A DDoS attack, or Distributed Denial-of-Service attack, is a cybercrime that involves flooding a target with internet traffic to make it inaccessible. DDoS attacks are a type of denial-of-service (DoS) attack, but they are far more powerful than traditional DoS because they use multiple sources to generate exponentially more traffic.
This information is part of a series of articles focused on anti-DDoS.
DDoS attacks are typically launched from a botnet, which is a network of compromised devices. This also increases the difficulty of attribution, as the true source of the attack is harder to identify.
The goal of a DDoS attack is to overwhelm a system's resources or bandwidth, making it difficult or impossible for legitimate traffic to reach its destination. DDoS attacks can have a number of consequences, including lost business, reputation damage, and a drop in legitimate traffic.
Some examples of DDoS attack scenarios include:
- Disrupting a financial institution's online services
- Blocking eCommerce operations during peak sales events
- Targeting healthcare portals during emergency situations
Learn more in our detailed guide to DDoS examples.
There are many types of DDoS attacks, detailed below. Some of the common types include:
- HTTP floods: Overwhelm a server with a large number of HTTP GET or POST requests
- Low and slow attacks: Send traffic and HTTP requests that appear to be legitimate at a very slow rate
- Slowloris attacks: Open and maintain many simultaneous HTTP connections to a target server
- TCP state-exhaustion attacks: Attempt to consume the connection state tables in infrastructure components
DDoS attacks are illegal in the United States and can be classified as a federal criminal offense under the Computer Fraud and Abuse Act (CFAA).
This is part of an extensive series of guides about hacking.
What is a DDoS Attack? | A Radware Minute
In this article:
Let’s review the basics of modern DDoS attacks.
DoS vs. DDoS
While many modern denial of service attacks are distributed attacks (DDoS), some attacks are simple denial of service (DoS)—launched from a single machine or a small group of machines working together. This type of attack is simpler to execute but also easier to detect and mitigate. The limited number of devices means that the attack can often be traced back to its source, and defense mechanisms can be more effective at blocking traffic.
A DDoS attack leverages a large number of machines, often distributed across various locations around the world. These machines, typically the compromised devices of unknowing victims, flood the target with traffic simultaneously, making it much harder to defend against. The distributed nature of a DDoS attack makes it significantly more powerful and difficult to stop, as traffic comes from numerous sources, often with varying IP addresses.
Related content: Read our guide to DDoS vs DoS attacks.
Botnets
A botnet is a network of compromised computers or devices, often referred to as "zombies," that are controlled remotely by an attacker. These compromised devices are typically infected with malware, allowing the attacker to send commands to the entire network without the owners' knowledge. Botnets are crucial to the execution of DDoS attacks because they can be used to generate the massive amount of traffic required to overwhelm the target's resources.
Botnets are often formed by exploiting vulnerabilities in Internet of Things (IoT) devices, which may include anything from webcams to home routers. These devices are particularly susceptible because they often have weak security features, making them easy targets for attackers.
DDoS as a Service
DDoS as a Service (DDoSaaS) is a business model where cybercriminals offer DDoS attacks as a paid service, making it accessible even to those with little technical expertise. These services are often advertised on dark web forums, where attackers can specify the target, duration, and intensity of the attack they wish to launch. Prices for these services vary depending on the scale of the attack, with some starting as low as a few dollars.
The rise of DDoSaaS has significantly lowered the barrier to entry for launching DDoS attacks. This has led to an increase in the frequency and diversity of attacks, as even unskilled individuals can now launch highly effective DDoS attacks. The availability of these services has made DDoS attacks a more prevalent threat.
DDoS Extortion (RDoS) and Advanced Persistent DoS (APDoS)
Two newer forms of DDoS attacks are DDoS extortion and advanced persistent DoS:
- DDoS extortion, also known as ransom DDoS (RDoS), involves attackers threatening to launch or continue a DDoS attack unless a ransom is paid. This tactic often targets organizations that rely heavily on their online presence, as even a brief disruption can lead to significant financial losses. Attackers usually demand payment in cryptocurrencies, making the transactions difficult to trace. Victims are often given a short deadline to comply before the attack escalates.
- Advanced Persistent DoS (APDoS) is a more sophisticated and sustained form of DDoS attack. Unlike traditional DDoS attacks that may last for a few hours or days, APDoS attacks are prolonged, sometimes stretching over weeks or even months. The attackers continuously change their tactics, making it challenging for the target to defend against the assault. This type of attack often involves multiple attack vectors, including application-layer attacks, volumetric attacks, and protocol attacks. The persistence and adaptability of APDoS can exhaust an organization's resources, making it difficult to maintain normal operations.
Related content: Read our guide to TCP floods.
Distributed Denial-of-Service (DDoS) attacks aren't launched in a vacuum. Perpetrators are driven by a range of motivations, transforming this tactic from a nuisance to a strategic tool. Understanding these motives is crucial for effective defense.
Ideological and Social Causes: Hacktivists, activists, and individuals with strong convictions may launch DDoS attacks to disrupt operations, raise awareness, or silence opposing voices. This can target government agencies, corporations, or organizations perceived as violating ethical principles or societal norms.
Malicious Competition: In the realm of business, DDoS attacks can be used by competitors to disrupt a rival's online presence and gain an unfair advantage. By overwhelming a competitor's servers, they aim to hinder their ability to serve customers and potentially damage their reputation.
Financial Gain: DDoS attacks can be wielded as an extortion tool. Attackers may cripple an organization's online services and demand a ransom in exchange for restoring normalcy. This tactic often preys on businesses heavily reliant on online operations, forcing them into difficult choices.
Purely Destructive Acts: In some cases, DDoS attacks might be motivated by a desire for chaos or disruption. Perpetrators may find amusement in exploiting vulnerabilities and causing havoc, regardless of the specific target or desired outcome.
Personal Grudges and Vendetta: DDoS attacks can be fueled by personal vendettas or disgruntled individuals seeking revenge against an organization or individual. This can manifest in attempts to disrupt online operations, damage reputation, or simply cause inconvenience.
By recognizing the diverse motivations behind DDoS attacks, organizations and individuals can develop more
comprehensive and nuanced defense strategies. This may involve strengthening security protocols, implementing
proactive mitigation measures, and staying informed about emerging threats and attack trends.
Related content: Read our guide to SYN floods.
The best way to detect and identify a DDoS attack is via network traffic monitoring and analysis. Network traffic can be monitored via a firewall or intrusion detection system. An administrator may even set up rules that create an alert upon the detection of an anomalous traffic load and identify the source of the traffic, or drops network packets that meet certain criteria.
The following symptoms could indicate a DoS or DDoS attack:
- Unusually slow network performance
- Unavailability of a particular network service and/or website
- An inability to access any website
- An IP address makes an unusually large number of requests in a limited timespan
- Server responds with a 503-error due to a service outage
- Log analysis indicated a large spike in network traffic
- Odd traffic patterns such as spikes at odd hours of the day or patterns that appear to be unusual
Note: Symptoms of a DoS attack often resemble non-malicious availability issues, such as technical problems with a particular network or a system administrator performing maintenance.
Related content: Read our guide to UDP floods.
Growth and diversity of attacks
According to Radware’s 2024 Global Threat Analysis Report, DDoS attacks are evolving, with hackers adapting their strategies to counteract mitigation techniques:
- In 2023, the number of DDoS attacks per customer grew by 94% compared to 2022, after the previous year’s growth of 99%.
- Attack volume increased 48% in 2023 compared to 2022. In 2023, we observed 63% more attacks with traffic below 1Gbps, 177% more attacks peaking between 100Gbps and 250Gbps, and an increase of 150% in large attacks peaking above 500Gbps.
- The number of attacks per customer has grown from 106 attacks per month or 3.48 attacks per day in 2021 to an average of 49 attacks per day in 2023.
- The Americas were targeted by almost half of all global DDoS attacks. The EMEA region, accounting for 39% of the DDoS attacks, had to mitigate 65% of the global DDoS attack volume. The APAC region accounted for almost 12% of global DDoS attacks.
Related content: Read our guide to ICMP flood.
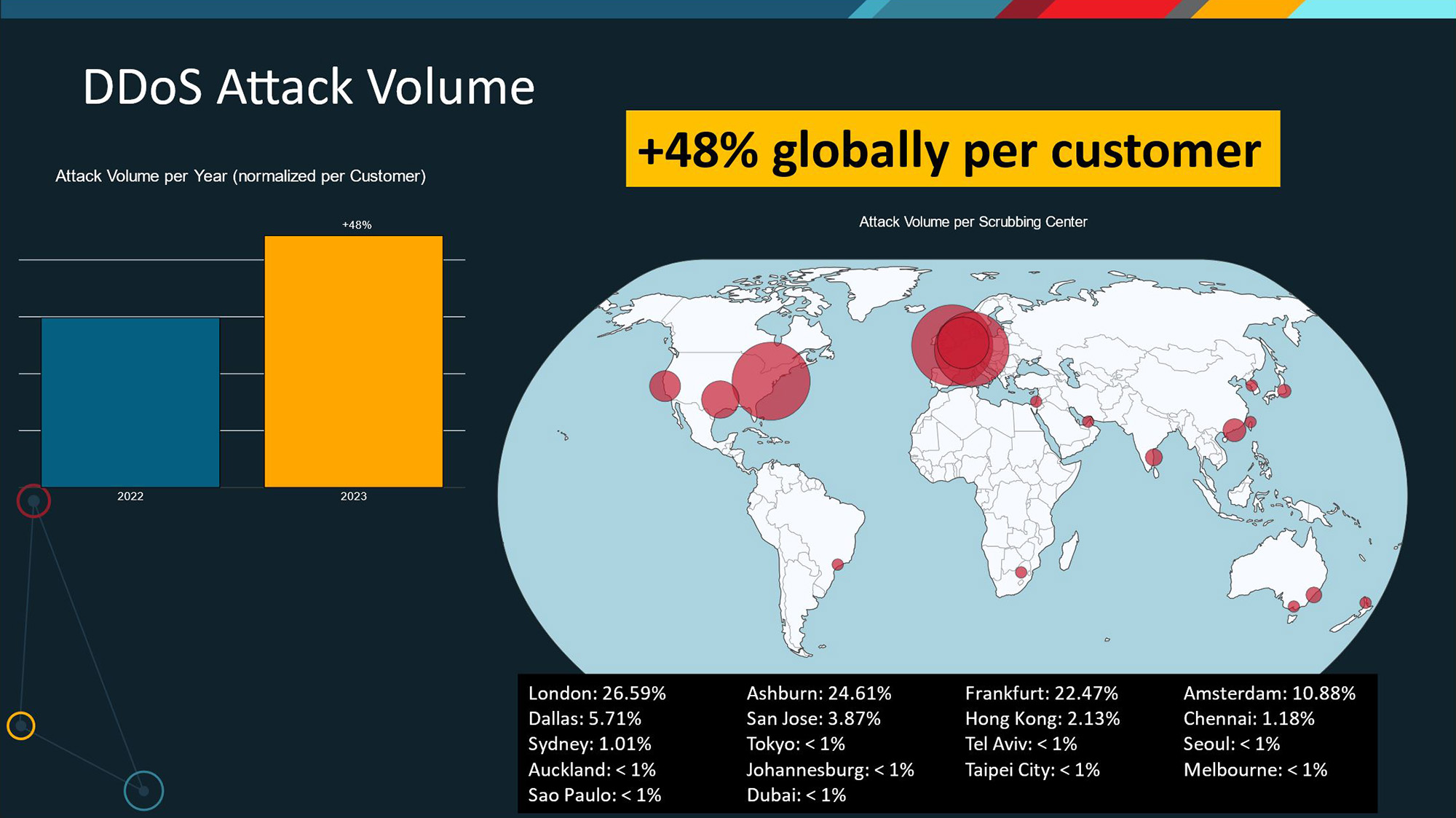
Figure 2: Increase in DDoS Attacks on Organizations in 2023
Cost of DDoS attacks
According to Radware’s 2023 report Application Security in a Multi-Cloud World:
- 31% of organizations face DDoS attacks weekly.
- Downtime due to a successful application DDoS attack costs organizations an average of $6,130 per minute. For instance, if an attack lasts for an hour, the cost could potentially escalate to over $367,800.
Future trends and predictions
Here are some of the most important trends affecting DDoS attacks, according to Radware’s 2023 DDoS Report:
- Emergence of “Mega-Attacks”: The growing number of connected devices, the widespread adoption of IPv6, and the increasing availability of powerful botnets could facilitate the launch of larger and more complex attacks with the potential to cripple critical infrastructure and online services.
- Machine Learning (ML): ML algorithms offer real-time identification and mitigation of malicious traffic, adapting to novel attack patterns. For instance, Radware’s DefensePro leverages ML-powered anomaly detection for proactive attack mitigation.
- Targeted Attacks on Critical Infrastructure: Critical infrastructure, such as power grids, financial institutions, and healthcare providers, may become more susceptible to targeted DDoS attacks aimed at causing widespread disruption and potentially jeopardizing public safety.
- Ransomware Attacks: DDoS attacks can be used to disrupt operations and pressure organizations into paying ransom demands.
- AI-powered Attacks: Attackers may leverage artificial intelligence (AI) to automate and personalize attacks, making them more challenging to detect and mitigate. AI could be used to identify and exploit vulnerabilities in an organization’s defenses, Launch coordinated attacks that adapt to ongoing mitigation efforts, and generate highly targeted phishing and social engineering attacks.
- Increased Geopolitical Implications: In a world rife with geopolitical tensions, DDoS attacks may be used as tools of cyberwarfare, aimed at disrupting rival nations’ infrastructure, or influencing public opinion.
The Main Types of DDoS Attacks
Application Layer (Layer-7) DDoS Attacks
Application Layer DDoS attacks specifically target the application layer of networked services.
Unlike traditional network-based attacks that flood network resources, these attacks exploit vulnerabilities in
application protocols such as HTTP, HTTPS, SMTP, FTP, and VOIP. Their goal is to exhaust the resources of the targeted
application, rendering it inaccessible or unresponsive to legitimate users.
Application Layer DDoS attacks exhibit diverse characteristics:
HTTP Floods: Attackers flood web
servers with a massive number of HTTP requests. These requests overload the server’s processing capacity,
leading to service disruption.
HTTPS Attacks: Similar to HTTP floods, but with encrypted traffic. Attackers exploit SSL/TLS
handshakes, consuming server resources during connection setup.
SMTP and Email Attacks: By bombarding email servers with excessive requests, attackers disrupt
email communication and overload mail servers.
FTP Attacks: Attackers overwhelm File Transfer Protocol (FTP) servers, hindering file transfers
and access.
VOIP Attacks: Targeting Voice over IP (VOIP) services, these attacks flood SIP (Session
Initiation Protocol) servers, causing call drops and service degradation.
Application Layer DDoS attacks come in various flavors:
“Low and Slow” Attacks: These are more subtle. Attackers send requests at a slow
pace, avoiding detection thresholds. For example:
- Slowloris:
Opens multiple connections to a web server and sends partial HTTP requests, keeping connections open
indefinitely.
- R-U-Dead-Yet (RUDY): Sends slow POST requests to exhaust server resources.
Flood Attacks: High-volume requests flood the application, saturating its resources. These can
be HTTP floods, HTTPS floods, or other protocol-specific floods.
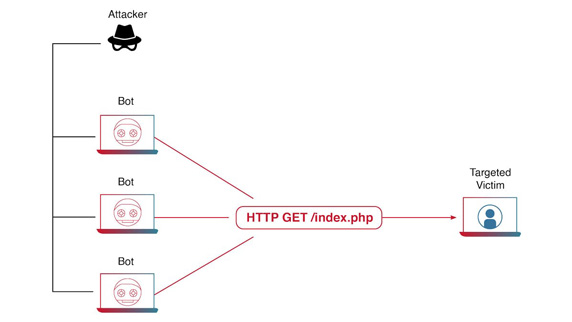
Figure 3: How a Layer-7 Application DDoS Attack
What is a Layer 7 DDoS Attack? | A Radware Minute
Volumetric or Volume-Based Attacks
Volumetric DDoS attacks have been a persistent threat in the cybersecurity landscape. These attacks aim to
overwhelm a network’s bandwidth, causing disruptions in availability and accessibility. The evolution
of these attacks has been influenced by various geopolitical events and advancements in technology, including the
advent of Reflection/Amplification attacks.
Volumetric DDoS attacks are characterized by several key features:
High Traffic Volume: These attacks generate an enormous amount of traffic, saturating the
bandwidth of the targeted network.
IP Spoofing: Attackers often use IP spoofing to mask the source of the attack traffic, making it
difficult to block and trace back.
Use of Botnets: Attackers often leverage botnets - networks of compromised devices - to generate
the massive traffic volume required for these attacks.
Protocol Exploitation: Common network protocols such as NTP, DNS, and SSDP are exploited to
amplify the attack traffic.
Related content: Read our guide to DNS DDoS attacks.
Reflection/Amplification Attacks: In these attacks, the attacker spoofs the victim’s IP
address and sends a request to a third-party server that will send a large response. This amplifies the amount of
traffic directed at the victim, overwhelming their resources.
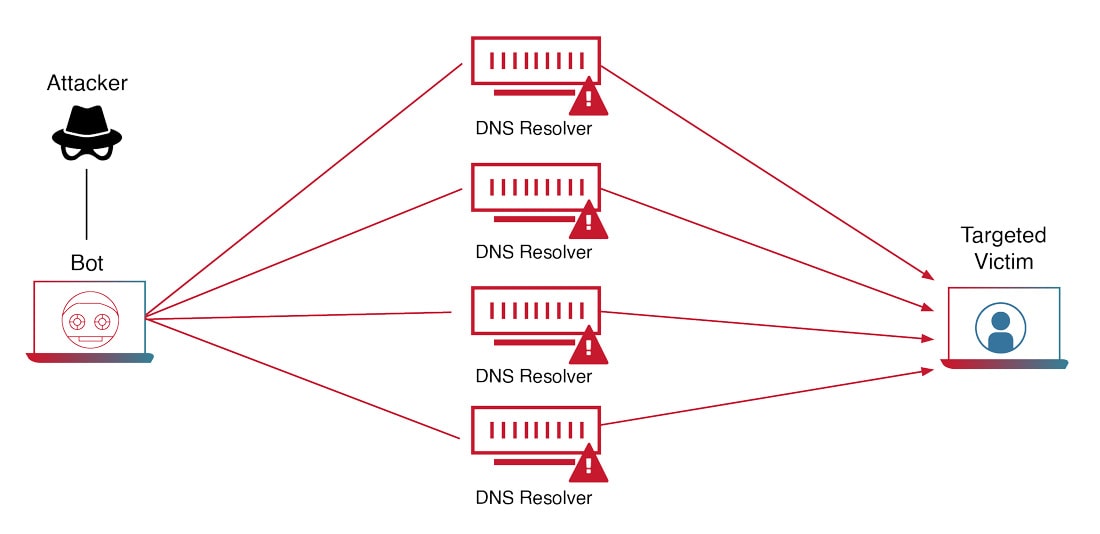
Figure 4: How a Volumetric DDoS Attack Works
Web DDoS Tsunami Attack
Web DDoS tsunami attacks represent a new
breed of cyber threat that emerged during the heightened era of hacktivist activity triggered by Russia’s
invasion of Ukraine in February 2022. Initially, these attacks began as high-volume network-based Flood attacks.
However, they swiftly evolved into more sophisticated multi-vector application-level assaults that pose significant
challenges for detection and mitigation.
These attacks are characterized by several key features:
High Request Volume: Web DDoS Tsunami attacks generate an exceptionally high number of requests
per second (RPS), overwhelming targeted servers and infrastructure.
Encryption: Attack traffic is often encrypted, making it difficult to discern malicious requests
from legitimate ones.
Application-Level Attack Methods: These include HTTPS Get, Push, and Post request attacks with
dynamic parameters behind proxies. Each request appears innocuous, making timely detection challenging.
Sophisticated Evasion Techniques:
- Randomized Headers: Attackers manipulate HTTP methods, headers, and cookies,
making their requests appear legitimate.
- IP Spoofing: They spoof IP addresses, complicating attribution and filtering.
- Impersonation of Third-Party Services: Attackers mimic popular embedded
third-party services, further camouflaging their intent.
Continuous Morphing: Web DDoS Tsunami attacks continuously evolve, altering their patterns and
characteristics. This dynamic behavior prolongs the attack duration and exacerbates downtime.
Learn more in our detailed guide to Web DDoS attacks.
Mitigation Challenges
- Resource Exhaustion: These attacks drain server memory, CPU, and bandwidth.
- Service Disruption: Critical services like web apps, email, and VOIP become unusable.
- Mitigation Complexity: Require specialized defenses that inspect application-level traffic.
- Complex Attribution: Spoofed IP addresses and botnets make identifying the true source of these attacks challenging.
The following case studies highlight the potential scale and impact of DDoS attacks, demonstrating the importance of
effective mitigation strategies and the need for ongoing vigilance in the face of evolving threats.
Attack on LCK Spring 2024 (February 2024): Recent matches in the LCK Spring 2024 season faced
disruptions caused by persistent ping issues attributed to DDoS attacks. These disruptions led to prolonged
technical pauses, impacting players and fans, both online and on-site.
Attack on AWS (February 2020): Amazon Web Services (AWS) reported mitigating a massive DDoS
attack that saw incoming traffic at a rate of 2.3 terabits per second (Tbps). The attackers responsible used
hijacked Connection-less Lightweight Directory Access Protocol (CLDAP) web servers. AWS did not disclose which
customer was targeted by the attack.
Attack on Google (September 2017): This attack is considered the largest DDoS attack to date,
reaching a size of 2.54 Tbps. The attackers sent spoofed packets to 180,000 web servers, which in turn sent
responses to Google. This was not an isolated incident as the attackers had directed multiple DDoS attacks at
Google’s infrastructure over the previous six months.
Attack on Occupy Central, Hong Kong (2014): This attack targeted the Occupy Central movement in
Hong Kong. The movement’s websites were hit with a massive DDoS attack, disrupting their online presence and
communication.
Attack on Overwatch 2 (February 2024): The popular online multiplayer game Overwatch 2 was hit
with a major DDoS attack. The attack caused major issues for players, disrupting gameplay and causing widespread
frustration.
Attack on GitHub (February 2018): This attack reached 1.3 Tbps, sending packets at a rate of
126.9 million per second. The GitHub attack was a memcached DDoS attack, so there were no botnets involved.
Instead, the attackers leveraged the amplification effect of a popular database caching system known as memcached.
By flooding memcached servers with spoofed requests, the attackers were able to amplify their attack by a
magnitude of about 50,000 times.
Attack on Dyn (October 2016): This massive DDoS attack was directed at Dyn, a major DNS
provider. The attack created disruption for many major sites, including Airbnb, Netflix, PayPal, Visa, Amazon, The
New York Times, Reddit, and GitHub. This was done using malware called Mirai, which creates a botnet out of
compromised Internet of Things (IoT) devices such as cameras, smart TVs, radios, printers, and even baby monitors.
The following capabilities are critical to preventing DDoS attacks:
Traffic Differentiation
Traffic differentiation allows organizations to distinguish between legitimate user traffic and malicious traffic generated by attackers. This involves analyzing traffic patterns, such as IP addresses, geographic origins, and behavior over time, to identify anomalies. Advanced DDoS mitigation tools use machine learning and real-time analytics to improve the accuracy of traffic differentiation, reducing the likelihood of false positives that could block genuine users.
Firewalls and Web Application Firewalls (WAF)
Traditional firewalls monitor and filter incoming and outgoing traffic based on predefined security rules, helping to block malicious traffic at the network level. WAFs are specifically designed to protect web applications by filtering and monitoring HTTP requests. They can block malicious traffic targeting application vulnerabilities, such as SQL injection or cross-site scripting (XSS), and are particularly effective against application-layer DDoS attacks.
Cloud, On-Premises, and Hybrid Deployment
Flexibility of deployment models is crucial so an organization can tailor its DDoS mitigation service to suit its needs, budget, network topology and threat profile. The appropriate deployment model—hybrid, on-demand or always-on cloud protection—will vary based on network topology, application hosting environments and sensitivity to delays and latency.
Scrubbing Capacity and Global Network
DDoS attacks are increasing in quantity, severity, complexity, and persistence. If faced with large volumetric or simultaneous assaults, cloud DDoS services should provide a robust, global security network that scales with several Tbps worth of mitigation capacity with dedicated scrubbing centers segregating clean traffic from DDoS attack traffic.
Fully Automated Protection
With today’s dynamic and automated DDoS attacks, organizations do not want to rely on manual protection. A service that does not require any customer intervention with a fully automated attack lifecycle—data collection, attack detection, traffic diversion and attack mitigation—ensures better quality protection.
Behavioral-Based Protection
A DDoS mitigation solution that blocks attacks without impacting legitimate traffic is key. Solutions that leverage machine-learning and behavioral-based algorithms to understand what constitutes legitimate behavior and automatically blocks malicious attacks are critical. This increases protection accuracy and minimizes false positives.
Protection Against All Attack Vectors
Comprehensive DDoS protection requires defenses that cover all potential attack vectors, including volumetric attacks, protocol attacks, and application-layer attacks. A robust DDoS mitigation solution should integrate multiple technologies, such as traffic analysis, anomaly detection, scrubbing services, and behavioral protection, to provide a layered defense. This approach ensures that regardless of the attack type or method, the defense mechanisms are able to neutralize the threat without impacting legitimate traffic.
CDN-Based Protection
Content Delivery Networks (CDNs) play a vital role in mitigating DDoS attacks by distributing content across multiple servers worldwide. When a DDoS attack occurs, the CDN can absorb and diffuse the traffic across its global network, preventing the attack from overwhelming a single server. Additionally, CDNs often include built-in security features that can detect and mitigate DDoS traffic.
Here are five steps to follow when your organization detects a DDoS attack.
Step 1: Alert Key Stakeholders
Alert key stakeholders within the organization of the attack and steps that are being taken to mitigate it. Examples of key stakeholders include the CISO, security operations center (SoC), IT director, operations managers, business managers of affected services, etc. Keep the alert concise but informative.
Key information should include:
- What is occurring
- When the attack started
- What steps are being taken to mitigate the attack
- Impact to users and customers
- Which assets (applications, services, servers, etc.) are being impacted
Step 2: Notify Your Security Provider
You will also want to alert your security provider and initiate steps on their end to help mitigate the attack. Your security provider could be your internet service provider (ISP), web hosting provider or a dedicated security service. Each vendor type has different capabilities and scope of service. Your ISP might help you minimize the amount of malicious network traffic reaching your network, whereas your web hosting provider might help you minimize application impact and scale your service accordingly.
Likewise, security services will usually have dedicated tools for dealing with DDoS attacks. Even if you don’t already have a predefined agreement for service, or are not subscribed to their DDoS protection offering, you should nonetheless reach out to them to see how they can assist.
Step 3: Activate Countermeasures
If you already have anti-DDoS countermeasures in place, activate them. Ideally, these countermeasures will initiate immediately when an attack is detected. However, in some cases, certain tools, such as out-of-path hardware devices or manually activated, on-demand mitigation services, might require the customer to initiate them manually.
One approach is to implement IP-based access Control lists (ACLs) to block all traffic coming from attack sources. This is accomplished at the network router level and can usually be accomplished by either your network team or your ISP. This is a useful approach if the attack is coming from a single source or a small number of attack sources. However, if the attack is coming from a large pool of IP address, this approach might not help.
If the target of the attack is an application- or a web-based service, you could limit the number of concurrent application connections. This approach is known as rate-limiting and is frequently the favored approach by web hosting providers and CDNs. Note that this approach is prone to high degrees of false positives because it cannot distinguish between malicious and legitimate user traffic. Dedicated DDoS protection tools will give you the widest coverage against DDoS attacks. DDoS protection measures can be deployed either as an appliance in your data center, as a cloud-based scrubbing service, or as a hybrid solution combining a hardware device and a cloud service.
Step 4: Monitor Attack Progression
Throughout the attack, monitor the progression of the attack to see how it develops. This should include:
- What type of DDoS attack is it? Is it a network-level flood or an application-layer attack?
- Is the attack coming from a single IP source or multiple sources? Can you identify them?
- Are the targets of the attack staying the same or are attackers changing their targets over time?
- What are the attack characteristics? How large is the attack, both in terms of bits-per-second and of packets-per-second?
- How does the attack pattern look like? Is it a single sustained flood or is it a burst attack? Does it involve a single protocol, or does it involve multiple attack vectors?
Tracking attack progression will also help you tune your defenses to stop it.
Step 5: Assess Defense Performance
Finally, as the attack develops and countermeasures are activated, assess their effectiveness. Your security vendor should provide a service level agreement document which commits their service obligations. Ensure they’re meeting their SLAs and whether there is an impact to your operations. If they’re not, or not able to stop the attack whatsoever, now is the time to assess whether you need to make an emergency change to your service.
Legal Considerations
DDoS attacks are considered illegal in most countries and can lead to severe penalties.
Criminal Charges: DDoS attacks are illegal, and the attacker may face criminal charges. For
instance, under the Computer Misuse Act 1990 in the UK, individuals involved in DDoS attacks face up to 10 years
in prison. In the United States, individuals participating in DDoS attacks risk being charged with legal offenses
at the federal level, both criminally and civilly.
Liability: If a DDoS attack causes harm to an individual or a business, the attacker can be held
liable for the damages.
Violation of Terms of Service: DDoS attacks violate the terms of service of most internet
service providers and websites.
Ethical Considerations
While DDoS attacks are generally viewed as malicious activities, some argue that they can serve a noble purpose by
taking down harmful websites. However, this perspective is fraught with moral dilemmas and potential legal battles.
Potential for Abuse: Despite these arguments, DDoS attacks have the potential to be abused and
can cause significant harm. They can disrupt services, cause financial loss, and infringe on people’s rights
to access information. Therefore, even if they are used with good intentions, DDoS attacks can have negative
consequences.
Civil Disobedience: Some proponents of DDoS attacks argue that they can be seen as a form of
civil disobedience or online protest. In this view, DDoS attacks are akin to sit-ins or other forms of peaceful
protest, used to draw attention to an issue or cause.
Ethical Hacking: Ethical hacking, also known as “white hat” hacking, involves using
hacking skills to identify and fix vulnerabilities in systems. Ethical hackers can play a crucial role in
preventing DDoS attacks by identifying potential weaknesses that could be exploited and helping organizations
strengthen their defenses.
In conclusion, while DDoS attacks are generally considered
illegal and unethical, there are complex legal and ethical issues surrounding their use. It’s crucial for
individuals and organizations to understand these aspects and navigate them carefully.
See Additional Guides on Key Hacking Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of hacking.