support ticket rather than self‑service.
- Bulk Indicator Management: Lacks a simple bulk‑upload interface for IP or indicator lists, making large‑scale changes more manual.
- Pricing Perception: Positioned as an enterprise‑grade solution; cost can be a barrier for smaller organizations.

Imperva Advanced Bot Protection is a bot mitigation solution that secures websites, mobile applications, and APIs from automated attacks, including OWASP Automated Threats. It combines detection models, behavioral analysis, and monitoring to distinguish between human, good bot, and malicious bot traffic.
Key features include:
- Multi-layered detection: Uses behavior analysis, client interrogation, threat intelligence, and ML to detect traffic dimensions.
- Adaptive protection: Customizable detection models and policies help stay ahead of evolving bot evasion techniques.
- Granular controls: Enables configuration of defenses and fine-tuning of mitigation strategies.
- Reporting: Provides explainable insights with monitoring, rule-level analysis, and customizable dashboards.
- Low false positives: Detection accuracy is improved through validation and testing.
Limitations (reported by users on G2):
- Dashboard usability could be improved; users find it less intuitive than competitors.
- Testing flexibility is limited; users can only use Imperva’s predefined testing bot.
- Deployment may require adding a reverse proxy, increasing setup complexity.
- Setup inside private networks can take extra effort to avoid public network hops.
- Pricing is considered relatively high for the available features.

Cloudflare Bot Management is a scalable solution for identifying and mitigating malicious bot traffic. By leveraging data from websites on its network, Cloudflare trains machine learning models to assign a bot score to requests. It combines behavioral analysis, fingerprinting, and anomaly detection to block threats such as credential stuffing, scraping, and inventory hoarding.
Key features include:
- Multiple detection methods: Uses machine learning, request fingerprinting, and behavioral signals to classify and block malicious bots.
- No CAPTCHAs: Reduces user friction with privacy-focused methods like Private Access Tokens for human verification.
- Simple deployment: Automatically recommends bot management rules with minimal setup and maintenance required.
- Bot scoring: Assigns a bot score to requests based on deviations from normal traffic behavior patterns.
- Custom rules engine: Enables tailored bot policies by scoping rules based on application-specific criteria.
Limitations (reported by users on Capterra):
- Service disruptions can occur during initial configuration.
- Steep learning curve for users with limited cloud technology experience.
- Website display issues may persist even after clearing cache on both server and browser.
- Changing a domain’s name servers requires a paid plan.
- Customer support is difficult to reach, with slow ticket responses and limited direct contact options.
- Frequent interface and feature changes complicate routine administrative tasks.
- Support quality may vary unless users upgrade to a higher plan.

Akamai Account Protector is a security solution to detect and prevent account abuse throughout the user account lifecycle. It uses machine learning, behavioral profiling, and threat intelligence to evaluate the legitimacy of user actions from account creation to post-login activity.
Key features include:
- Lifecycle protection: Secures accounts from creation through login, password reset, and post-login activity.
- Behavior-based detection: Profiles users based on behavior, device, location, network, and time-based patterns to detect anomalies.
- Risk scoring: Assesses each request, assigning a dynamic risk score used to drive automated responses.
- Edge-based mitigation: Executes response actions, such as block or alert, at the edge for faster protection.
- Bot detection: Identifies and blocks bots, including adversarial bots.
Limitations (as reported by users on Peerspot):
- Configuration pushes and retractions are slow, taking about 20 minutes each.
- Pricing is considered high relative to competitors.
- Customer support and documentation need improvement.
- Application layer protection is seen as weaker compared to alternatives like Cloudflare.
- Custom rules and analytics reporting in the OEM console lack visibility and flexibility.

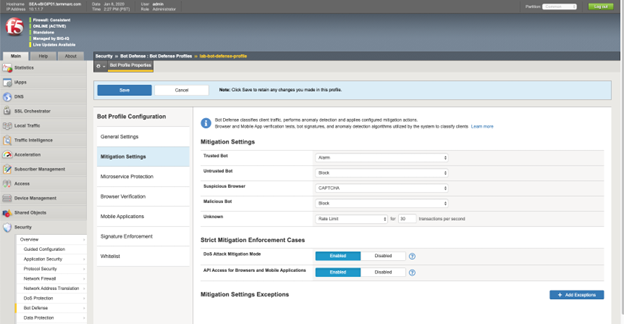
F5 Bot Management is designed to protect web applications and APIs from malicious automation, including account takeover (ATO), fraud, and business logic abuse. It uses a combination of AI-driven analysis, spoof-resistant telemetry, and adaptive defense mechanisms to detect and stop bot attacks.
Key features include:
- Adaptive bot detection: Continuously learns and adapts to new bot behaviors, helping defend against retooling attempts.
- Spoof-proof telemetry: Collects trusted signals from clients to distinguish bots from human users.
- AI-powered analysis: Uses trained AI models to evaluate user behavior and interaction patterns across apps and APIs.
- Reduced user friction: Minimizes reliance on CAPTCHAs and other intrusive authentication mechanisms to improve customer experience.
- Enterprise-scale visibility: Protects large volumes of transactions.
Limitations (as reported by users on G2):
- User interface is outdated and overly text-heavy, making navigation harder.
- Initial setup is complex and often requires support from F5.
- Cloud-based processing can introduce latency during request analysis.
- Connection times can be slow, with delays ranging from 30 to 90 seconds.
- Auto Connect sessions may drop without notifying users, requiring manual restarts.
- Pricing is higher compared to similar bot management solutions.
Source: F5
Conclusion
Effective anti-bot software plays a critical role in securing digital platforms against the growing threat of automated attacks. By combining real-time detection, behavioral analysis, adaptability, and comprehensive coverage, these solutions help organizations protect their applications, APIs, and user accounts. Scalability and seamless integration further ensure that protection remains consistent even as traffic patterns change and attack methods evolve.